Create and customize Microsoft Sentinel playbooks from content templates
A playbook template is a prebuilt, tested, and ready-to-use workflow that can be customized to meet your needs. Templates can also serve as a reference for best practices when developing playbooks from scratch, or as inspiration for new automation scenarios.
Playbook templates aren't active playbooks themselves, until you create a playbook (an editable copy of the template) from them.
Many playbook templates are developed by the Microsoft Sentinel community, independent software vendors (ISVs), and Microsoft's own experts, based on popular automation scenarios used by security operations centers around the world.
Get playbook templates from the following sources:
On the Automation page, the Playbook templates tab lists the playbook templates installed. Multiple active playbooks can be created from the same template.
When a new version of the template is published, the active playbooks created from that template show in the Active playbooks tab that an update is available.
Playbook templates are available as part of product solutions or standalone content that you install from the content hub in Microsoft Sentinel. For more information, see Microsoft Sentinel content and solutions and Discover and manage Microsoft Sentinel out-of-the-box content.
The Microsoft Sentinel GitHub repository contains many playbook templates. They can be deployed to an Azure subscription by selecting the Deploy to Azure button.
Technically, a playbook template is an Azure Resource Manager (ARM) template which consists of several resources: an Azure Logic Apps workflow and API connections for each connection involved.
This article focuses on deploying a playbook template from the Playbook templates tab under Automation.
This article helps you understand how to:
- Explore out-of-the-box playbook templates
- Deploy a playbook template
Important
Playbook templates are currently in PREVIEW. See the Supplemental Terms of Use for Microsoft Azure Previews for additional legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
Microsoft Sentinel is available as part of the public preview for the unified security operations platform in the Microsoft Defender portal. For more information, see Microsoft Sentinel in the Microsoft Defender portal.
Explore playbook templates
For Microsoft Sentinel in the Azure portal, select the Content management > Content hub page. For Microsoft Sentinel in the Defender portal, select Microsoft Sentinel > Content management > Content hub.
On the Content hub page, select Content type to filter for Playbook. This filtered view lists all the solutions and standalone content that include one or more playbook templates. Install the solution or standalone content to get the template.
Then, select Configuration > Automation > Playbook templates tab to view the installed templates.
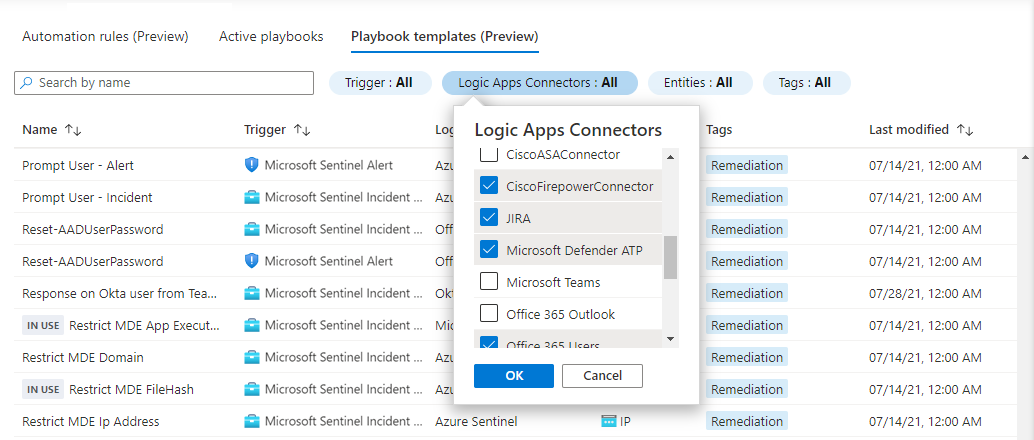
To find a playbook template that fits your requirements, you can filter the list by the following criteria:
Trigger indicates whether the playbook is triggered by incident creation, by incident update, or by alert creation. Learn more
Logic Apps connectors shows the external services this playbook interacts with. During the deployment process, each connector needs to assume an identity to authenticate to the external service.
Entities shows the entity types explicitly filtered and parsed by a playbook that expects to find those entity types in the incident. For example, a playbook that tells a firewall to block an IP address expects to operate on incidents created by analytics rules that generate alerts containing IP addresses, such as a Brute Force attack detection rule.
Tags show labels applied to the playbook to relate it to a specific scenario, or to indicate a special characteristic.
Examples:
Enrichment - The playbook fetches information from another service to add information to an incident. This information is usually added as a comment to the incident or sent to the SOC.
Remediation - The playbook takes an action on the affected entities to eliminate a potential threat.
Sync - The playbook helps to keep an external service, such as an incident management service, updated with the incident's properties.
Notification - The playbook sends an email or message.
Response from Teams - The playbook allows the analysts to take a manual action from Teams using interactive cards.
Customize a playbook from a template
This procedure describes how to deploy playbook templates.
You can repeat this process to create multiple playbooks on the same template.
Select a playbook name from the Playbook templates tab.
If the playbook has any prerequisites, make sure to follow the instructions.
Some playbooks call other playbooks as actions. This second playbook is referred to as a nested playbook. In such a case, one of the prerequisites is to first deploy the nested playbook.
Some playbooks require deploying a custom Logic Apps connector or an Azure Function. In such cases, there is a Deploy to Azure link that takes you to the general ARM template deployment process.
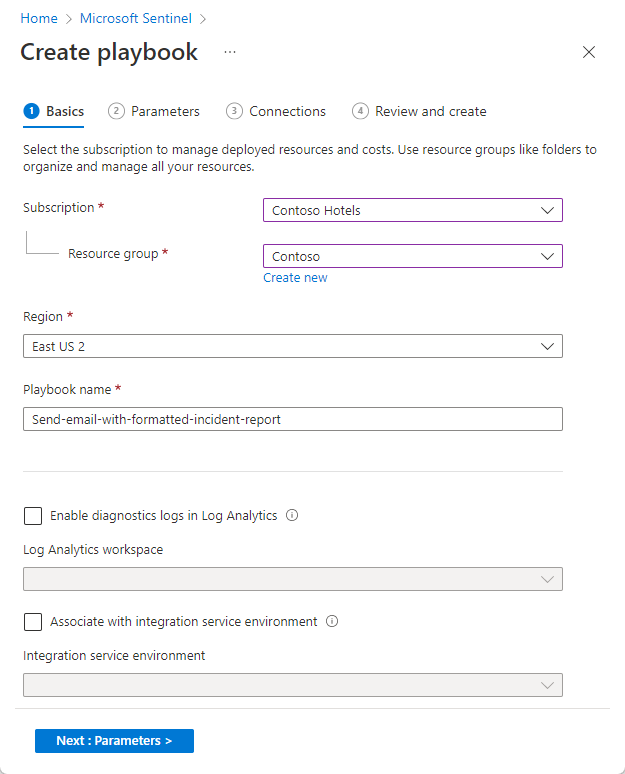
Select Create playbook to open the playbook creation wizard based on the selected template. The wizard has four tabs:
Basics: Locate your new playbook (Logic Apps resource) and give it a name (can use default).
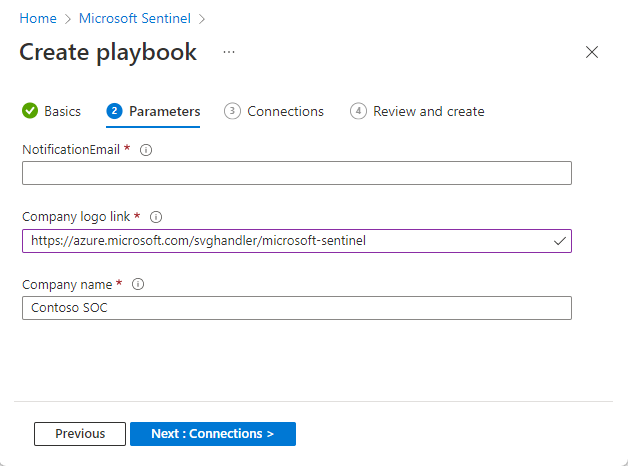
Parameters: Enter customer-specific values that the playbook uses. For example, if this playbook sends an email to the SOC, you can define the recipient address here. This tab is shown only if the playbook has parameters.
Note
If this playbook has a custom connector in use, it should be deployed in the same resource group, and you will be able to insert its name in this tab.
Connections: Expand each action to see the existing connections you created for previous playbooks. Learn more about creating connections for playbooks.
Note
For custom connectors, connections will be displayed by the name of the custom connector entered in the Parameters tab.
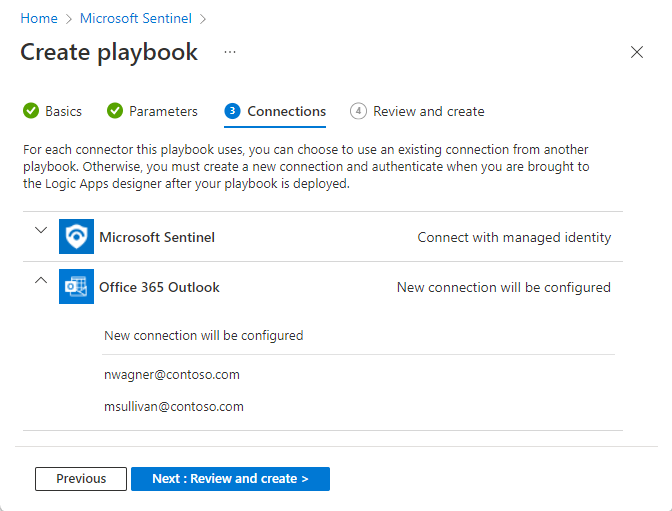
If there aren't any, or if you want to create new ones, choose Create new connection after deployment. This option takes you to the Logic Apps designer after the deployment process is completed.
For connectors that support connecting with managed identity, such as Microsoft Sentinel, this is the connection method selected by default.
Review and Create: View a summary of the process and await validation of your input before creating the playbook.
After following the steps in the playbook creation wizard to the end, you're taken to the new playbook's workflow design in the Logic Apps designer.
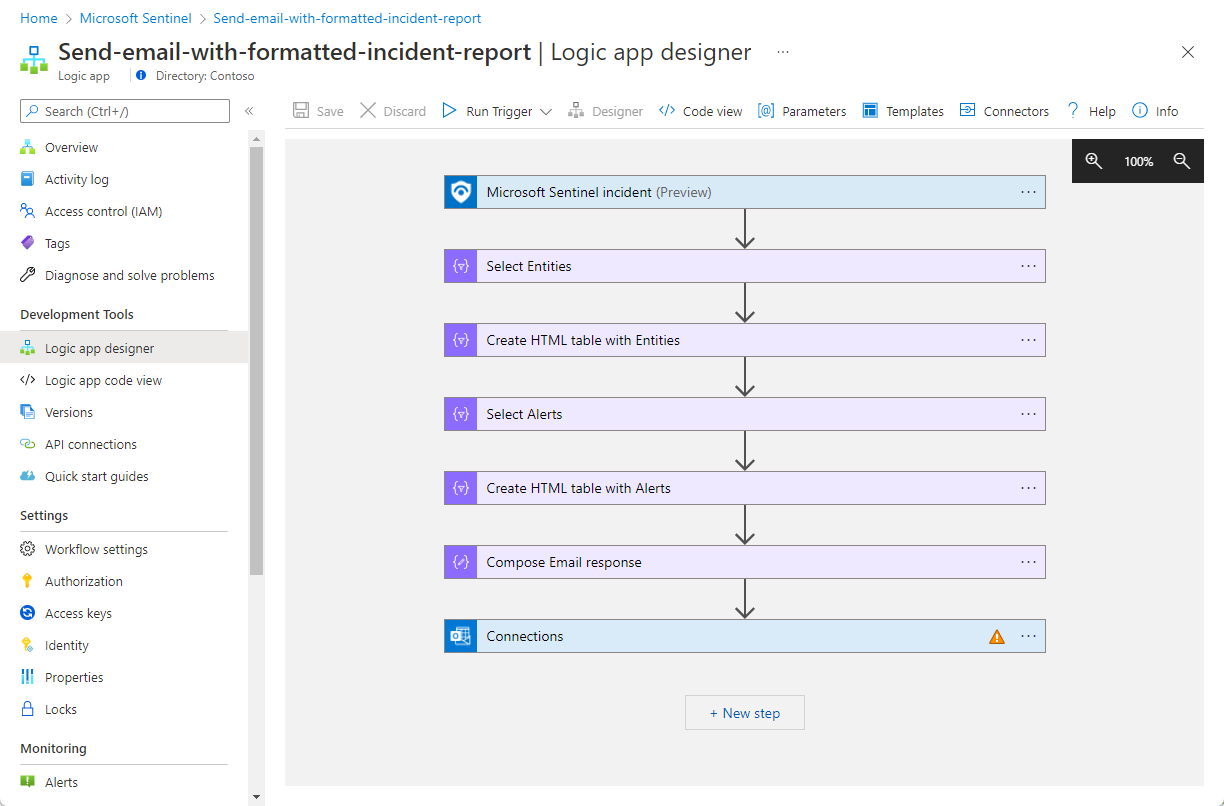
For each connector you chose to create a new connection for after deployment:
From the navigation menu, select API connections.
Select the connection name.
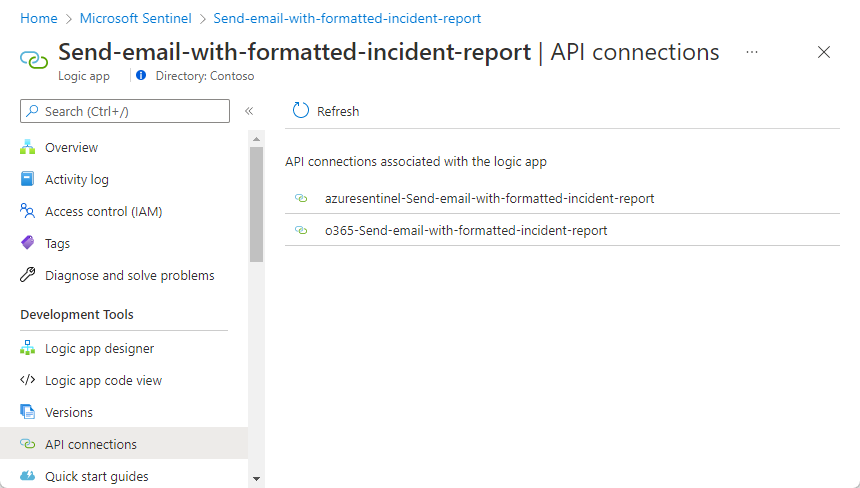
Select Edit API connection from the navigation menu.
Fill in the required parameters and select Save.

Alternatively, you can create a new connection from within the relevant steps in the Logic Apps designer:
For each step that appears with an error sign, select it to expand.
Select Add new.
Authenticate according to the relevant instructions.
If there are other steps using this same connector, expand their boxes. From the list of connections that appears, select the connection you just created.
If you have chosen to use a managed identity connection for Microsoft Sentinel (or for other supported connections), grant permissions to the new playbook on the Microsoft Sentinel workspace (or on the relevant target resources for other connectors).
Save the playbook. You'll now be able to see it in the Active Playbooks tab.
To run this playbook, set an automated response or run manually.
Most of the templates can be used as is, but we recommend making any adjustments required to fit the new playbook to your SOC needs.
Troubleshooting
Issue: Found a bug in the playbook
To report a bug or request an improvement for a playbook, select the Supported by link in the playbook's details pane. If this is a community-supported playbook, the link takes you to open a GitHub issue. Otherwise, you're directed to the supporter's page.
Next steps
In this article, you learned how to work with playbook templates, creating and customizing playbooks to fit your needs. Learn more about playbooks and automation in Microsoft Sentinel:
- Security Orchestration, Automation, and Response (SOAR) in Microsoft Sentinel
- Automate threat response with playbooks in Microsoft Sentinel
- Tutorial: Use playbooks with automation rules in Microsoft Sentinel
- Authenticate playbooks to Microsoft Sentinel
- Use triggers and actions in Microsoft Sentinel playbooks
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for
