Configure Azure DDoS Protection diagnostic logging alerts
DDoS Protection diagnostic logging alerts provide visibility into DDoS attacks and mitigation actions. You can configure alerts for all DDoS protected public IP addresses that you have enabled diagnostic logging on.
In this tutorial, you learn how to:
- Configure diagnostic logging alerts through Azure Monitor and Logic App.
Prerequisites
- If you don't have an Azure subscription, create a free account before you begin.
- DDoS Network Protection must be enabled on a virtual network or DDoS IP Protection must be enabled on a public IP address.
- In order to use diagnostic logging, you must first create a Log Analytics workspace with diagnostic settings enabled.
- DDoS Protection monitors public IP addresses assigned to resources within a virtual network. If you don't have any resources with public IP addresses in the virtual network, you must first create a resource with a public IP address. You can monitor the public IP address of all resources deployed through Resource Manager (not classic) listed in Virtual network for Azure services (including Azure Load Balancers where the backend virtual machines are in the virtual network), except for Azure App Service Environments. To continue with this guide, you can quickly create a Windows or Linux virtual machine.
Configure diagnostic logging alerts through Azure Monitor
With these templates, you'll be able to configure alerts for all public IP addresses that you have enabled diagnostic logging on.
Create Azure Monitor alert rule
The Azure Monitor alert rule template will run a query against the diagnostic logs to detect when an active DDoS mitigation is occurring. The alert indicates a potential attack. Action groups can be used to invoke actions as a result of the alert.
Deploy the template
Select Deploy to Azure to sign in to Azure and open the template.
On the Custom deployment page, under Project details, enter the following information.
Setting Value Subscription Select your Azure subscription. Resource Group Select your Resource group. Region Select your Region. Workspace Name Enter your workspace name. In this example the Workspace name is myLogAnalyticsWorkspace. Location Enter East US. Note
Location must match the location of the workspace.
Select Review + create and then select Create after validation passes.
Create Azure Monitor diagnostic logging alert rule with Logic App
This DDoS Mitigation Alert Enrichment template deploys the necessary components of an enriched DDoS mitigation alert: Azure Monitor alert rule, action group, and Logic App. The result of the process is an email alert with details about the IP address under attack, including information about the resource associated with the IP. The owner of the resource is added as a recipient of the email, along with the security team. A basic application availability test is also performed and the results are included in the email alert.
Deploy the template
Select Deploy to Azure to sign in to Azure and open the template.
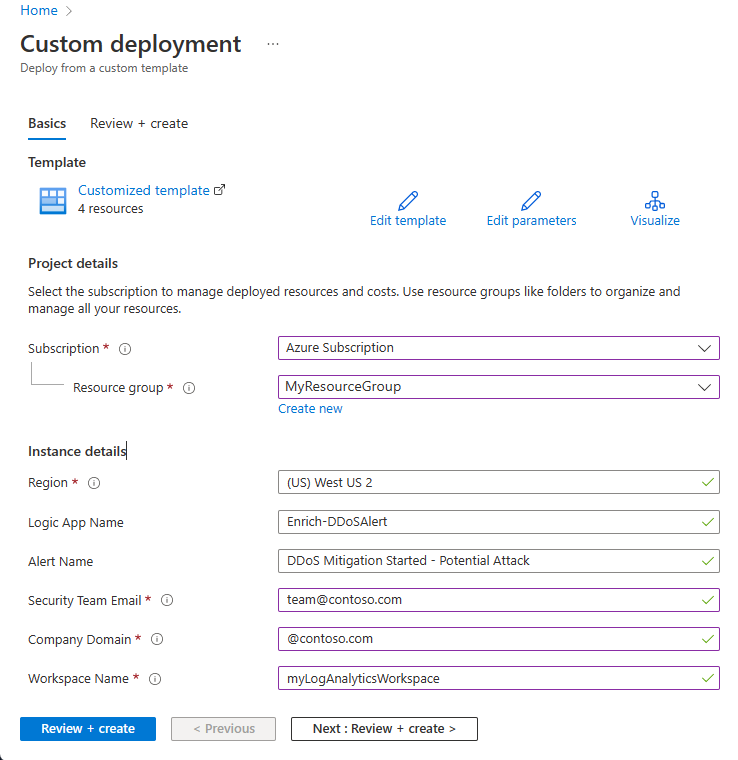
On the Custom deployment page, under Project details, enter the following information.
Setting Value Subscription Select your Azure subscription. Resource Group Select your Resource group. Region Select your Region. Alert Name Leave as default. Security Team Email Enter the required email address. Company Domain Enter the required domain. Workspace Name Enter your workspace name. In this example the Workspace name is myLogAnalyticsWorkspace. Select Review + create and then select Create after validation passes.
Clean up resources
You can keep your resources for the next guide. If no longer needed, delete the alerts.
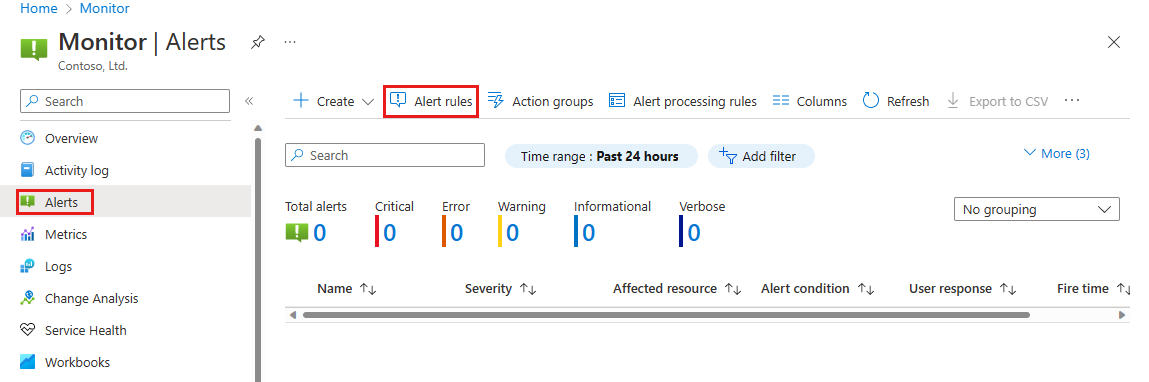
In the search box at the top of the portal, enter Alerts. Select Alerts in the search results.
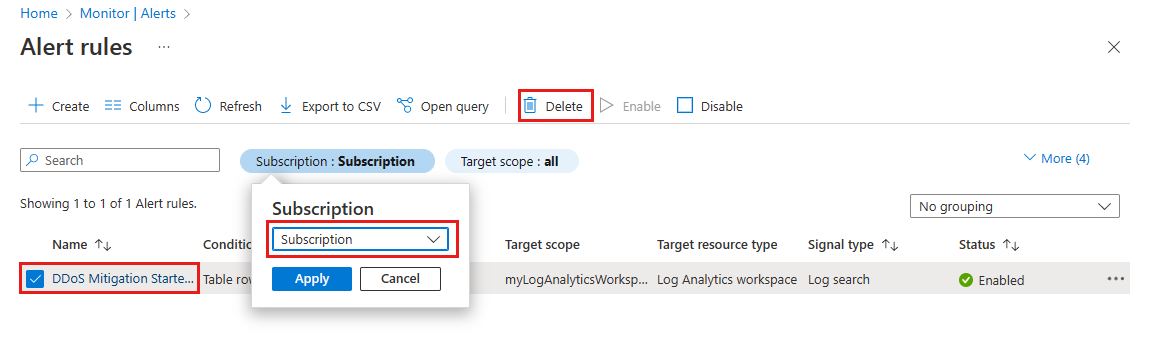
Select Alert rules, then in the Alert rules page, select your subscription.
Select the alerts created in this guide, then select Delete.
Next steps
In this tutorial you learned how to configure diagnostic alerts through Azure portal.
To test DDoS Protection through simulations, continue to the next guide.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for