To grant access to users in Microsoft Entra ID, you assign Microsoft Entra roles. A role is a collection of permissions. This article describes how to assign Microsoft Entra roles using the Microsoft Entra admin center and PowerShell.
Assign Microsoft Entra roles to users
Prerequisites
- Privileged Role Administrator or Global Administrator. To know who your Privileged Role Administrator or Global Administrator is, see List Microsoft Entra role assignments
- Microsoft Entra ID P2 license when using Privileged Identity Management (PIM)
- Microsoft Graph PowerShell module when using PowerShell
- Admin consent when using Graph explorer for Microsoft Graph API
For more information, see Prerequisites to use PowerShell or Graph Explorer.
Microsoft Entra admin center
Follow these steps to assign Microsoft Entra roles using the Microsoft Entra admin center. Your experience will be different depending on whether you have Microsoft Entra Privileged Identity Management (PIM) enabled.
Assign a role
Tip
Steps in this article might vary slightly based on the portal you start from.
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to Identity > Roles & admins > Roles & admins.
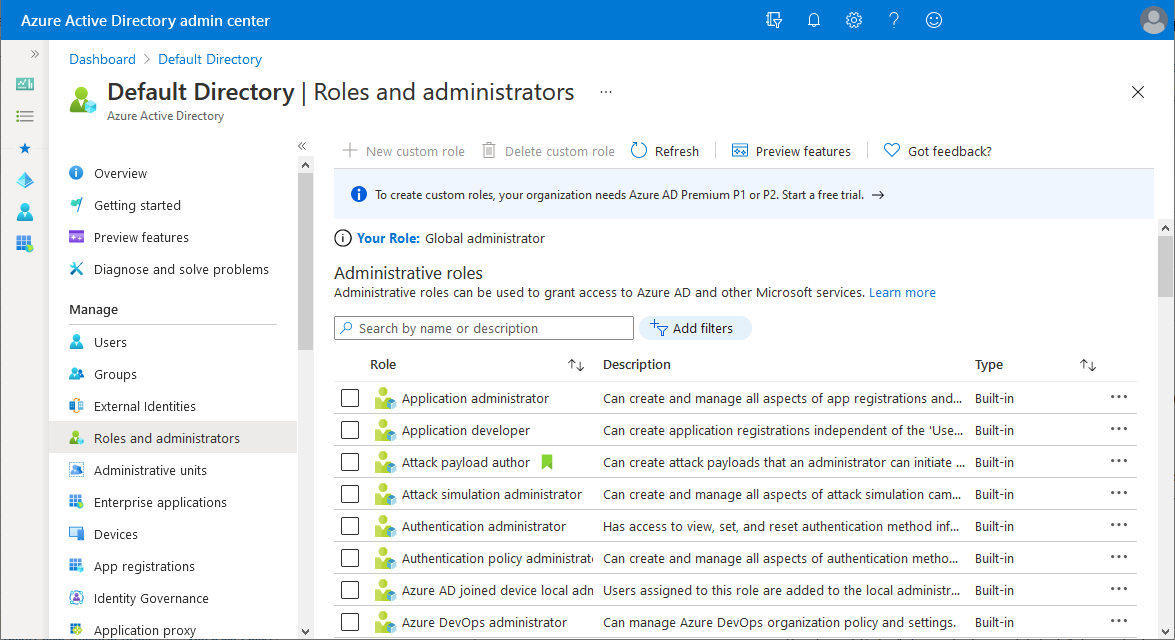
Find the role you need. You can use the search box or Add filters to filter the roles.
Select the role name to open the role. Don't add a check mark next to the role.
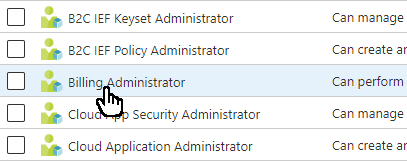
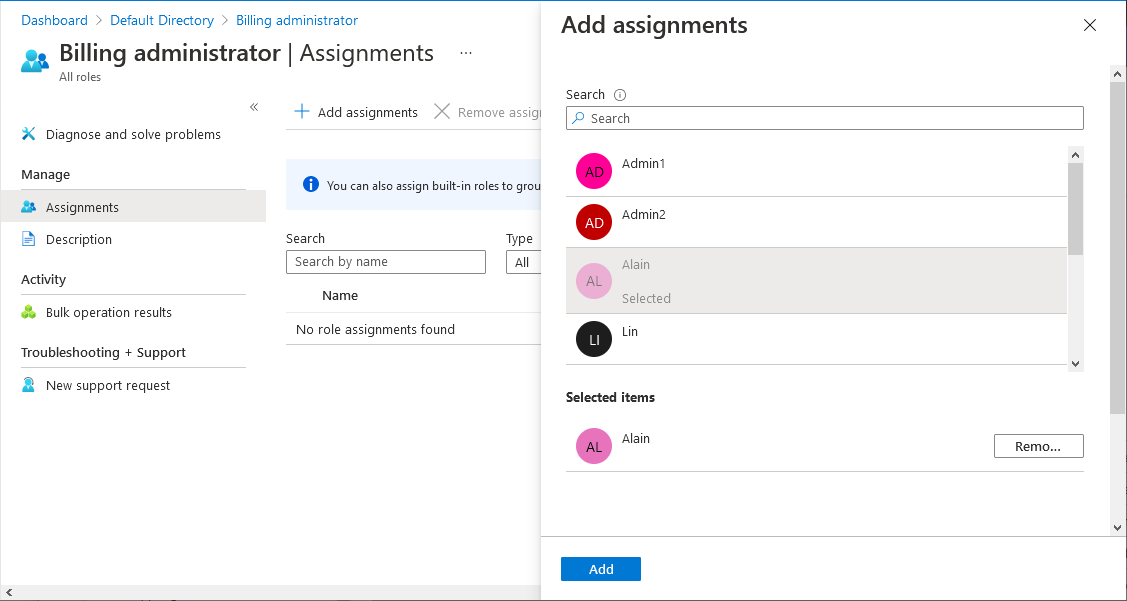
Select Add assignments and then select the users you want to assign to this role.
If you see something different from the following picture, you might have PIM enabled. See the next section.
Note
If you assign a Microsoft Entra built-in role to a guest user, the guest user will be elevated to have the same permissions as a member user. For information about member and guest user default permissions, see What are the default user permissions in Microsoft Entra ID?
Select Add to assign the role.
Assign a role using PIM
If you have Microsoft Entra Privileged Identity Management (PIM) enabled, you have additional role assignment capabilities. For example, you can make a user eligible for a role or set the duration. When PIM is enabled, there are two ways that you can assign roles using the Microsoft Entra admin center. You can use the Roles and administrators page or the PIM experience. Either way uses the same PIM service.
Follow these steps to assign roles using the Roles and administrators page. If you want to assign roles using Privileged Identity Management, see Assign Microsoft Entra roles in Privileged Identity Management.
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to Identity > Roles & admins > Roles & admins.

Find the role you need. You can use the search box or Add filters to filter the roles.
Select the role name to open the role and see its eligible, active, and expired role assignments. Don't add a check mark next to the role.

Select Add assignments.
Select No member selected and then select the users you want to assign to this role.
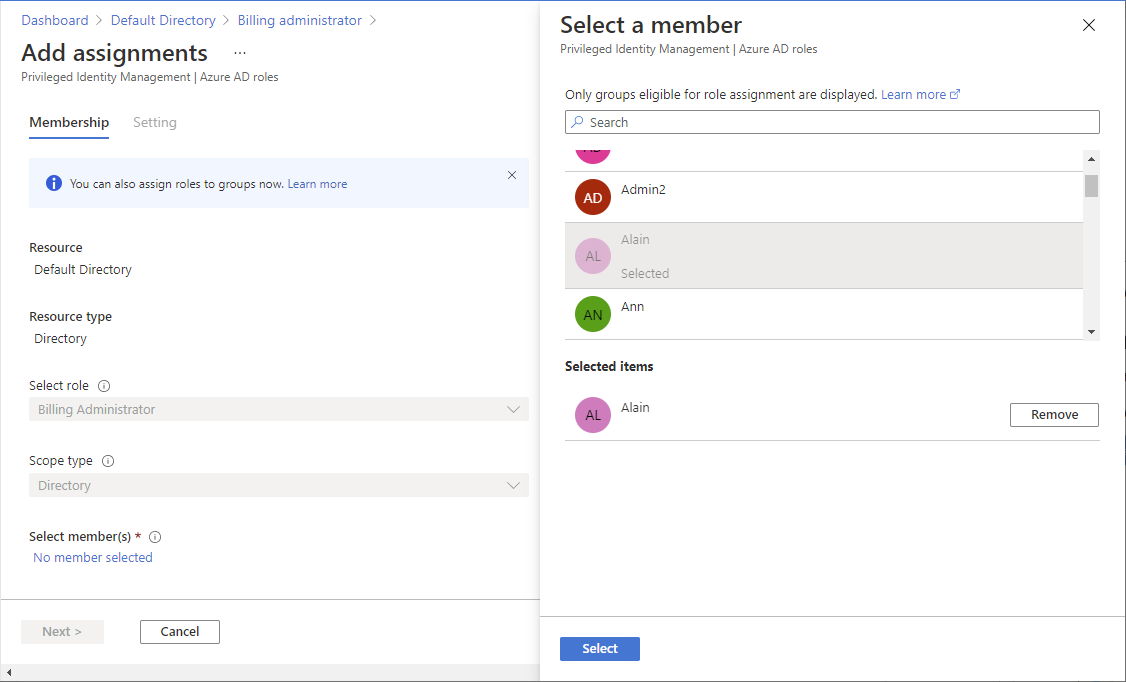
Select Next.
On the Setting tab, select whether you wan to make this role assignment Eligible or Active.
An eligible role assignment means that the user must perform one or more actions to use the role. An active role assignment means that the user doesn't have to perform any action to use the role. For more information about what these settings mean, see PIM terminology.
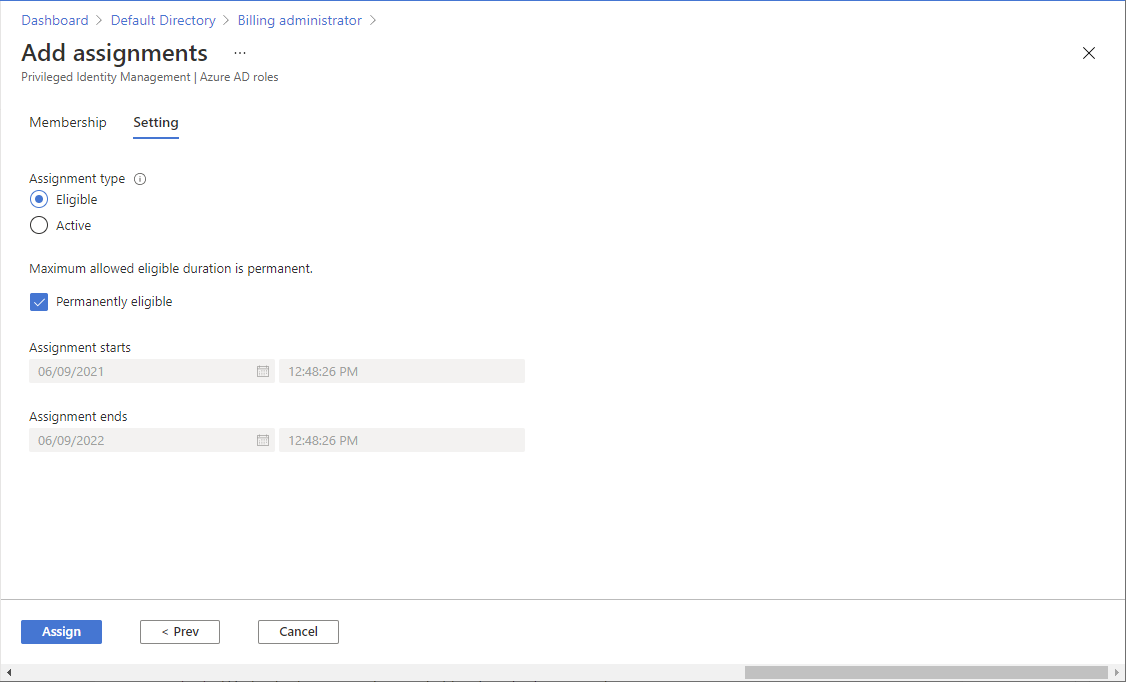
Use the remaining options to set the duration for the assignment.
Select Assign to assign the role.
PowerShell
Follow these steps to assign Microsoft Entra roles using PowerShell.
Setup
Open a PowerShell window and use Import-Module to import the Microsoft Graph PowerShell module. For more information, see Prerequisites to use PowerShell or Graph Explorer.
Import-Module -Name Microsoft.Graph.Identity.Governance -ForceIn a PowerShell window, use Connect-MgGraph to sign in to your tenant.
Connect-MgGraph -Scopes "RoleManagement.ReadWrite.Directory"Use Get-MgUser to get the user you want to assign a role to.
$user = Get-MgUser -Filter "userPrincipalName eq 'johndoe@contoso.com'"
Assign a role
Use Get-MgRoleManagementDirectoryRoleDefinition to get the role you want to assign.
$roledefinition = Get-MgRoleManagementDirectoryRoleDefinition -Filter "DisplayName eq 'Billing Administrator'"Use New-MgRoleManagementDirectoryRoleAssignment to assign the role.
$roleassignment = New-MgRoleManagementDirectoryRoleAssignment -DirectoryScopeId '/' -RoleDefinitionId $roledefinition.Id -PrincipalId $user.Id
Assign a role as eligible using PIM
If PIM is enabled, you have additional capabilities, such as making a user eligible for a role assignment or defining the start and end time for a role assignment. These capabilities use a different set of PowerShell commands. For more information about using PowerShell and PIM, see PowerShell for Microsoft Entra roles in Privileged Identity Management.
Use Get-MgRoleManagementDirectoryRoleDefinition to get the role you want to assign.
$roledefinition = Get-MgRoleManagementDirectoryRoleDefinition -Filter "DisplayName eq 'Billing Administrator'"Use the following command to create a hash table to store all the necessary attributes required to assign the role to the user. The Principal ID will be the user ID to which you want to assign the role. In this example, the assignment will be valid only for 10 hours.
$params = @{ "PrincipalId" = "053a6a7e-4a75-48bc-8324-d70f50ec0d91" "RoleDefinitionId" = "b0f54661-2d74-4c50-afa3-1ec803f12efe" "Justification" = "Add eligible assignment" "DirectoryScopeId" = "/" "Action" = "AdminAssign" "ScheduleInfo" = @{ "StartDateTime" = Get-Date "Expiration" = @{ "Type" = "AfterDuration" "Duration" = "PT10H" } } }Use New-MgRoleManagementDirectoryRoleEligibilityScheduleRequest to assign the role as eligible. Once the role has been assigned, it will reflect in the Microsoft Entra admin center under Identity governance > Privileged Identity Management > Microsoft Entra roles > Assignments > Eligible Assignments section.
New-MgRoleManagementDirectoryRoleEligibilityScheduleRequest -BodyParameter $params | Format-List Id, Status, Action, AppScopeId, DirectoryScopeId, RoleDefinitionId, IsValidationOnly, Justification, PrincipalId, CompletedDateTime, CreatedDateTimeMicrosoft Graph API
Follow these instructions to assign a role using the Microsoft Graph API.
Assign a role
In this example, a security principal with objectID
f8ca5a85-489a-49a0-b555-0a6d81e56f0dis assigned the Billing Administrator role (role definition IDb0f54661-2d74-4c50-afa3-1ec803f12efe) at tenant scope. To see the list of immutable role template IDs of all built-in roles, see Microsoft Entra built-in roles.POST https://graph.microsoft.com/v1.0/roleManagement/directory/roleAssignments Content-type: application/json { "@odata.type": "#microsoft.graph.unifiedRoleAssignment", "roleDefinitionId": "b0f54661-2d74-4c50-afa3-1ec803f12efe", "principalId": "f8ca5a85-489a-49a0-b555-0a6d81e56f0d", "directoryScopeId": "/" }Assign a role using PIM
Assign a time-bound eligible role assignment
In this example, a security principal with objectID
f8ca5a85-489a-49a0-b555-0a6d81e56f0dis assigned a time-bound eligible role assignment to Billing Administrator (role definition IDb0f54661-2d74-4c50-afa3-1ec803f12efe) for 180 days.POST https://graph.microsoft.com/v1.0/rolemanagement/directory/roleEligibilityScheduleRequests Content-type: application/json { "action": "adminAssign", "justification": "for managing admin tasks", "directoryScopeId": "/", "principalId": "f8ca5a85-489a-49a0-b555-0a6d81e56f0d", "roleDefinitionId": "b0f54661-2d74-4c50-afa3-1ec803f12efe", "scheduleInfo": { "startDateTime": "2021-07-15T19:15:08.941Z", "expiration": { "type": "afterDuration", "duration": "PT180D" } } }Assign a permanent eligible role assignment
In the following example, a security principal is assigned a permanent eligible role assignment to Billing Administrator.
POST https://graph.microsoft.com/v1.0/rolemanagement/directory/roleEligibilityScheduleRequests Content-type: application/json { "action": "adminAssign", "justification": "for managing admin tasks", "directoryScopeId": "/", "principalId": "f8ca5a85-489a-49a0-b555-0a6d81e56f0d", "roleDefinitionId": "b0f54661-2d74-4c50-afa3-1ec803f12efe", "scheduleInfo": { "startDateTime": "2021-07-15T19:15:08.941Z", "expiration": { "type": "noExpiration" } } }Activate a role assignment
To activate the role assignment, use the Create roleAssignmentScheduleRequests API.
POST https://graph.microsoft.com/v1.0/roleManagement/directory/roleAssignmentScheduleRequests Content-type: application/json { "action": "selfActivate", "justification": "activating role assignment for admin privileges", "roleDefinitionId": "b0f54661-2d74-4c50-afa3-1ec803f12efe", "directoryScopeId": "/", "principalId": "f8ca5a85-489a-49a0-b555-0a6d81e56f0d" }For more information about managing Microsoft Entra roles through the PIM API in Microsoft Graph, see Overview of role management through the privileged identity management (PIM) API.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for