Hi @Dhanalakshmi-9499
Welcome to the Microsoft Q&A and thank you for posting your questions here.
Your question is to know how to create policies in Azure, especially a policy to Inherit the tags from Resource Group to Resources and policy to allow only listed tag values.
This a require a few steps you might need to follow. You can use Azure Portal or Implement it using JSON file.
Sequel to your first question on Inheriting Tags from Resource Group to Resources:
Step 1: Create the Policy Definition:
- Go to the Azure Portal .
- Navigate to "All services" > "Policy" or search for "Policy" as in fig1. After click on Policy, In Policy Page by Authoring Pane, click on "Definitions".
-
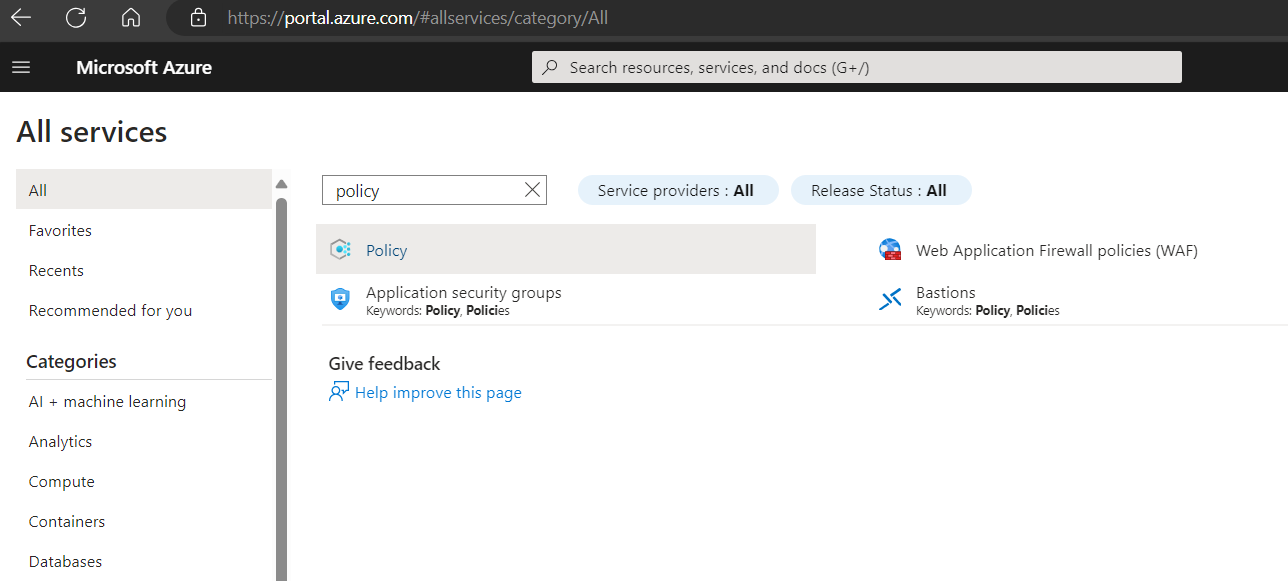
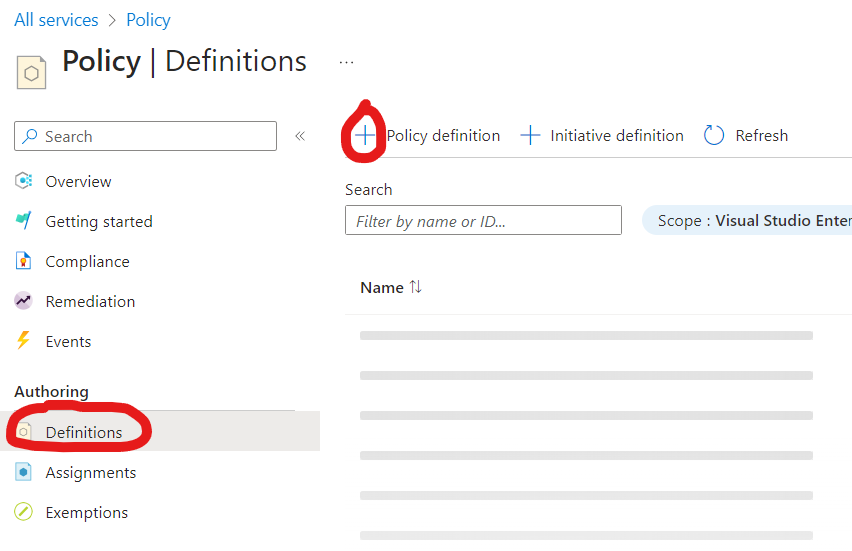
- Click on "+ Policy definition" to create a new policy definition.
- Enter a name for your policy definition (e.g., "Inherit Tags from Resource Group").
- Definition location Should be your Subscription Level where you have the Resources group. You will click on Launch Scope Selector as in the fig. below.
-
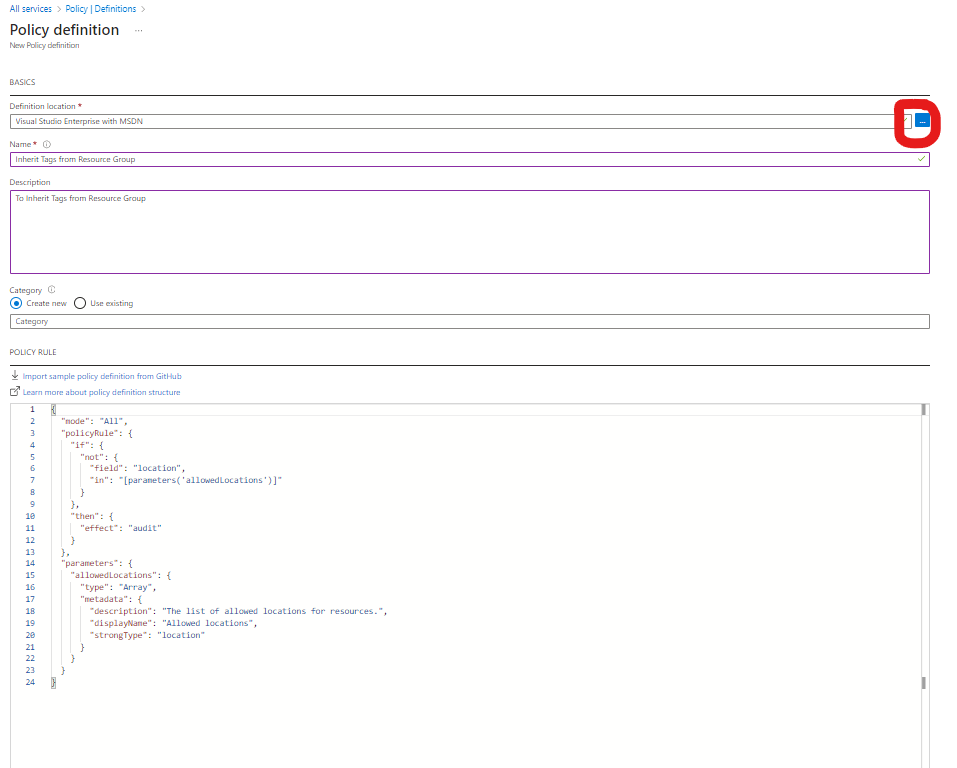
Provide all necessary information and notice your policy written in JSON. You can modify the code to suite your need as shown below:
{
"mode": "Indexed",
"policyRule": {
"if": {
"field": "tags",
"exists": "false"
},
"then": {
"effect": "deployIfNotExists",
"details": {
"type": "Microsoft.Resources/tags",
"existenceCondition": {
"allOf": [
{
"field": "Microsoft.Resources/tags[tagName]",
"equals": "tagValue"
}
]
},
"roleDefinitionIds": [
"/providers/Microsoft.Authorization/roleDefinitions/{roleDefinitionId}"
],
"tagDetails": {
"tagName": "tagValue"
}
}
}
},
"parameters": {
"roleDefinitionId": {
"type": "String",
"metadata": {
"displayName": "Role Definition ID",
"description": "The ID of the role definition for assigning tags to resources"
}
}
}
}
- NOTE: In this policy above:
"tagDetails" specifies the tag name (tagName) and its value (tagValue) that you want to inherit.
"roleDefinitionIds" specifies the role definition ID that has permission to assign tags to resources.
- Save the Policy. After you will see the next page similar to the below page.
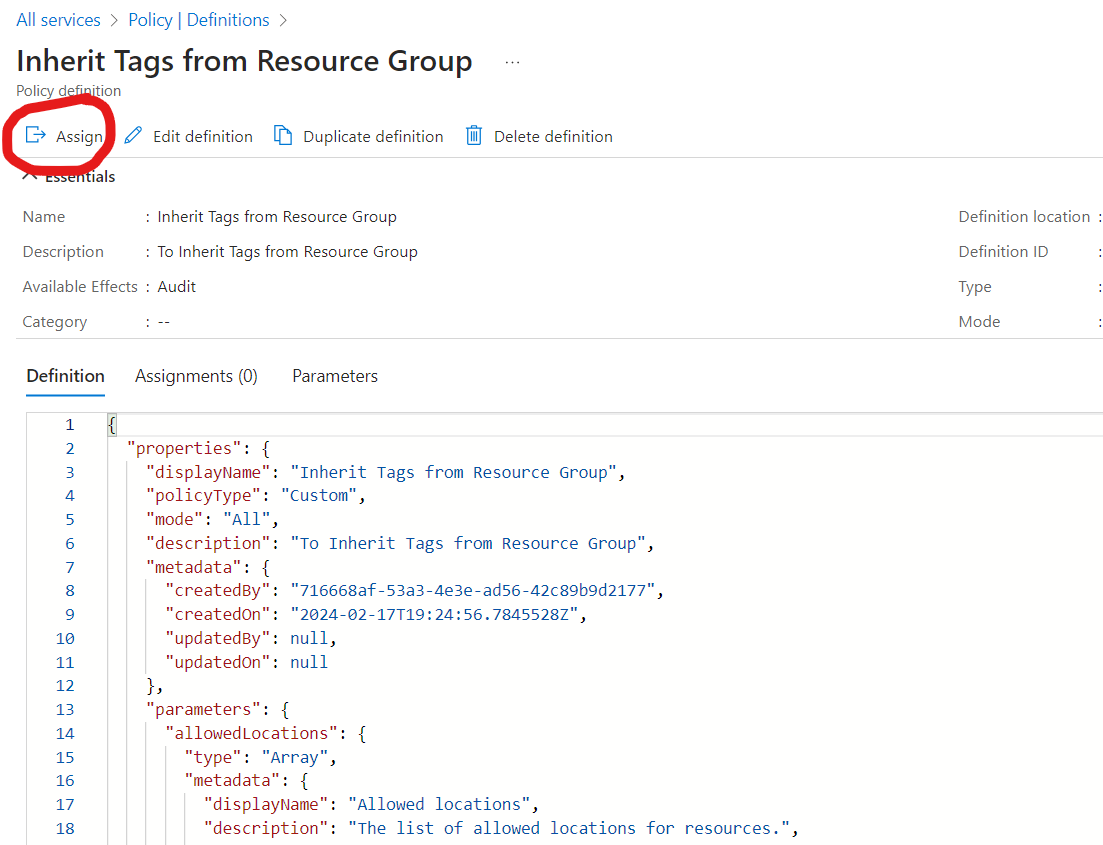 Continue with step 2.
Step 2: Assign the Policy:
Continue with step 2.
Step 2: Assign the Policy:
- After creating the policy definition, In the "All services" > "Policy" > "Assignments" page as seen above. Click on "+ Assign" to assign a new policy.
- Select the scope for the policy assignment (e.g., subscription, resource group).
- Choose the policy definition you created earlier from the "Policy definition" dropdown.
- Configure any additional parameters required by the policy definition (e.g., Role Definition ID).
- Click on "Review + create", then "Create" to assign the policy.
On your second question to Allow Only Listed Tag Values.
- Follow the same steps as above to create a new policy definition.
Enter a name for your policy definition (e.g., "Allowed Tag Values").
- Paste / Import the JSON policy definition similar to the below:
{
"mode": "All",
"parameters": {
"allowedTagValues": {
"type": "Array",
"metadata": {
"displayName": "Allowed Tag Values",
"description": "The list of allowed tag values"
}
}
},
"policyRule": {
"if": {
"allOf": [
{
"field": "tags",
"exists": "true"
},
{
"not": {
"field": "tags['tagName']",
"in": "[parameters('allowedTagValues')]"
}
}
]
},
"then": {
"effect": "deny"
}
}
}
In the above policy NOTE "allowedTagValues" parameter specifies the list of allowed tag values.
"tagName" should be replaced with the actual name of the tag you want to restrict.
As previous steps, after creating the policy definition, in the same navigation page to "All services" > "Policy" > "Assignments". Assign the Policy.
- Select the appropriate scope for the policy assignment.
- Choose the policy definition you created earlier from the "Policy definition" dropdown.
- Configure any additional parameters required by the policy definition (e.g., Allowed Tag Values).
- Click on "Review + create", then "Create" to assign the policy.
Notes:
Ensure that you have the necessary permissions (e.g., Owner, Contributor) to create and assign policies. Take into consideration the scope of the policy assignment to apply the policy at the desired level (subscription, resource group). Make sure to review the policy definitions and assignments carefully before creating them to ensure they meet your requirements.
I hope this is helpful! Do not hesitate to let me know if you have any other questions.
Please remember to "Accept Answer" if answer helped, so that others in the community facing similar issues can easily find the solution.
Best
