Hi @Tom ,
Thank you for reaching out to Microsoft Q&A for this question.
The Policy evaluation for "resource creation" is based on the ARM template submitted during deployment (either through portal, cli, PowerShell etc.) and not based on the exported template after the resource has been created. Generally, they are similar but in case of FunctionApp and App Service, they appear to be a bit different for the specific properties being targeted in the Policy definition.
edited - 08/09/2022
Note that the actual field name of resource and corresponding property alias (which is used in Azure policy definition) can be different. Please refer to this link for more details - Aliases in Azure Policy Definition. Considering that, you should be using the following available property aliases, depending on the requirement (this is case sensitive).
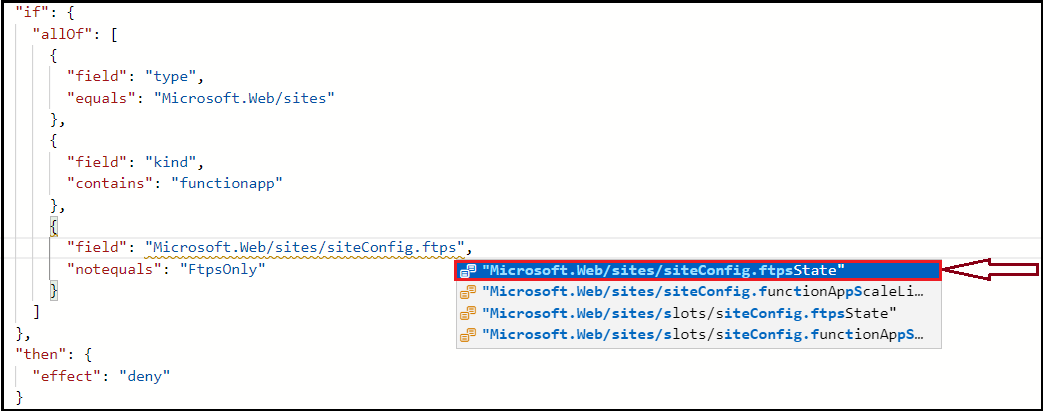
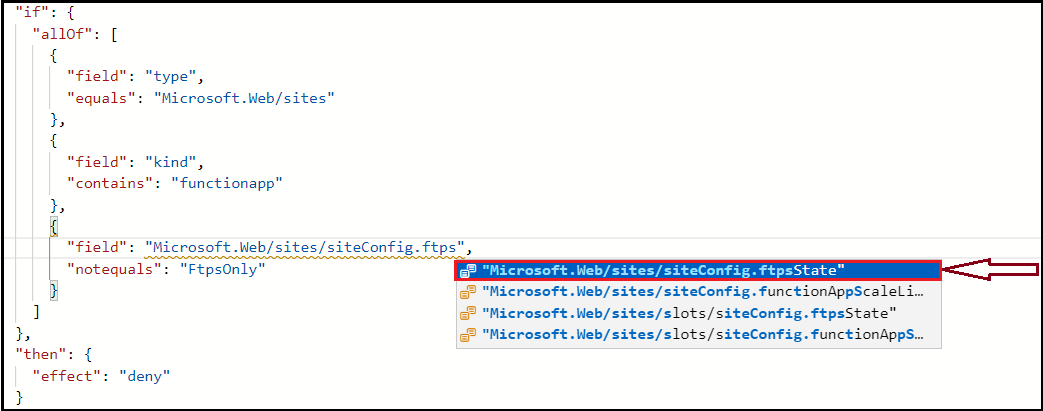
I tested a sample policy using the "field": "Microsoft.Web/sites/siteConfig.ftpsState", and it worked as expected (see the screenshot above for details).
There are a number of ways to get the correct property alias for resource and 2 of them are mentioned here.
One of the other ways is to get it from Azure Portal when defining the Policy as shown in the screenshot above (use ctrl+space to get the hints loaded).
Similarly, for Azure App Service, the template generated from Portal does not have "Kind" set and is empty when submitting for deployment. This field seems to be getting set after the resource creation, hence the condition fails here too. Please remove this condition and test.
You may also see details available here for more understanding of how the policy is evaluated and scenarios where it might not work - Azure/azure-policy
Please let me know if you have any questions.
---
Please 'Accept as answer' and ‘Upvote’ if it helped so that it can help others in the community looking for help on similar topics.