Hello,
Thank you so much for posting here.
There is no connection between the key size selection on a CA certificate or sub-ordinate CA, and an End-Entity certificate. An End-Entity certificate can use a key size that is larger, or smaller than that used on the CA certificate or sub-ordinate CA used to sign the End-Entity certificate.
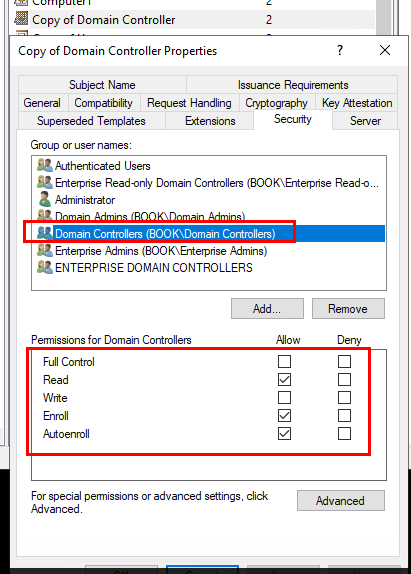
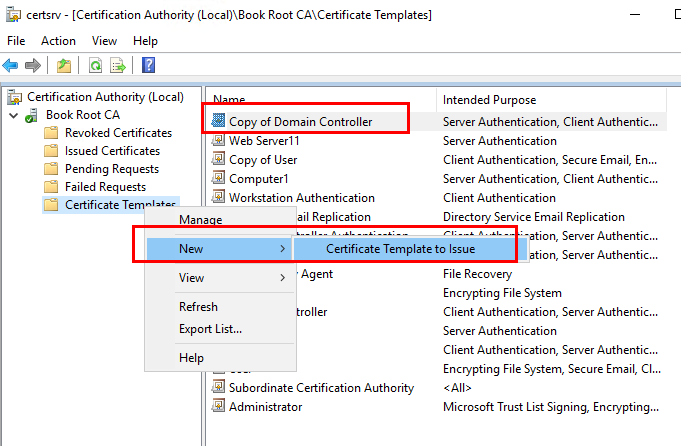
CA has the Domain Controller template in their default template list, but it is v1 certificate template, and not support auto-enrollment by default, you need to duplicate and custom the domain controller certificate.
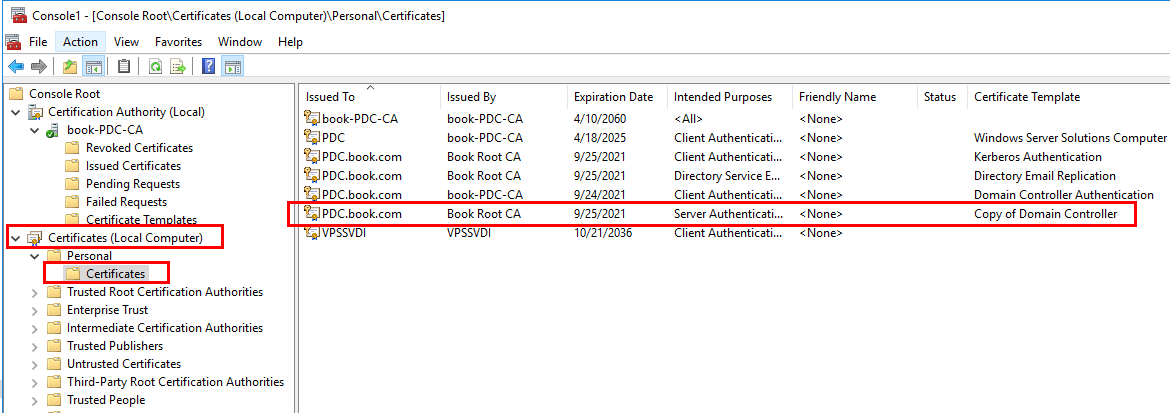
In my case, I tried to create a duplicate of domain controller certificate template with 1024 key size as shown below. (The CA certificate is 2048 bit key size.)Then issue this certificate template.
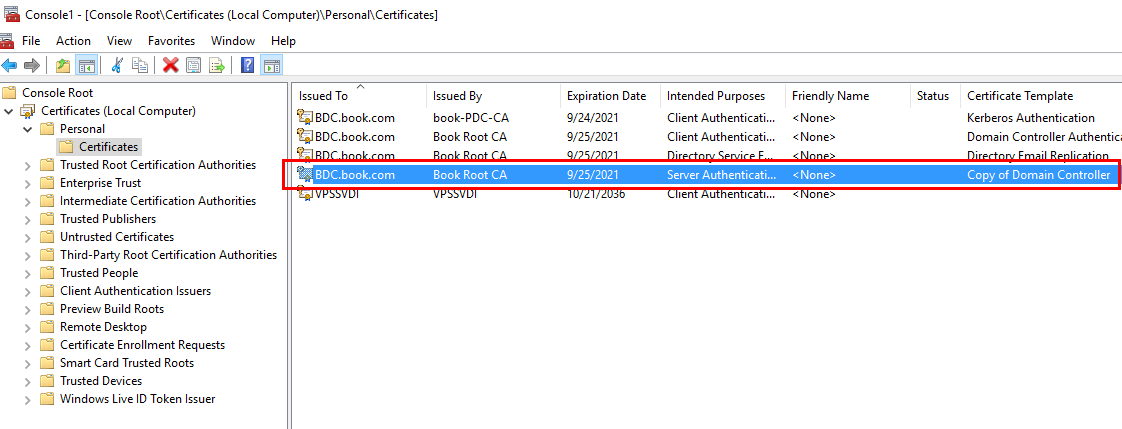
Once requesting the new certificate from this certificate template via Certificate MMC, it shows 1024 key size as shown below.
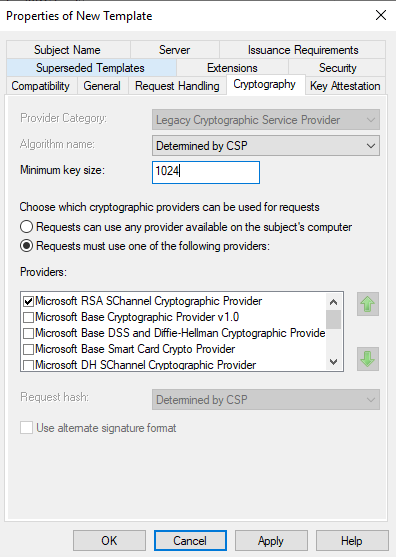
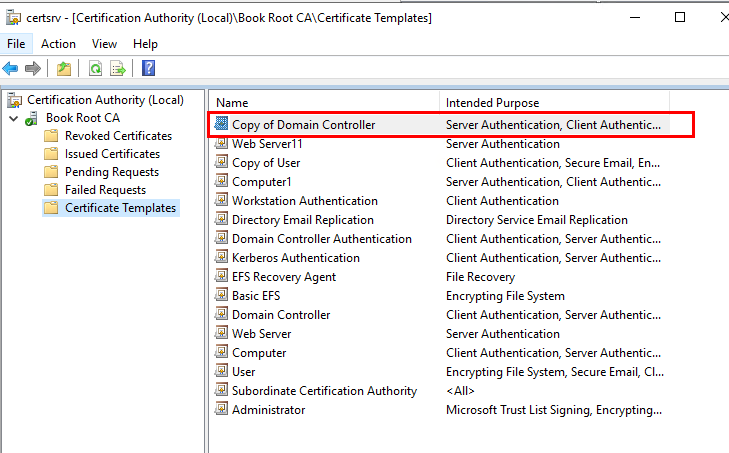
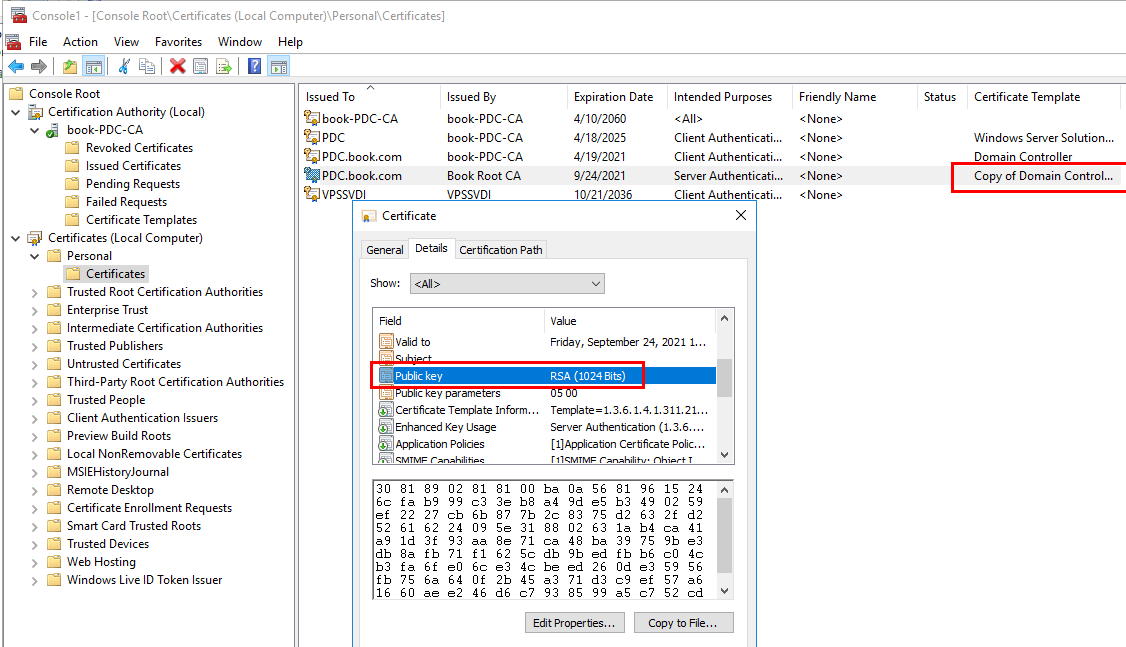
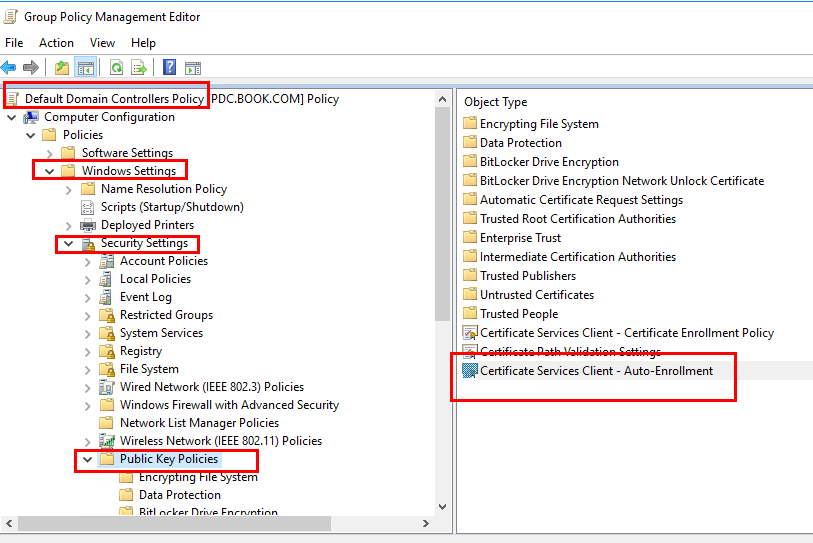
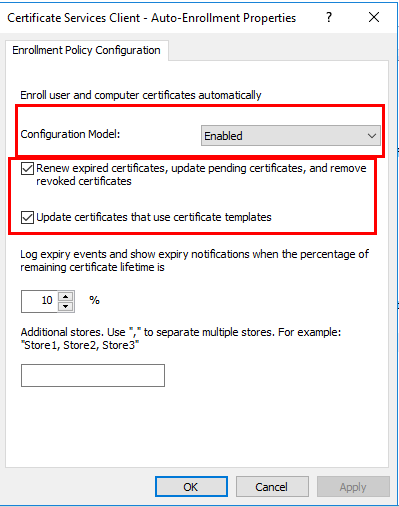
If we set the auto enrollment, please make sure that the duplicated domain controller certificate template had the autoenroll permission set. And then we should use Reenroll All Certificate Holders to cause the servers to reenroll and request a different key size (assuming certificate autoenrollnent is enabled).
We could refer to the below article about this:
For any question, please feel free to contact us.
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.