What are the Microsoft Entra user provisioning logs?
Microsoft Entra ID integrates with several third party services to provision users into your tenant. If you need to troubleshoot an issue with a provisioned user, you can use the information captured in the Microsoft Entra provisioning logs to help find a solution.
Two other activity logs are also available to help monitor the health of your tenant:
- Sign-ins – Information about sign-ins and how your resources are used by your users.
- Audit – Information about changes applied to your tenant such as users and group management or updates applied to your tenant’s resources.
This article gives you an overview of the user provisioning logs.
License and role requirements
The required roles and licenses vary based on the report. Separate permissions are required to access monitoring and health data in Microsoft Graph. We recommend using a role with least privilege access to align with the Zero Trust guidance.
| Log / Report | Roles | Licenses |
|---|---|---|
| Audit | Reports Reader Security Reader Security Administrator Global Reader |
All editions of Microsoft Entra ID |
| Sign-ins | Reports Reader Security Reader Security Administrator Global Reader |
All editions of Microsoft Entra ID |
| Provisioning | Reports Reader Security Reader Security Administrator Global Reader Security Operator Application Administrator Cloud App Administrator |
Microsoft Entra ID P1 or P2 |
| Custom security attribute audit logs* | Attribute Log Administrator Attribute Log Reader |
All editions of Microsoft Entra ID |
| Usage and insights | Reports Reader Security Reader Security Administrator |
Microsoft Entra ID P1 or P2 |
| Identity Protection** | Security Administrator Security Operator Security Reader Global Reader |
Microsoft Entra ID Free Microsoft 365 Apps Microsoft Entra ID P1 or P2 |
| Microsoft Graph activity logs | Security Administrator Permissions to access data in the corresponding log destination |
Microsoft Entra ID P1 or P2 |
*Viewing the custom security attributes in the audit logs or creating diagnostic settings for custom security attributes requires one of the Attribute Log roles. You also need the appropriate role to view the standard audit logs.
**The level of access and capabilities for Identity Protection varies with the role and license. For more information, see the license requirements for Identity Protection.
What can you do with the provisioning logs?
You can use the provisioning logs to find answers to questions like:
- What groups were successfully created in ServiceNow?
- What users were successfully removed from Adobe?
- What users from Workday were successfully created in Active Directory?
Note
Entries in the provisioning logs are system generated and can't be changed or deleted.
What do the logs show?
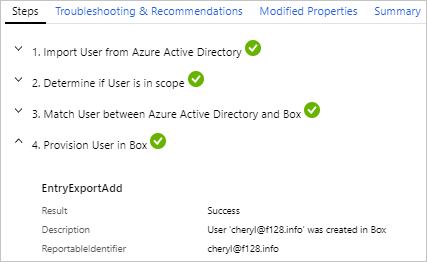
When you select an item in the provisioning list view, you get more details about this item, such as the steps taken to provision the user and tips for troubleshooting issues. The details are grouped into four tabs.
Steps: This tab outlines the steps taken to provision an object. Provisioning an object can include the following steps, but not all steps are applicable to all provisioning events.
- Import the object.
- Match the object between source and target.
- Determine if the object is in scope.
- Evaluate the object before synchronization.
- Provision the object (create, update, delete, or disable).
Troubleshooting & Recommendations: If there was an error, this tab provides the error code and reason.
Modified Properties: If there were changes, this tab shows the old value and the new value.
Summary: Provides an overview of what happened and identifiers for the object in the source and target systems.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for