Set up automatic enrollment for Windows devices
Applies to
- Windows 10
- Windows 11
Simplify device enrollment by enabling automatic enrollment in Microsoft Intune. This enrollment method enables devices to enroll automatically when they join or register in Microsoft Entra ID. Enrollment in Intune occurs when:
- A Microsoft Entra user adds their work or school account to their personal device.
- A corporate-owned device joins to your Microsoft Entra ID.
Automatic enrollment can be used in the following device management and provisioning scenarios:
- Bring-your-own-device (BYOD), personal devices
- Bulk enrollment
- Group Policy
- Windows Autopilot (user driven and self-deploying)
- Co-management with Configuration Manager
This article describes how to enable automatic mobile device management (MDM) enrollment for personal and corporate-owned devices.
Prerequisites
You must have:
A Microsoft Entra ID P1 or P2 subscription or Premium trial subscription for automatic MDM enrollment and custom company branding.
A Microsoft Intune subscription.
Global Administrator permissions.
Enable Windows automatic enrollment
Sign in to Microsoft Intune admin center as a Global administrator or Intune service administrator.
Sign in to the Microsoft Intune admin center
Go to Devices > Enrollment.
Go to the Windows tab. Then select Automatic Enrollment.
Note
Automatic MDM enrollment is a premium Microsoft Entra feature available for Microsoft Entra ID Premium subscribers. If you can't see the automatic enrollment settings, select Automatic MDM enrollment is available only for Microsoft Entra ID Premium subscribers to activate a free trial.
Select Microsoft Intune.
Configure the MDM user scope. This setting enables automatic MDM enrollment for Microsoft Entra users so that you can manage their devices in Intune.
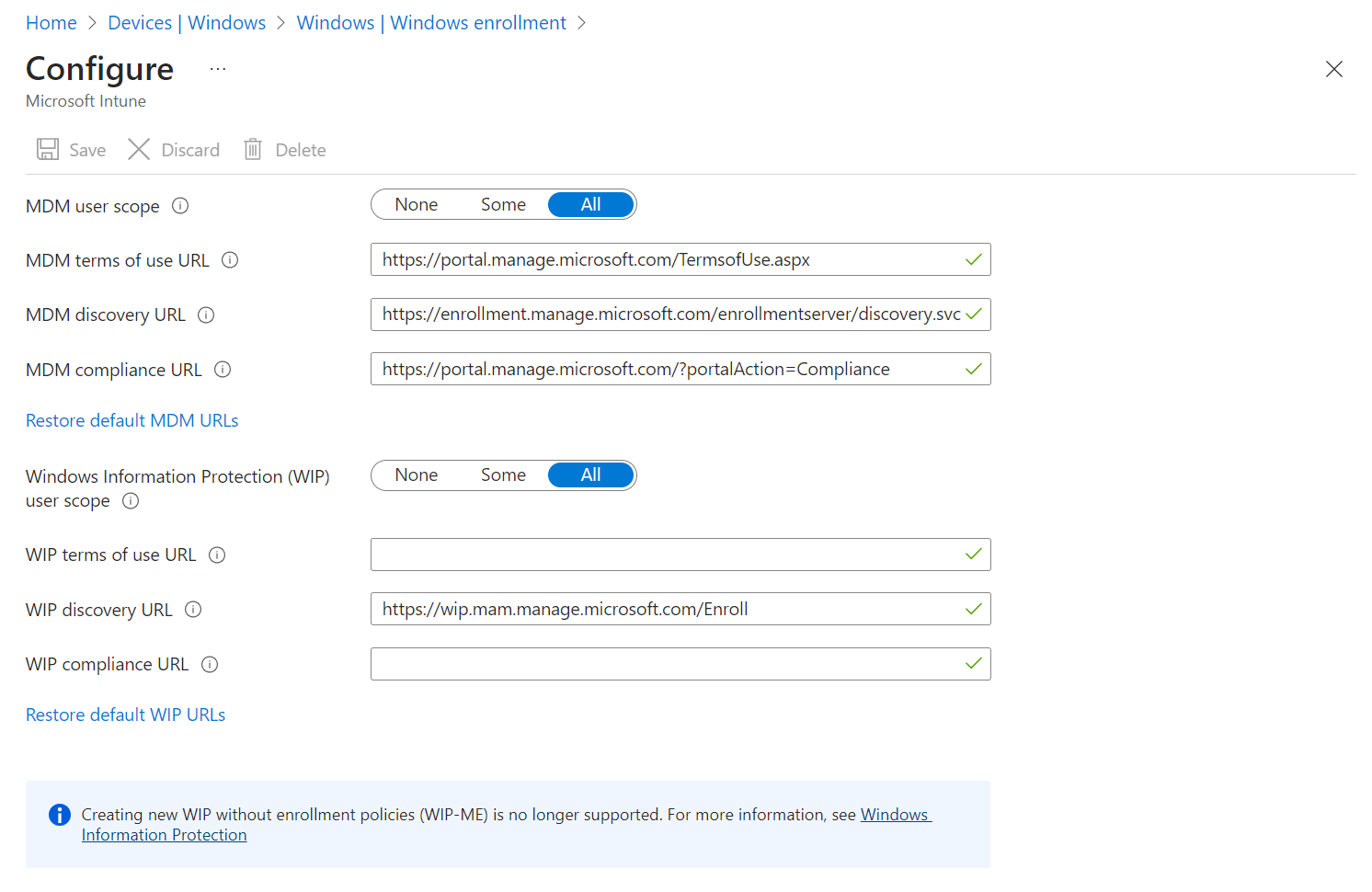
Your options are:
- None - Automatic MDM enrollment is disabled for all users. You can still manage devices in Microsoft Intune but users must initiate MDM enrollment.
- Some - Automatic MDM enrollment is enabled for the users you select.
- All - Automatic MDM enrollment is enabled for all users. Their devices automatically enroll in Intune when they join or register with Microsoft Entra ID.
Tip
If your intent is to enable automatic MDM enrollment for Windows BYOD devices, select All or Some for the MDM user scope. Then make sure the WIP user scope is None or Some, and that users are not members of both user scopes.
Use the default values for these URLs:
- MDM Terms of use URL
- MDM Discovery URL
- MDM Compliance URL
For WIP user scope, select None. If the WIP user scope is set to any other value, make sure the selected users aren't a part of the MDM user scope.
Important
When a user is in both the MDM user scope and WIP user scope:
- The MDM user scope takes precedence if they're on a corporate-owned device. The device automatically enrolls in Microsoft Intune when they set it up for work.
- The WIP user scope takes precedence if they bring their own device. The device doesn't enroll in Microsoft Intune for device management. Microsoft Purview Information Protection policies are applied if you configured them.
Select Save.
Multifactor authentication
Two-factor authentication is not enabled for automatic enrollment by default. We recommend requiring multifactor authentication during device registration. For more information, see Getting started with the Azure Multi-Factor Authentication Server.
Support for device users
The Microsoft Intune user-help docs provide conceptual information, tutorials, and how-to guides for employees and students setting up their devices for work. You can point people directly to the Intune docs, or use these articles as guidance when developing and updating your own device management docs.
Users on personal devices running Windows 11 or Windows 10 can automatically enroll by adding their work or school account on their device, or by using the Intune Company Portal app. Devices running earlier versions of Windows must enroll using the Intune Company Portal app. For more information, see Enroll Windows 10/11 devices.
You can also let unlicensed admins sign in to the Intune admin center to help with troubleshooting and support. For more information, see Unlicensed admins.
Best practices and troubleshooting
Device users must access the Company Portal website through Microsoft Edge to view apps assigned for specific versions of Windows. Other browsers such as Google Chrome, Mozilla Firefox, and Internet Explorer do not support this type of filtering.
After enrollment, you'll see two records in the Microsoft Intune admin center if automatic MDM enrollment is disabled and devices are joined to Microsoft Entra ID. To stop the duplicate records, instruct users on joined devices to Settings > Accounts > Access work or school. Then they can Connect using the same account.
Next steps
For information about how to integrate and use automatic enrollment when provisioning devices, see:
- Windows Autopilot scenarios
- Enroll a Windows client device automatically using Group Policy
- Enable co-management in Configuration Manager
If you're not using automatic enrollment as part of your enrollment or provisioning solution, we recommend creating a domain name server (DNS) alias (known as a CNAME record type) that redirects enrollment requests to Intune servers. For more information, see Enable automatic discovery of Intune enrollment server.
Povratne informacije
Uskoro: tokom 2024. postepeno ćemo ukidati probleme s uslugom GitHub kao mehanizam povratnih informacija za sadržaj i zamijeniti ga novim sistemom povratnih informacija. Za više informacija, pogledajte https://aka.ms/ContentUserFeedback.
Pošalјite i prikažite povratne informacije za