Events
9 Apr, 15 - 10 Apr, 12
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
In this article, you learn how to integrate Cisco Secure Firewall - Secure Client with Microsoft Entra ID. When you integrate Cisco Secure Firewall - Secure Client with Microsoft Entra ID, you can:
The scenario outlined in this article assumes that you already have the following prerequisites:
In this article, you configure and test Microsoft Entra SSO in a test environment.
To configure the integration of Cisco Secure Firewall - Secure Client into Microsoft Entra ID, you need to add Cisco Secure Firewall - Secure Client from the gallery to your list of managed SaaS apps.
Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, assign roles, and walk through the SSO configuration as well. Learn more about Microsoft 365 wizards.
Configure and test Microsoft Entra SSO with Cisco Secure Firewall - Secure Client using a test user called B.Simon. For SSO to work, you need to establish a link relationship between a Microsoft Entra user and the related user in Cisco Secure Firewall - Secure Client.
To configure and test Microsoft Entra SSO with Cisco Secure Firewall - Secure Client, perform the following steps:
Follow these steps to enable Microsoft Entra SSO.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > Cisco Secure Firewall - Secure Client > Single sign-on.
On the Select a single sign-on method page, select SAML.
On the Set up single sign-on with SAML page, select the edit/pen icon for Basic SAML Configuration to edit the settings.
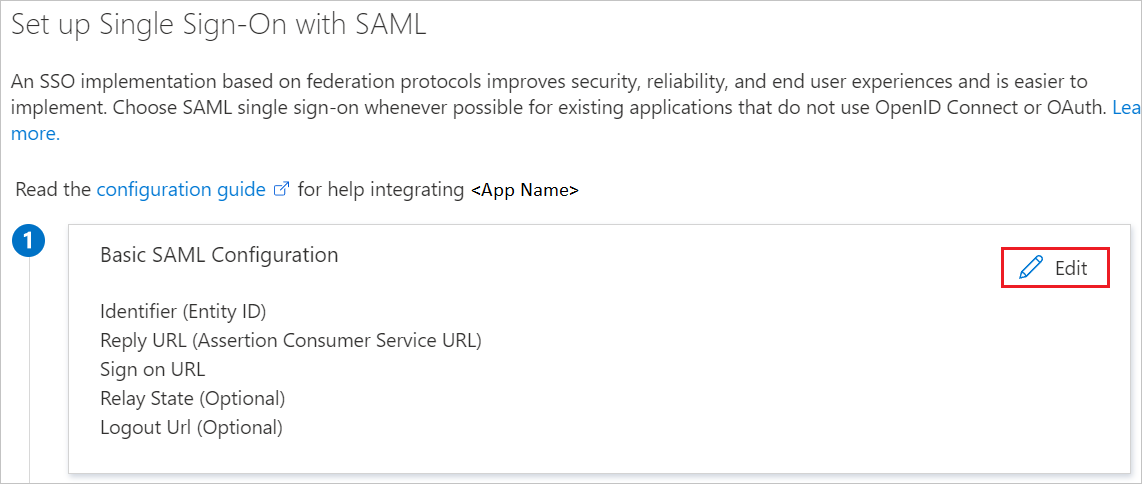
On the Set up single sign-on with SAML page, enter the values for the following fields:
In the Identifier text box, type a URL using the following pattern:
https://<SUBDOMAIN>.YourCiscoServer.com/saml/sp/metadata/<Tunnel_Group_Name>
In the Reply URL text box, type a URL using the following pattern:
https://<YOUR_CISCO_ANYCONNECT_FQDN>/+CSCOE+/saml/sp/acs?tgname=<Tunnel_Group_Name>
Note
<Tunnel_Group_Name> is a case-sensitive and the value must not contain dots "." and slashes "/".
Note
For clarification about these values, contact Cisco TAC support. Update these values with the actual Identifier and Reply URL provided by Cisco TAC. Contact the Cisco Secure Firewall - Secure Client support team to get these values. You can also refer to the patterns shown in the Basic SAML Configuration section.
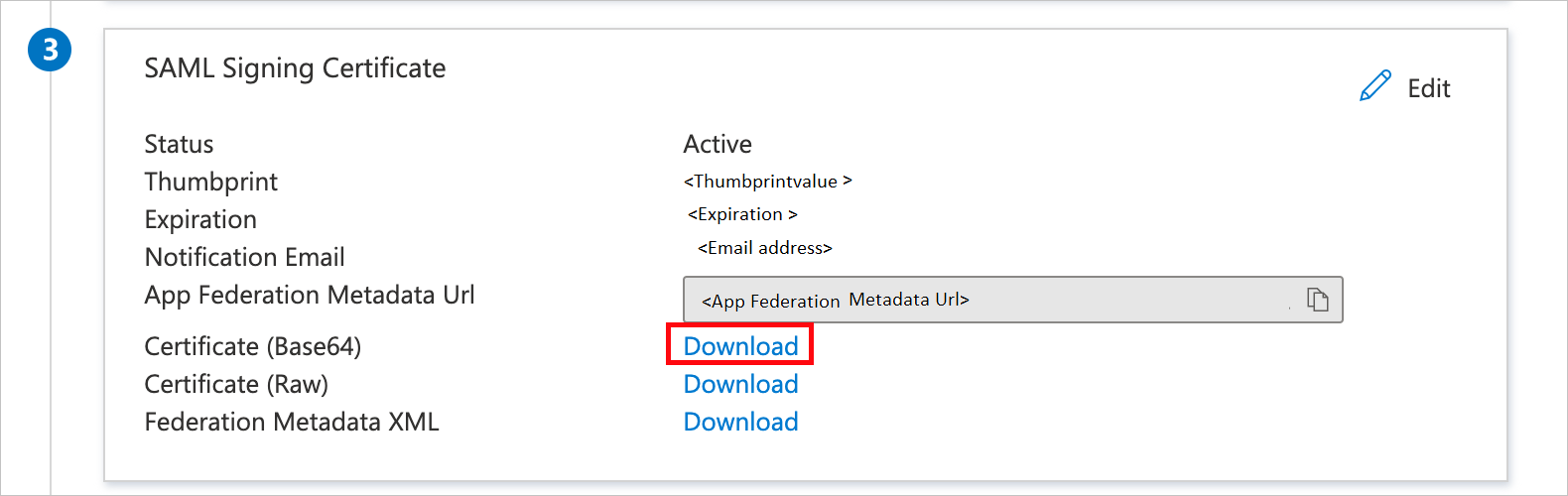
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64) and select Download to download the certificate file and save it on your computer.
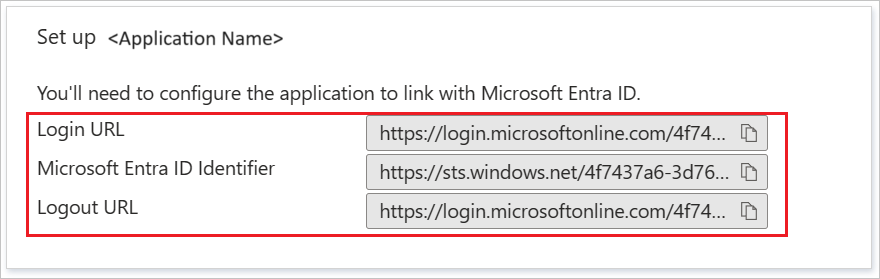
On the Set up Cisco Secure Firewall - Secure Client section, copy the appropriate URL(s) based on your requirement.
Note
If you would like to on board multiple TGTs of the server then you need to add multiple instances of the Cisco Secure Firewall - Secure Client application from the gallery. You can also choose to upload your own certificate in Microsoft Entra ID for all these application instances. That way you can have same certificate for the applications but you can configure different Identifier and Reply URL for every application.
Follow the guidelines in the create and assign a user account quickstart to create a test user account called B.Simon.
You're going to do this on the CLI first, you might come back through and do an ASDM walk-through at another time.
Connect to your VPN Appliance, you're going to be using an ASA running 9.8 code train, and your VPN clients are 4.6+.
First you create a Trustpoint and import our SAML cert.
config t
crypto ca trustpoint AzureAD-AC-SAML
revocation-check none
no id-usage
enrollment terminal
no ca-check
crypto ca authenticate AzureAD-AC-SAML
-----BEGIN CERTIFICATE-----
…
PEM Certificate Text from download goes here
…
-----END CERTIFICATE-----
quit
The following commands will provision your SAML IdP.
webvpn
saml idp https://sts.windows.net/xxxxxxxxxxxxx/ (This is your Azure AD Identifier from the Set up Cisco Secure Firewall - Secure Client section in the Azure portal)
url sign-in https://login.microsoftonline.com/xxxxxxxxxxxxxxxxxxxxxx/saml2 (This is your Login URL from the Set up Cisco Secure Firewall - Secure Client section in the Azure portal)
url sign-out https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 (This is Logout URL from the Set up Cisco Secure Firewall - Secure Client section in the Azure portal)
trustpoint idp AzureAD-AC-SAML
trustpoint sp (Trustpoint for SAML Requests - you can use your existing external cert here)
no force re-authentication
no signature
base-url https://my.asa.com
Now you can apply SAML Authentication to a VPN Tunnel Configuration.
tunnel-group AC-SAML webvpn-attributes
saml identity-provider https://sts.windows.net/xxxxxxxxxxxxx/
authentication saml
end
write mem
Note
There's a work around with the SAML IdP configuration. If you make changes to the IdP configuration you need to remove the saml identity-provider configuration from your Tunnel Group and re-apply it for the changes to become effective.
In this section, you create a user called Britta Simon in Cisco Secure Firewall - Secure Client. Work with Cisco Secure Firewall - Secure Client support team to add the users in the Cisco Secure Firewall - Secure Client platform. Users must be created and activated before you use single sign-on.
In this section, you test your Microsoft Entra single sign-on configuration with following options.
Once you configure Cisco Secure Firewall - Secure Client you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.
Events
9 Apr, 15 - 10 Apr, 12
Code the Future with AI and connect with Java peers and experts at JDConf 2025.
Register NowTraining
Module
Implement and monitor the integration of enterprise apps for SSO - Training
Deploying and monitoring enterprise applications to Azure solutions can ensure security. Explore how to deploy on-premises and cloud based apps to users.
Certification
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Documentation
Microsoft Entra single sign-on (SSO) integration with Meraki Dashboard - Microsoft Entra ID
Learn how to configure single sign-on between Microsoft Entra ID and Meraki Dashboard.