The latest BSOD was bugcheck 50 and was caused by an older Nvidia GPU driver.
Some of the Live kernel event bugchecks seen in the logs were:
117 Bug Check 0x117: VIDEO_TDR_TIMEOUT_DETECTED
141 Bug Check 0x141: VIDEO_ENGINE_TIMEOUT_DETECTED
193 Bug Check 0x193: VIDEO_DXGKRNL_LIVEDUMP
With multiple BSOD and different driver versions for Nvidia GPU driver nvlddmkm.sys it is important to identify any malfunctioning hardware before the warranty expires.
Contact Lenovo now to report recurrent BSOD with Windows 11.
This includes multiple BSOD caused by different versions of Nvidia GPU drivers.
This typically is caused by malfunctioning GPU.
It can also be caused by a malfunctioning motherboard however there is no option for the computer user to swap test the GPU in a laptop.
If Lenovo accepts the multiple recurrent BSOD as malfunctioning hardware then request a Return Merchandise Authorization (RMA).
If Lenovo insists on additional testing the continue with the steps later in this thread.
Windows 11 backup images can be made and restored so that the laptop can be tested with Windows 10.
If possible, plan to use Windows 10 for a week and after testing restore a Windows 11 image.
The testing of the Nvidia GPU drivers and hardware can be repeated by upgrading to Windows 11.
Once testing has completed a backed up Windows 11 image can be restored.
If there are BSOD related to Nvidia GPU with both Windows 11 and Windows 10 then this confirms malfunctioning hardware.
If Lenovo does not require a clean install of either Windows 11 or Windows 10 for testing and authorizes a RMA then you can skip all further testing.
1) Turn off WDV
2) Make free backup images using Macrium and save the images to another disk drive or the cloud
https://www.tenforums.com/tutorials/61026-backup-restore-macrium-reflect.html
3) Find a flash drive that you can format ( > or = 8 GB)
4) Create a bootable Windows 10 iso
https://www.tenforums.com/tutorials/2376-create-bootable-usb-flash-drive-install-windows-10-a.html
https://www.tenforums.com/tutorials/9230-download-windows-10-iso-file.html
https://www.microsoft.com/en-us/software-download/windows10
3) Clean install Windows 10
https://www.tenforums.com/tutorials/1950-clean-install-windows-10-a.html
Do not install any drivers at this time.
Later, plan to install drivers from the Nvidia website during the testing
4) Restart WDV
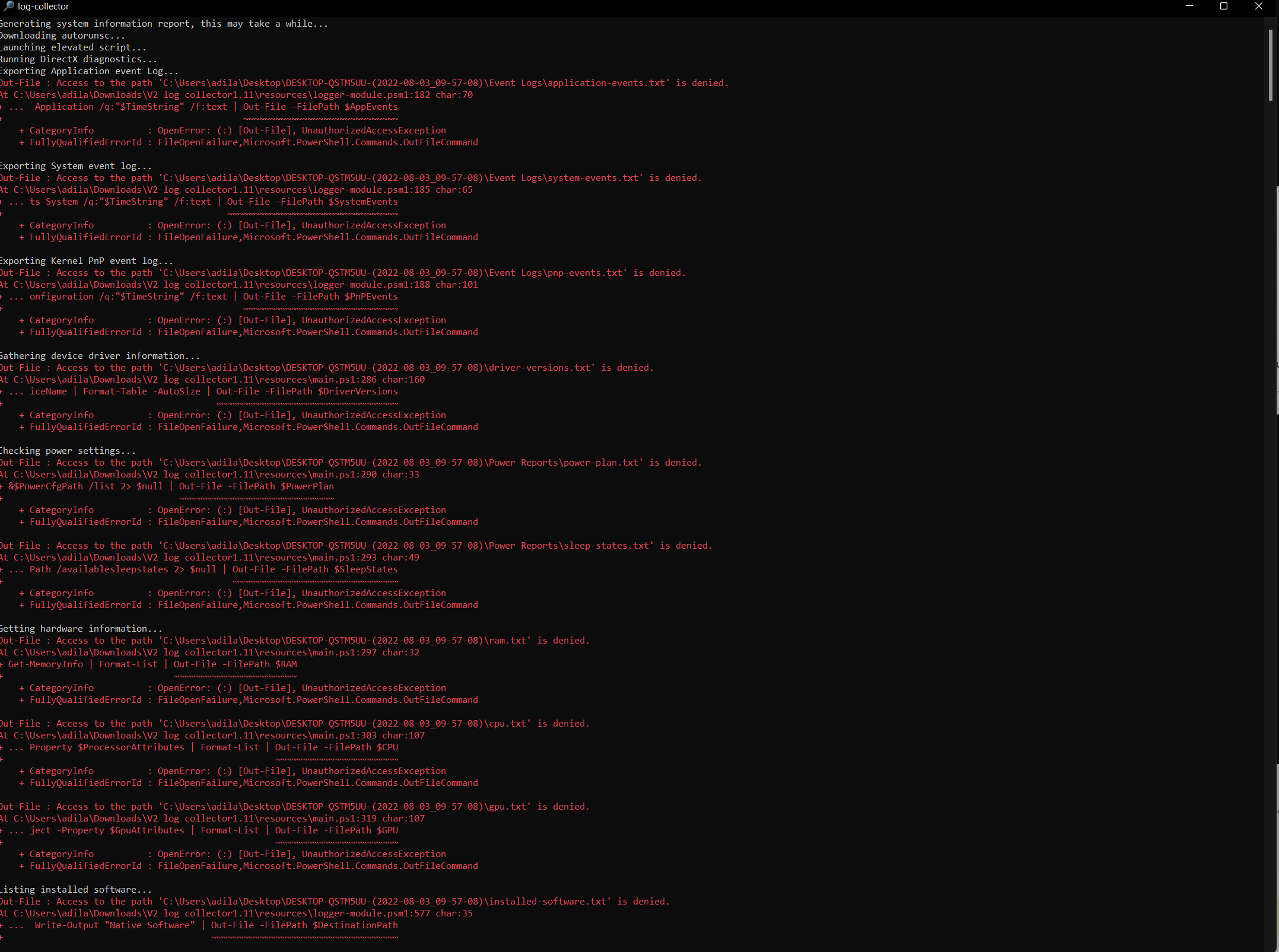
5) If there is no BSOD then post a new querysettings into the newest post
6) For any BSOD
a) Post a new V2 share link into the newest post
b) Post a new compressed memory dump share link into the newest post (separate share link)
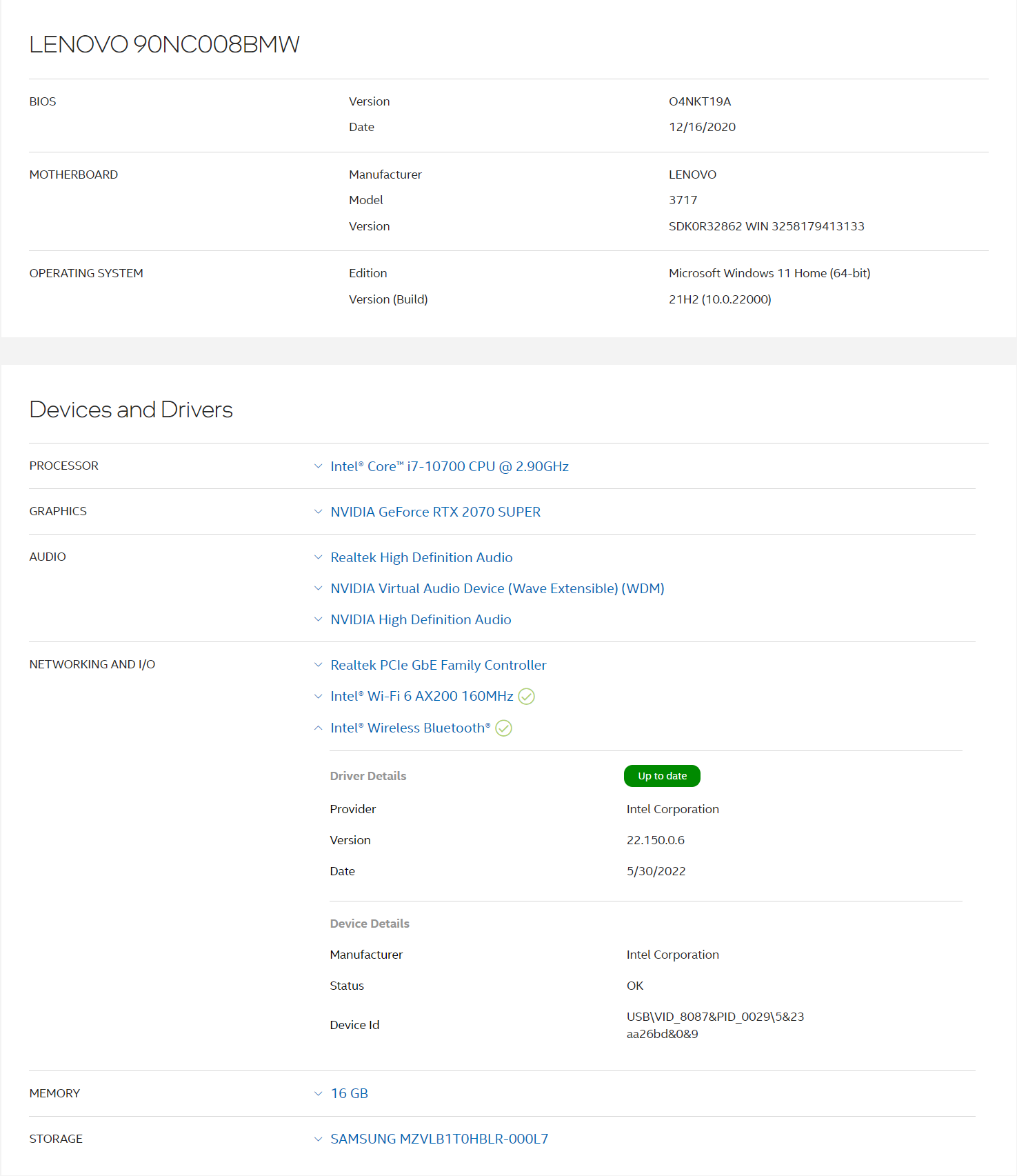
Name NVIDIA GeForce RTX 2070 SUPER
PNP Device ID PCI\VEN_10DE&DEV_1E84&SUBSYS_C72B1462&REV_A1\4&3292EEB7&0&0008
Adapter Type GeForce RTX 2070 SUPER, NVIDIA compatible
Adapter Description NVIDIA GeForce RTX 2070 SUPER
Adapter RAM (1 048 576) bytes
Installed Drivers C:\WINDOWS\System32\DriverStore\FileRepository\nvle.inf_amd64_c4410ab03e8e99d7\nvldumdx.dll,C:\WINDOWS\System32\DriverStore\FileRepository\nvle.inf_amd64_c4410ab03e8e99d7\nvldumdx.dll,C:\WINDOWS\System32\DriverStore\FileRepository\nvle.inf_amd64_c4410ab03e8e99d7\nvldumdx.dll,C:\WINDOWS\System32\DriverStore\FileRepository\nvle.inf_amd64_c4410ab03e8e99d7\nvldumdx.dll
Driver Version 27.21.14.5785
INF File oem18.inf (Section021 section)
Driver C:\WINDOWS\SYSTEM32\DRIVERSTORE\FILEREPOSITORY\NVLE.INF_AMD64_C4410AB03E8E99D7\NVLDDMKM.SYS (27.21.14.5785, 31,53 MB (33 056 416 bytes), 2022-08-06 14:10)
.
.
.
.
.
Please remember to vote and to mark the replies as answers if they help.
On the bottom of each post there is:
Propose as answer = answered the question
On the left side of each post there is /\ with a number: click = a helpful post
.
.
.
.
.