Diagnose on-premises VPN connectivity with Azure
In this article, you learn how to use Azure Network Watcher VPN troubleshoot capability to diagnose and troubleshoot your VPN gateway and its connection to your on-premises VPN device. For a list of validated VPN devices and their configuration guides, see VPN devices.
VPN troubleshoot allows you to quickly diagnose issues with your gateway and connections. It checks for common issues and returns a list of diagnostic logs that can be used to further troubleshoot the issue. The logs are stored in a storage account that you specify.
Prerequisites
An Azure account with an active subscription. Create an account for free.
A VPN device in your on-premises network represented by a local network gateway in Azure. For more information about local network gateways, see Create a local network gateway. For a list of validated VPN devices, see Validated VPN devices.
A VPN virtual network gateway in Azure with a site-to-site connection. For more information about virtual network gateways, see Create a VPN gateway and Default IPsec/IKE parameters
Troubleshoot using Network Watcher VPN troubleshoot
Use the VPN troubleshoot capability of Network Watcher to diagnose and troubleshoot your VPN gateway and its connection to your on-premises network.
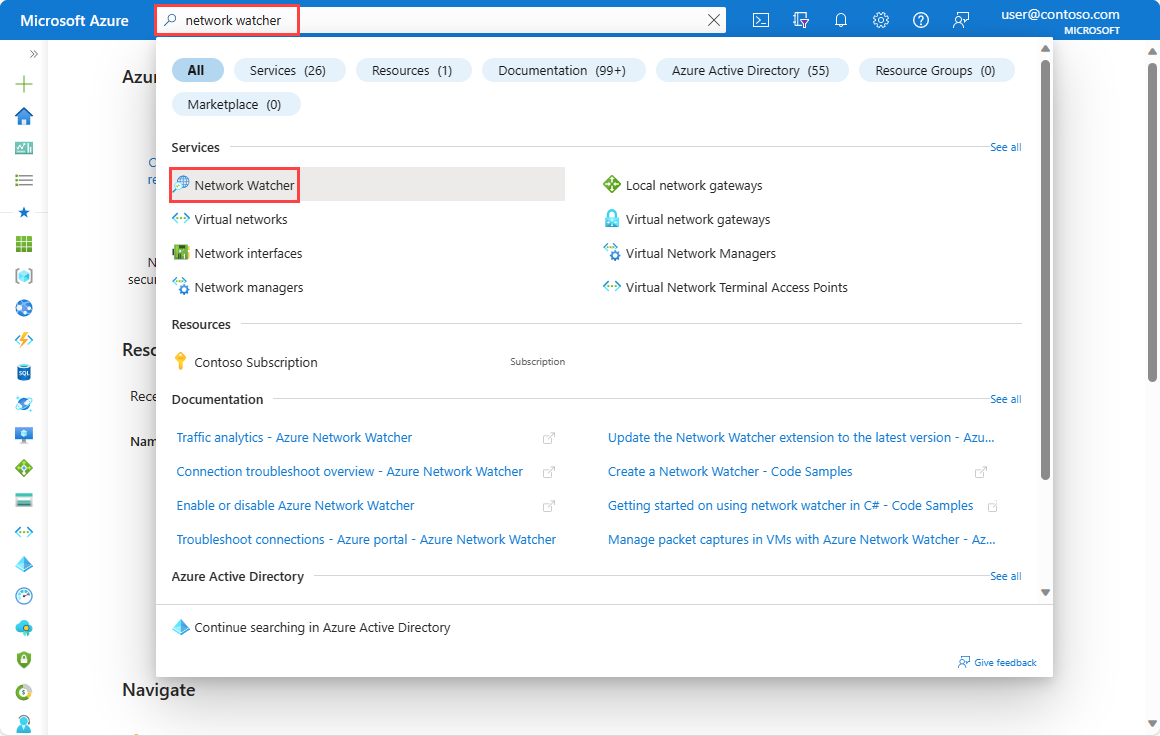
In the search box at the top of the portal, enter network watcher. Select Network Watcher in the search results.
Under Network diagnostic tools, select VPN troubleshoot.
In the VPN troubleshoot, select Select storage account to choose or create a Standard storage account to save the diagnostic files to.
Select the virtual network gateway and connection that you want to troubleshoot.
Select Start troubleshooting.
Once the check is completed, the troubleshooting status of the gateway and connection is displayed. The Unhealthy status indicates that there's an issue with the resource.
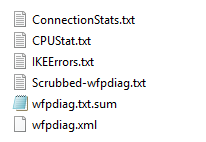
Go to the vpn container in the storage account that you previously specified and download the zip file that was generated during the VPN troubleshoot check session. Network Watcher creates a zip folder that contains the following diagnostic log files:
Note
- In some cases, only a subset of the log files is generated.
- For newer gateway versions, the IKEErrors.txt, Scrubbed-wfpdiag.txt and wfpdiag.txt.sum have been replaced by an IkeLogs.txt file that contains the whole IKE activity including any errors.
A common misconfiguration error is due to using incorrect shared keys where you can check the IKEErrors.txt to see the following error message:
Error: Authentication failed. Check shared key.
Another common error is due the misconfiguration of the IPsec parameters, where you can find the following error message in the IKEErrors.txt file:
Error: On-premises device rejected Quick Mode settings. Check values.
based on log : Peer sent NO_PROPOSAL_CHOSEN notify
For a detailed list of fault types that Network Watcher can diagnose and their logs, see Gateway faults and Connection faults.
Next step
Learn how to monitor VPN gateways using Azure Automation:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for