IT Admins - Manage external meetings and chat with people and organizations using Microsoft identities
With the external access feature in Teams, you can allow users in your organization to chat and meet with people outside the organization who are using Microsoft as an identity provider. You can configure external access with:
Other Microsoft 365 organizations (chat and meetings)
Teams users not managed by an organization (those using a Microsoft account) (chat only)
Skype users (chat only)
Users in your organization can accept or block incoming chats from people outside the organization. For details, see Accept or block people outside your org who send you a chat.
Note that these people from outside your organization won't have access to your teams, sites, or other Microsoft 365 resources. If you want them to have access to your teams and channels, see Collaborate with guests in a team and Collaborate with external participants in a shared channel.
Note
Your users can add apps when they host meetings or chats with people outside your organization. They can also use apps shared by external users when they join meetings or chats hosted externally. The data policies of the hosting user's organization, as well as the data sharing practices of any third-party apps shared by that user's organization, are applied. Learn more about use of apps by people outside your organization.
Related settings
It's important to note that there are other settings in Teams—including guest access and anonymous access—that affect meetings with people outside your organization. See Plan for meetings with external participants in Microsoft Teams for more information.
The meeting lobby can control how people outside your organization join meetings. For more information, see Control who can bypass the meeting lobby in Microsoft Teams and Configure the Microsoft Teams meeting lobby for sensitive meetings.
Organization settings and user policies for external access
Each external access option has both an organization setting and user policies. The organization settings apply to your entire organization. User policies determine which users can use the options that you've configured at the organization level.
Configure the organization settings to specify which types of external meetings and chat you want to allow, and then configure user policies for the users who should have access to these features. Note that both the organization settings and user policies are turned on by default.
For a user to use external access, both the organization setting and a user policy must allow it.
Use the procedures on the tabs below to configure organization settings and user policies.
In this section, you can configure:
- Meetings and chat with trusted Microsoft 365 organizations
- Chat with external Teams users not managed by an organization
- Chat and calls with Skype users
You can also configure these settings by using PowerShell
Specify trusted Microsoft 365 organizations
For meetings and chat with other Microsoft 365 organizations, you can specify which domains you want to trust. By default, all external domains are allowed. You can allow or block certain domains in order to define which organizations your organization trusts for external meetings and chat.
In order to chat and meet with people in external domains, the organizations that you trust must also trust your organization, and their users must be enabled for external access. If not, they won't be able to chat with users in your organization and are considered anonymous when joining meetings hosted by your organization. Learn more about meetings with other Microsoft 365 organizations.
You can specify which domains are allowed or which domains are blocked. If you specify blocked domains, all other domains are allowed; if you specify allowed domains, all other domains are blocked. There are four scenarios for configuring trusted organizations:
Allow all external domains - This is the default setting in Teams, and it lets users in your organization find, call, chat, and set up meetings with people external to your organization in any domain.
In this scenario, your users can communicate with all external domains that are running Teams or Skype for Business so long as the other organization has also enabled external access.
Allow only specific external domains - By adding domains to an Allow list, you limit external access to only the allowed domains. Once you set up a list of allowed domains, all other domains are blocked.
Block specific domains - By adding domains to a Block list, you can communicate with all external domains except the ones you've blocked. Once you set up a list of blocked domains, all other domains are allowed.
Block all external domains - Prevents users in your organization from finding, calling, chatting, and setting up meetings with people external to your organization in any domain.
Note
People from blocked domains can still join meetings anonymously if anonymous access is allowed. To learn more, see Manage anonymous participant access to Teams meetings.

To allow specific domains
In the Teams admin center, go to Users > External access.
Under Choose which domains your users have access to, choose Allow only specific external domains.
Select Allow domains.
In the Domain box, type the domain that you want to allow and then click Done.
If you want to allow another domain, click Add a domain.
Click Save.
To block specific domains
In the Teams admin center, go to Users > External access.
Under Choose which domains your users have access to, choose Block only specific external domains.
Select Block domains.
In the Domain box, type the domain that you want to allow and then click Done.
If you want to block another domain, click Add a domain.
Click Save.
By default, when you block domains, subdomains aren't blocked. For example, if you block contoso.com, marketing.contoso.com isn't blocked. If you want to block all subdomains, you can use the Set-CsTenantFederationConfiguration PowerShell cmdlet with the -BlockAllSubdomains parameter. For example:
Set-CsTenantFederationConfiguration -BlockAllSubdomains $True
Diagnostic Tool
If you're an administrator, you can use the following diagnostic tool to validate if a Teams user can communicate with a Teams user in a trusted organization:
Select Run Tests below, which populates the diagnostic in the Microsoft 365 Admin Center.
In the Run diagnostic pane, enter the Session Initiation Protocol (SIP) Address and the Federated tenant's domain name, and then select Run Tests.
The tests return the best next steps to address any setting or policy configurations that are preventing communication with the external Teams user.
Skype for Business Online
If you want chats and calls to arrive in the user's Skype for Business client, configure your users to be in any mode other than TeamsOnly. For more information, see Understand Microsoft Teams and Skype for Business coexistence and interoperability.
Manage chats and meetings with external Teams users not managed by an organization
You can choose to enable or disable chat with external unmanaged Teams users (those not managed by an organization, such as Microsoft Teams (free)). If you allow chat with unmanaged Teams users, you can further control how your users communicate with them:
- You can control if unmanaged Teams users can initiate the communication with your users.
- You can create a list of external user profiles that users can communicate with.
- You can restrict communication to the external user profiles list if needed.
Note
Chats and meetings with external unmanaged Teams users isn't available in GCC, GCC High, or DOD deployments, or in private cloud environments.
To allow chats and meetings with unmanaged Teams accounts
In the Teams admin center, go to Users > External access.
Turn on the People in my organization can communicate with Teams users whose accounts aren't managed by an organization setting.
If you want to allow external unmanaged Teams users to start the conversation, select the External users with Teams accounts not managed by an organization can contact users in my organization checkbox.
If you want to restrict communication with people with unmanaged Teams accounts to a specific list of user profiles, select the Restrict communication to the list of external user profiles added to extended directory checkbox and select Manage external user profiles to add the user profiles that you want to allow. (See manage external user profiles below.)
Note
Parent Connection in Microsoft Teams for Education does not support restricting communication to the list of external user profiles added to extended directory.
Select Save.
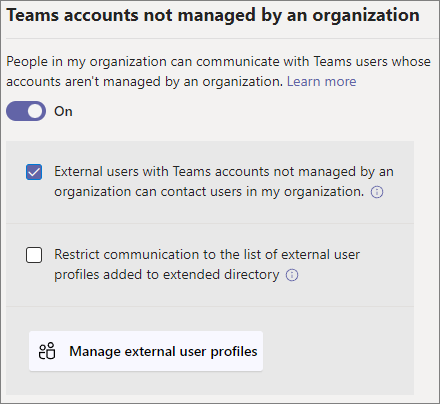
Note that if External users with Teams accounts not managed by an organization can contact users in my organization is turned off, unmanaged Teams users can't search by email address to find users in your organization. All communications with unmanaged Teams users must be initiated by users in your organization.
To prevent chat with unmanaged Teams accounts
In the Teams admin center, go to Users > External access.
Turn off the People in my organization can communicate with Teams users whose accounts aren't managed by an organization setting.
Select Save.
Manage external user profiles
External user profiles are based on phone numbers. You can add the name and phone numbers of people outside your organization and they'll be invited to communicate with people in your organization by using Teams on their mobile device. If they don't have Teams installed, they will receive a link to install it via SMS. Once they have created a Teams account, they can also use Teams on the desktop. You can delegate management of the user profiles by using the Extended Directory User Administrator role in Azure AD.
When a profile is added for someone outside your organization, it's available to your users via search by name or phone number within 24 hours. Users can start a 1:1 or group chat with the external users and can see the external users' profile cards with the information that you specify.
When a user starts a chat with an external user, the external user can allow or block the connection.
Important
Your organization is the Data Controller for the external user profiles that you add. This may have GDPR implications. For more information, see General Data Protection Regulation Summary.
To add an external user profile
- Select Manage external user profiles.
- Select Add.
- Type a Display name for the contact. (Users will be able to search for this name in Teams.)
- Type a Country or region code and Phone number.
- Add any additional information that you want to include.
- Read the Data Controller statement and select the check box to agree.
- Select Save.
You can remove an existing profile by selecting the profile and then selecting Delete.
Import a list of profiles
If you want to upload a list of users via .csv file, you can download a template file, add the people you want to include and their phone numbers, and upload the file.
To download the .csv template
- On the Manage external user profiles page, select Import on the command bar.
- Select download a template.
Required fields in the template are DisplayName and PhoneNumber. Other fields are optional.
To upload a completed template file
- On the Manage external user profiles page, select Import on the command bar.
- Select Select a file.
- Select the file that you want to upload and then select Open.
- If you want to update the profile information for existing profiles, select the Update existing external users checkbox.
- Read the Data Controller statement and select the check box to agree.
- Select Import.
Use PowerShell to restrict communication to the user profiles in extended directory
You can also configure the Restrict communication to the list of external user profiles added to extended directory setting in PowerShell by using the Set-CsExternalAccessPolicy cmdlet with the RestrictTeamsConsumerAccessToExternalUserProfiles parameter. For example:
Set-CsExternalAccessPolicy -Identity Global -RestrictTeamsConsumerAccessToExternalUserProfiles $true
restricts communication to the list of user profiles in extended directory for the default global external access policy.
Manage chat and calls with Skype users
Follow these steps to let Teams users in your organization chat with and call Skype users. Teams users can then search for and start a one-on-one text-only conversation or an audio/video call with Skype users and vice versa.
Meetings aren't supported with Skype users. If invited to a meeting, they're considered anonymous when joining.
Note
External communication with Skype users isn't available in GCC, GCC High, or DOD deployments, or in private cloud environments.
To configure chat and calls with Skype users
In the Teams admin center, go to Users > External access.
Turn the Allow users in my organization to communicate with Skype users setting on or off.
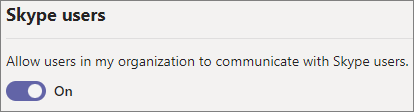
Select Save.
To learn more about the ways that Teams users and Skype users can communicate, including limitations that apply, see Teams and Skype interoperability.
Configure organization settings by using PowerShell
Trusted organizations can be configured by using the Set-CSTenantFederationConfiguration cmdlet.
The following table shows the cmdlet parameters used for configuring trusted organizations.
| Configuration | Parameter |
|---|---|
| Allow or prevent meetings and chat with other Teams organizations and Skype for Business | -AllowFederatedUsers |
| Specify allowed domains | -AllowedDomains |
| Specify blocked domains | -BlockedDomains |
| Block subdomains | -BlockAllSubdomains |
Chat with Teams users not managed by an organization and Skype users can be configured by using the Set-CSTenantFederationConfiguration cmdlet.
The following table shows the cmdlet parameters used for configuring chat with Skype and unmanaged Teams users.
| Configuration | Parameter |
|---|---|
| Allow or prevent chat with Teams users that aren't managed by an organization | -AllowTeamsConsumer |
| Allow or prevent Teams users not managed by an organization starting conversations | -AllowTeamsConsumerInbound |
| Allow or prevent chat with Skype users | -AllowPublicUsers |
Before you can run these cmdlets you must be connected to Microsoft Teams PowerShell. For more information, see Manage Teams with Microsoft Teams PowerShell.
Compliance and external access
See the following references to understand how external access works with compliance features in Microsoft 365.
- eDiscovery in external access and guest environments
- Message retention with external access users
- Data loss prevention and Microsoft Teams
Related topics
Use guest access and external access to collaborate with people outside your organization
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for