I am encountering an issue while trying to access call records using Microsoft Graph API. The error I am receiving is a 403 Forbidden error. I have granted all the necessary permissions, including 'CallRecords.Read.All,' and consent has been given. However, the issue persists.
Error Message:
Error: 403 Forbidden {"error":{"code":"Forbidden","message":"","innerError":{"request-id":"022bc9fa-476e-481b-a53c-c3c67770f9fd","date":"2024-01-03T04:46:31","client-request-id":"022bc9fa-476e-481b-a53c-c3c67770f9fd"}}}
Steps Taken:
- Checked and granted required permissions in Azure AD portal.
- Ensured 'CallRecords.Read.All' scope in the authorization request.
- Verified admin consent.
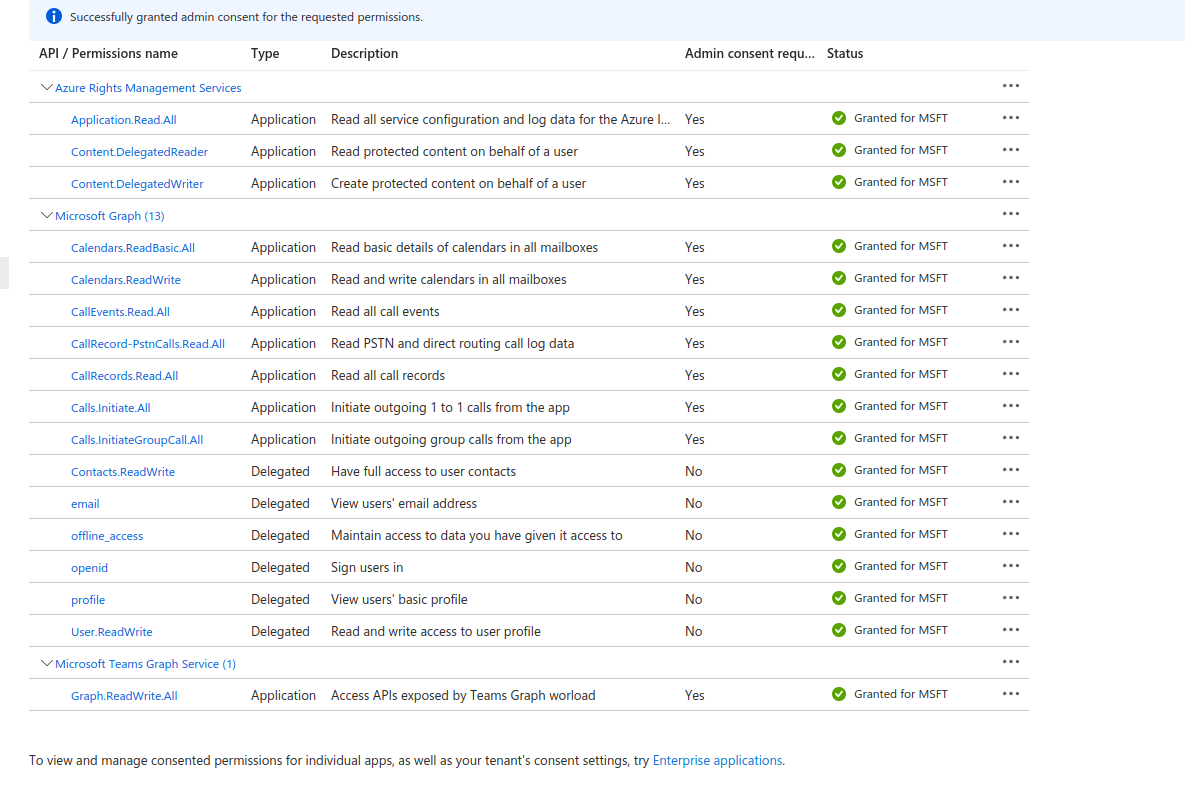
Environment:
- Graph API Version: v1.0
- Account Type: Microsoft 365 developer account
Facing 403 Forbidden error. Any insights on resolution? Considerations like licensing in a dev environment?
..It feels it only gives Delegate Permissions not Application Permissions ?

