Grant and manage consent to Teams app permissions
Use of Teams apps can provide an incredible boost to the productivity of and collaboration between your organization's users. Teams apps bring information at the tips of your users, without any context switching, and help them do great work. As an admin, you play a critical role to empower your users with the right type of apps while balancing your company's need for security and compliance. Once you decide to approve the use of an app, you must make sure that the app adoption is smooth for the users.
A crucial part is to grant consent to the permissions that an app needs to work. You consent for approved apps so that each user in your organization doesn't have to review permissions and consent individually, when they start the app. A few examples of permissions requested by apps include the ability to read information stored in a team, read a user's profile, and send an email on behalf of users. To learn more about permissions and consent, see Permissions and consent in the Microsoft identity platform endpoint.
To safeguard company's needs and adhere to its policies, only a Global Administrator can grant consent to apps permissions on behalf of all users in your organization. The option to view details and requirement to grant consent applies to custom and third-party apps, and not to the apps provided by Microsoft.
View Microsoft Graph permissions requested by an app
On the Manage apps page, the Permissions column indicates whether an app has permissions that need consent. Select the View details link for an app to view the various permissions and access to organization's information that the app requests. The option to view details and grant consent applies to custom and third-party apps, and not to the apps provided by Microsoft.
Grant org-wide admin consent to an app's permissions
Granting consent to such permissions allows an app to access your organization's information. Carefully review the permissions requested by the app before you grant consent. For more information, see Teams apps permissions and consent. Only Global Administrators can grant consent to the Graph permissions that an app requests. Teams Administrators can view the required permissions in admin center. The option to view details and grant consent applies to custom and third-party apps, and not to the apps provided by Microsoft.
To view and grant consent for all users in your organization, follow these steps:
In Teams admin center, access Teams apps > Manage apps.
Search for the required app and then do one of the following actions:
- Select the View details link in the Permissions column of the app, to open the Permissions tab.
- Select the app name to go to the app details page and select the Permissions tab.
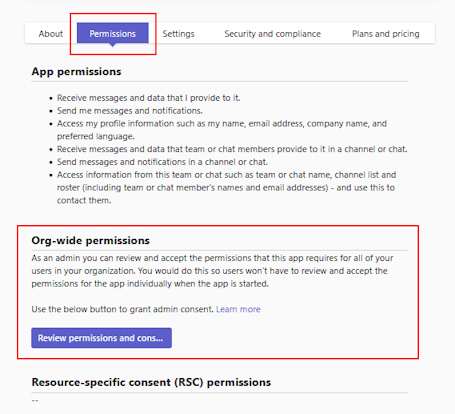
Under Org-wide permissions, select Review permissions and consent.
In the dialog that opens, review the permissions requested by the app.
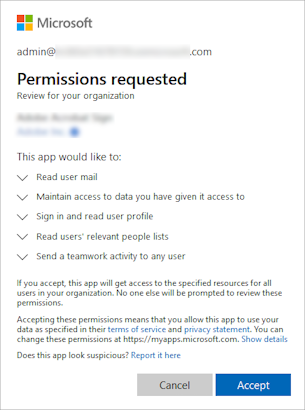
If you agree with the permissions requested by the app, select Accept to grant consent. A banner temporarily appears at the top of the page to let you know that the requested permissions are granted for the app. The app now has access to the specified resources for all users in your organization for whom the app is allowed. Users aren't prompted now to review the permissions.
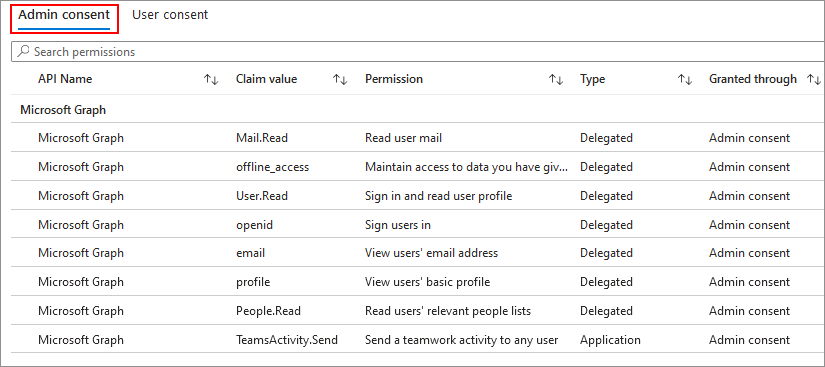
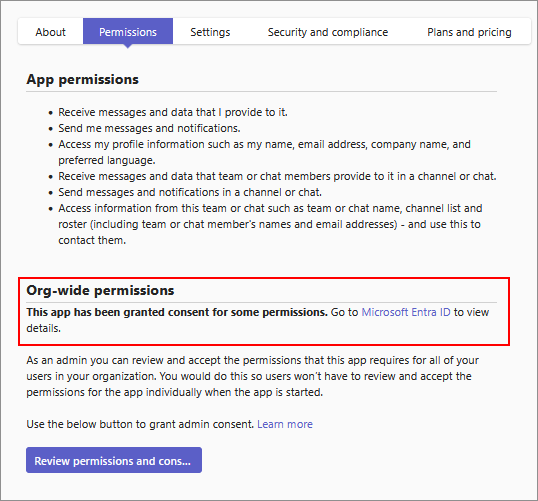
After you grant consent to permissions of an app, you'll see a message in the Permissions tab to let you know that consent was granted. If you want to view the app's permissions in Microsoft Entra ID, click the link to open the app's permissions in Microsoft Entra admin center.
Note
If the new version of an app requires extra permissions than the previous version, then you must grant consent to the app again.
Let users grant consent to low risk Graph permissions
You can configure user consent settings to let users consent to selected permissions (recommended approach) and use apps that require only these specific permissions without needing admin consent.
This approach works together with permissions classification in Microsoft Entra ID portal. The classification let admins define some Delegated Graph permissions as low risk permissions within their organization. Admins decide which low risk permissions based on their organization's risk posture. As a safety measure, you can't categorize Application permissions low risk.
You can configure user consent settings in way that lets users to:
- Not be able to consent to any apps and hence use only admin-approved apps.
- Consent to selected permissions (recommended approach) and use app that required only these specific permissions.
The recommended approach works together with permissions classification. The classification let admins define some or all of the Delegated Graph permissions as low risk permissions within their organization. Admins decide low risk permissions based on their organization's risk posture. As a safety measure, you can't categorize Application permissions low risk. Application permissions require only an admin to consent. For more information, see configure how users consent to applications and how to classify permissions as low or high risk.
To accomplish this configuration, you must have a Global Administrator, Application Administrator, or Cloud Application Administrator role in your organization.
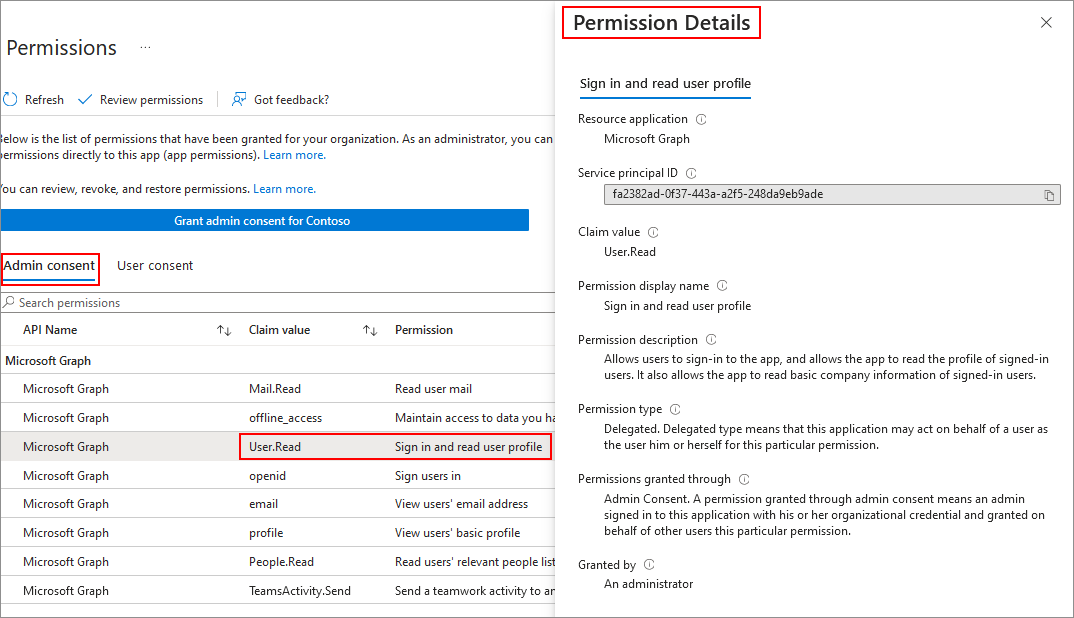
Check and verify granted consent to permissions
After you grant consent to permissions of an app, you'll see a message in the Permissions tab to let you know that consent was granted.

If you want to view the app's permissions in Microsoft Entra ID, select the link to open the app's permissions in Microsoft Entra admin center.
Select a permission to know more details about it.
Revoke granted consent to permissions
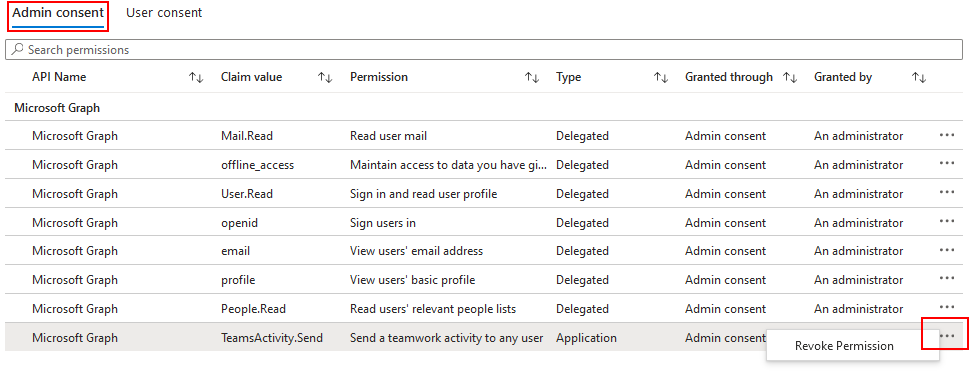
To revoke the consent that you granted to an app previously, follow these steps:
In the Permissions tab, select the Microsoft Entra ID link to open the app's permissions in Microsoft Entra admin center.
In the Admin consent tab, choose the permission you would like to revoke and then select the ellipses
....Select Revoke Permission and then select Yes, revoke in the confirmation dialog.
After you revoke consent to some permissions, you can regrant consent. See Grant org-wide admin consent to an app's permissions.
Grant consent to new Graph permissions after an app update
Developers update apps to add new functionality, enhance existing functionality, or fix bugs. Some app updates may add new permissions that weren't part of the previous version of the app. If the developer adds any new permissions that require admin consent, you must consent to the new permissions. Reconsent flow is the same as described in Grant org-wide admin consent to an app's permissions.
To know about app changes that require consent from a user or an admin, see conditions when an app update requires consenting. Depending on your organization's configuration, users may be able to grant consent to some types of permissions.
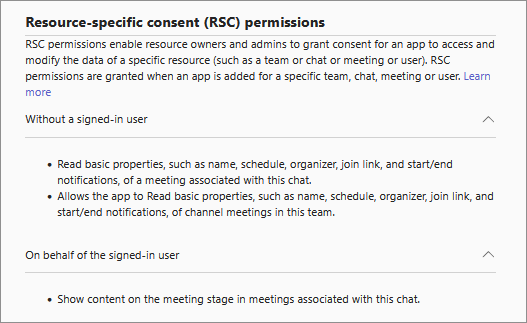
View resource-specific consent permissions of an app
RSC permissions let an app access and modify a team's or a user's data. RSC permissions are granular and specific to the Teams team in which an app is added. A few examples of RSC permissions are the ability to create and delete channels in a team, get the settings for a team, and create and remove channel tabs.
RSC permissions are defined in the app manifest and not in Microsoft Entra admin center. Team owners can grant consent for such permissions when they add the app to a team or a chat. To know more, see Resource-specific consent (RSC).
Global Administrators and Teams Administrators can view RSC permissions for an app in the Permissions tab of the app details page. To view RSC permissions for an app, follow these steps:
In Teams admin center, go to Teams apps > Manage apps.
Search for the required app in the catalog.
Click the app name to go to the app details page and then select the Permissions tab. Alternately, select the View details link of the app.
Under Resource-specific consent (RSC) permissions, review the RSC permissions requested by the app.
Let resource owners consent to RSC permissions
Admins can configure whether users can let apps access their groups' or teams' data or not. Global Administrators can change the Group owner consent for apps accessing data settings in Microsoft Entra ID, to let users to consent to RSC permissions.
If you don't let group owner consent for apps, then users can't consent to RSC permissions in an app, if RSC permissions are used.
Related articles
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for