Secure score in Defender for Cloud
The secure score in Microsoft Defender for Cloud can help you to improve your cloud security posture. The secure score aggregates security findings into a single score so that you can assess, at a glance, your current security situation. The higher the score, the lower the identified risk level is.
When you turn on Defender for Cloud in a subscription, the Microsoft cloud security benchmark (MCSB) standard is applied by default in the subscription. Assessment of resources in scope against the MCSB standard begins.
The MCSB issues recommendations based on assessment findings. Only built-in recommendations from the MCSB affect the secure score. Currently, risk prioritization doesn't affect the secure score.
Note
Recommendations flagged as Preview aren't included in secure score calculations. You should still remediate these recommendations wherever possible, so that when the preview period ends, they'll contribute toward your score. Preview recommendations are marked with an icon: ![]() .
.
Viewing the secure score
When you view the Defender for Cloud Overview dashboard, you can view the secure score for all of your environments. The dashboard shows the secure score as a percentage value and includes the underlying values.
The Azure mobile app shows the secure score as a percentage value. Tap it to see details that explain the score.
Exploring your security posture
The Security posture page in Defender for Cloud shows the secure score for your environments overall and for each environment separately.
On this page, you can see the subscriptions, accounts, and projects that affect your overall score, information about unhealthy resources, and relevant recommendations. You can filter by environment, such as Azure, Amazon Web Services (AWS), Google Cloud Platform (GCP), and Azure DevOps. You can then drill down into each Azure subscription, AWS account, and GCP project.
Calculation of the secure score
On the Recommendations page in Defender for Cloud, the Secure score recommendations tab shows how compliance controls within the MCSB contribute toward the overall security score.
Defender for Cloud calculates each control every eight hours for each Azure subscription or for each AWS or GCP cloud connector.
Important
Recommendations within a control are updated more often than the control itself. You might find discrepancies between the resource count on the recommendations and the resource count on the control.
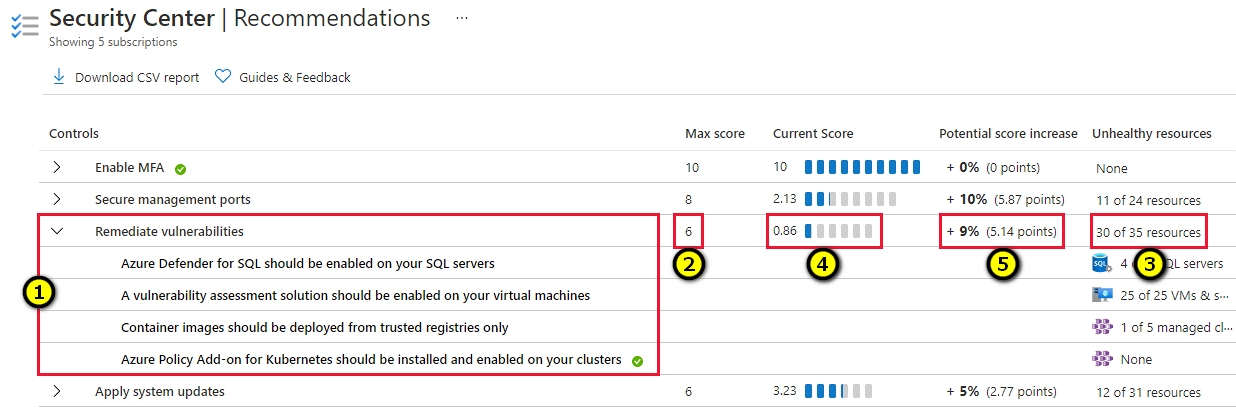
Example scores for a control
The following example focuses on secure score recommendations for enabling multifactor authentication (MFA).
This example illustrates the following fields in the recommendations.
| Field | Details |
|---|---|
| Remediate vulnerabilities | A grouping of recommendations for discovering and resolving known vulnerabilities. |
| Max score | The maximum number of points that you can gain by completing all recommendations within a control. The maximum score for a control indicates the relative significance of that control and is fixed for every environment. Use the values in this column to determine which issues to work on first. |
| Current score | The current score for this control. Current score = [Score per resource] * [Number of healthy resources] Each control contributes to the total score. In this example, the control is contributing 2.00 points to current total score. |
| Potential score increase | The remaining points available to you within the control. If you remediate all the recommendations in this control, your score increases by 9%. Potential score increase = [Score per resource] * [Number of unhealthy resources] |
| Insights | Extra details for each recommendation, such as: - - - - |
Score calculation equations
Here's how scores are calculated.
Security control
The equation for determining the score for a security control is:
The current score for each control is a measure of the status of the resources within the control. Each individual security control contributes toward the secure score. Each resource that's affected by a recommendation within the control contributes toward the control's current score. The secure score doesn't include resources found in preview recommendations.
In the following example, the maximum score of 6 is divided by 78 because that's the sum of the healthy and unhealthy resources. So, 6 / 78 = 0.0769. Multiplying that by the number of healthy resources (4) results in the current score: 0.0769 * 4 = 0.31.
Single subscription or connector
The equation for determining the secure score for a single subscription or connector is:
In the following example, there's a single subscription or connector with all security controls available (a potential maximum score of 60 points). The score shows 29 points out of a possible 60. The remaining 31 points are reflected in the Potential score increase figures of the security controls.
This equation is the same equation for a connector, with just the word subscription replaced by the word connector.
Multiple subscriptions and connectors
The equation for determining the secure score for multiple subscriptions and connectors is:
The combined score for multiple subscriptions and connectors includes a weight for each subscription and connector. Defender for Cloud determines the relative weights for your subscriptions and connectors based on factors such as the number of resources. The current score for each subscription and connector is calculated in the same way as for a single subscription or connector, but then the weight is applied as shown in the equation.
When you view multiple subscriptions and connectors, the secure score evaluates all resources within all enabled policies and groups them. Grouping them shows how, together, they affect each security control's maximum score.
The combined score is not an average. Rather, it's the evaluated posture of the status of all resources across all subscriptions and connectors. If you go to the Recommendations page and add up the potential points available, you find that it's the difference between the current score (22) and the maximum score available (58).
Improving a secure score
The MCSB consists of a series of compliance controls. Each control is a logical group of related security recommendations and reflects your vulnerable attack surfaces.
To see how well your organization is securing each individual attack surface, review the scores for each security control. Your score improves only when you remediate all of the recommendations.
To get all the possible points for a security control, all of your resources must comply with all of the security recommendations within the security control. For example, Defender for Cloud has multiple recommendations for how to secure your management ports. You need to remediate them all to make a difference in your secure score.
You can improve your secure score by using either of these methods:
- Remediate security recommendations from your recommendations list. You can remediate each recommendation manually for each resource, or use the Fix option (when available) to resolve an issue on multiple resources quickly.
- Enforce or deny recommendations to improve your score, and to make sure that your users don't create resources that negatively affect your score.
Secure score controls
The following table lists the security controls in Microsoft Defender for Cloud. For each control, you can see the maximum number of points that you can add to your secure score if you remediate all of the recommendations listed in the control, for all of your resources.
| Secure score | Security control |
|---|---|
| 10 | Enable MFA: Defender for Cloud places a high value on MFA. Use these recommendations to help secure the users of your subscriptions. There are three ways to enable MFA and be compliant with the recommendations: security defaults, per-user assignment, and conditional access policy. Learn more. |
| 8 | Secure management ports: Brute force attacks often target management ports. Use these recommendations to reduce your exposure with tools like just-in-time VM access and network security groups. |
| 6 | Apply system updates: Not applying updates leaves unpatched vulnerabilities and results in environments that are susceptible to attacks. Use these recommendations to maintain operational efficiency, reduce security vulnerabilities, and provide a more stable environment for your users. To deploy system updates, you can use the Update Management solution to manage patches and updates for your machines. |
| 6 | Remediate vulnerabilities: When your vulnerability assessment tool reports vulnerabilities to Defender for Cloud, Defender for Cloud presents the findings and related information as recommendations. Use these recommendations to remediate identified vulnerabilities. |
| 4 | Remediate security configurations: Misconfigured IT assets have a higher risk of being attacked. Use these recommendations to harden the identified misconfigurations across your infrastructure. |
| 4 | Manage access and permissions: A core part of a security program is ensuring that your users have just the necessary access to do their jobs: the least privilege access model. Use these recommendations to manage your identity and access requirements. |
| 4 | Enable encryption at rest: Use these recommendations to ensure that you mitigate misconfigurations around the protection of your stored data. |
| 4 | Encrypt data in transit: Use these recommendations to help secure data that's moving between components, locations, or programs. Such data is susceptible to man-in-the-middle attacks, eavesdropping, and session hijacking. |
| 4 | Restrict unauthorized network access: Azure offers a suite of tools that help you provide high security standards for access across your network. Use these recommendations to manage adaptive network hardening in Defender for Cloud, ensure that you configured Azure Private Link for all relevant platform as a service (PaaS) services, enable Azure Firewall on virtual networks, and more. |
| 3 | Apply adaptive application control: Adaptive application control is an intelligent, automated, end-to-end solution to control which applications can run on your machines. It also helps to harden your machines against malware. |
| 2 | Protect applications against DDoS attacks: Advanced networking security solutions in Azure include Azure DDoS Protection, Azure Web Application Firewall, and the Azure Policy add-on for Kubernetes. Use these recommendations to help protect your applications with these tools and others. |
| 2 | Enable endpoint protection: Defender for Cloud checks your organization's endpoints for active threat detection and response solutions, such as Microsoft Defender for Endpoint or any of the major solutions shown in this list. If no endpoint detection and response (EDR) solution is enabled, use these recommendations to deploy Microsoft Defender for Endpoint. Defender for Endpoint is included in the Defender for Servers plan. Other recommendations in this control help you deploy agents and configure file integrity monitoring. |
| 1 | Enable auditing and logging: Detailed logs are a crucial part of incident investigations and many other troubleshooting operations. The recommendations in this control focus on ensuring that you enabled diagnostic logs wherever they're relevant. |
| 0 | Enable enhanced security features: Use these recommendations to enable any Defender for Cloud plans. |
| 0 | Implement security best practices: This collection of recommendations is important for your organizational security but doesn't affect your secure score. |
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for