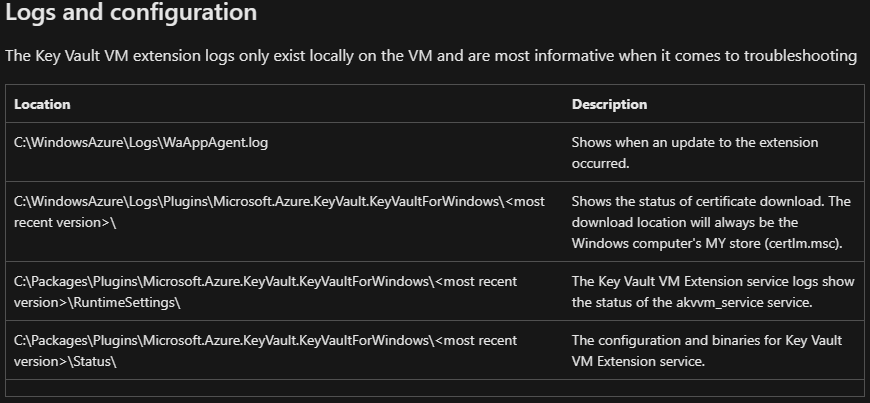
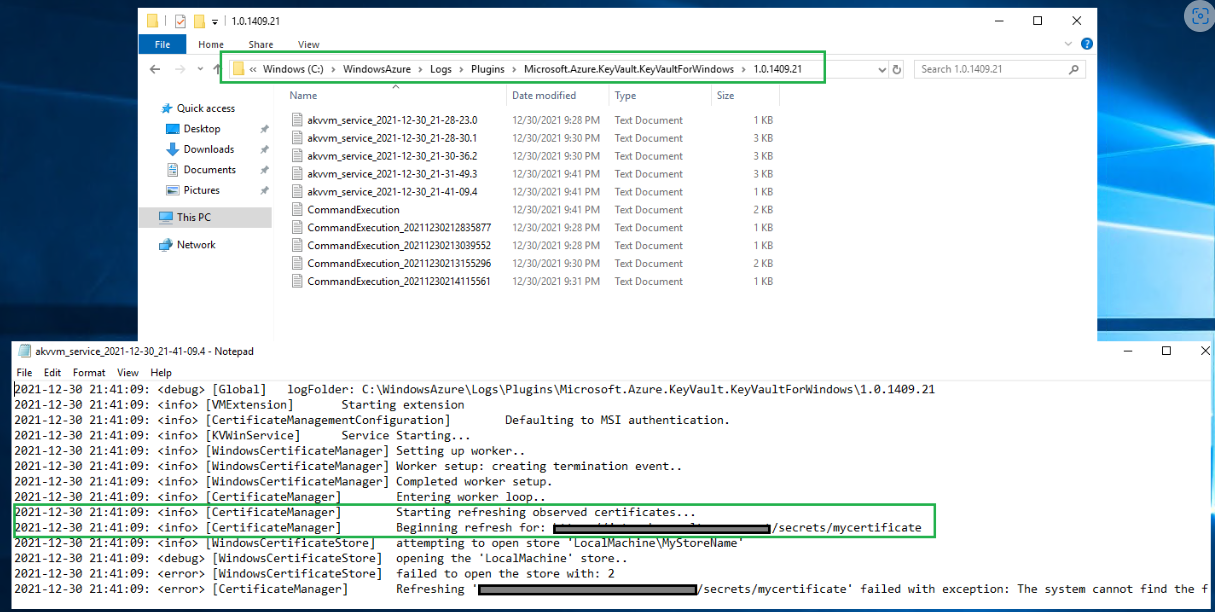
Azure KeyVault VM extension now supports writing events to log and hence new certificate would be automatically updated.
Microsoft-Windows-CertificateServicesClient-Lifecycle-System/Operational
Can the Azure Key Vault VM Extension be configured to write events to the event log "Microsoft-Windows-CertificateServicesClient-Lifecycle-System/Operational" ?
End goal - I want to automate certificate renewal and rebind in IIS, using certificates from an Azure Key Vault. i.e. When a cert is renewed in the key vault, the cert should get pushed/pulled to the VM, then the IIS binding should swap to the newer certificate.
I've already setup and tested the Azure Key Vault VM Extension to watch a particular certificate, and I've enabled Automatic Rebind of Renewed Certificate in IIS.
The problem is that when the Key Vault VM Extension pulls over a newer version of the certificate, it's not writing the expected event 1001 (or any event) to the Event Log watched by the Task created by Automatic Rebind.
Am I missing something here? Or is there a better way to accomplish this goal?
Documentation I'm basing my goal on:
https://learn.microsoft.com/en-us/azure/virtual-machines/extensions/key-vault-windows
https://learn.microsoft.com/en-us/iis/get-started/whats-new-in-iis-85/certificate-rebind-in-iis85
-
Aquib Qureshi 81 Reputation points Microsoft Employee
2023-11-10T14:58:37.0633333+00:00
1 additional answer
Sort by: Most helpful
-
 JamesTran-MSFT 36,371 Reputation points Microsoft Employee
JamesTran-MSFT 36,371 Reputation points Microsoft Employee2022-12-22T23:11:22.377+00:00 @Bollwerk, Pete
Thank you for your time and patience on this issue!I received a response from our Key Vault engineering team and when it comes to IIS automatic rebinding, the Key Vault VM Extension doesn't support this because it requires Certificate Services Lifecycle Notifications, and the KV VM extension doesn't write a certificate-renewal event (event ID 1001) whenever a new version comes.
Due to the KV VM extension not writing a certificate-renewal event, you should be able to leverage the
linkOnRenewalproperty within the Key Vault VM Extension schema. Upon installation, when thelinkOnRenewalproperty is set totrue, the previous version of a certificate is chained to its successor via theCERT_RENEWAL_PROP_ID(certificate extension property). This chaining enables S-channel to pick up the most recent/farthest valid certificate with a matching SAN. This feature enables auto-rotation of SSL certificates, without necessitating a re-deployment or binding.Note: Please make sure you set the SAN, and the KV VM Extension links the certificate strictly by SAN. This feature doesn’t require re-binding. You might see the binding in IIS still pointing to the older version, but IIS will auto pick up the latest version via S-channel."properties": { "publisher": "Microsoft.Azure.KeyVault", "type": "KeyVaultForWindows", "typeHandlerVersion": "1.0", "autoUpgradeMinorVersion": true, "settings": { "secretsManagementSettings": { "pollingIntervalInS": <string specifying polling interval in seconds, e.g: "3600">, "certificateStoreName": <certificate store name, e.g.: "MY">, "linkOnRenewal": <Only Windows. This feature ensures s-channel binding when certificate renews, without necessitating a re-deployment. e.g.: false>, "certificateStoreLocation": <certificate store location, currently it works locally only e.g.: "LocalMachine">, "requireInitialSync": <initial synchronization of certificates e..g: true>, "observedCertificates": <list of KeyVault URIs representing monitored certificates, e.g.: "https://myvault.vault.azure.net/secrets/mycertificate" }When it comes to the KV VM extension writing events to the
Microsoft-Windows-CertificateServicesClient-Lifecycle-System/Operationallog, I noticed that you leveraged our User Voice forum and created a feature request - I've also created an internal feature request, so our engineering team can look into implementing this.I hope this helps!
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.