Hello Alberto Porro,
Greetings! Welcome to Micrsoft Q&A Platform.
Azure Storage supports using Microsoft Entra ID to authorize requests to blob data. With Microsoft Entra ID, you can use Azure role-based access control (Azure RBAC) to grant permissions to a security principal, which may be a user, group, or application service principal.
the error message “Selected user account does not exist in tenant ‘Microsoft Services’ and cannot access the application,” it suggests that the Microsoft personal account is not recognized within the specified tenant. Verify that the tenant configuration allows external users to be added and confirm that the Microsoft personal account is indeed added as an external user in the tenant.
Also add the user to the application that they trying to access- https://learn.microsoft.com/en-us/entra/external-id/add-users-administrator#add-guest-users-to-a-group After a guest user has been added to the directory in Microsoft Entra ID, an application owner can send the guest user a direct link to the app they want to share.
This guide provides the basic steps to invite an external user. To learn about all of the properties and settings that you can include when you invite an external user, see How to create and delete a user.
Once your Guest account has accepted the invite (through Azure AD Users), and once you granted access to this Guest to your desired application, you will receive an email with a link in it that will bring the user to myapps.microsoft.com once you accept the terms by looking at the top right corner of the screen, you will see a button that looks like this:
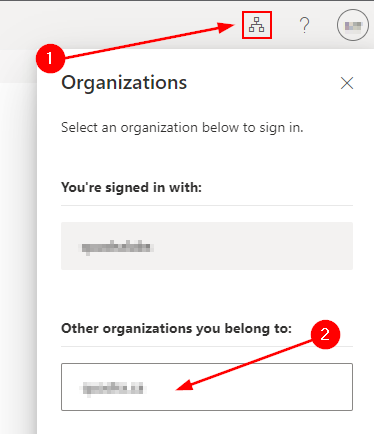
Ensure that once you received the email to your Guest account you need to click on the organization that you want to a view with the apps shared from. Also, once you grant access to an application it can take some time to show for your users.
Alternatively, If the user account is created for only accessing storage account then you try to Create SAS tokens for your storage containers with desired permissions and share it with your users and User should install the Storage Explorer and connect to the Blob container with provided SAS tokens to upload the files.
Step:1 Create SAS tokens in the Azure portal.
Go to the Azure portal and navigate to your container (Your storage account → containers → your container)
- Generate SAS from the drop-down menu.
- Define Permissions by checking and/or clearing the appropriate check box:
- Your target container or file must have designated read, create, write and list access to upload the files to the container.
- Specify the signed key Start and Expiry times.
- Review then select Generate SAS token and URL.
- The Blob SAS token query string and Blob SAS URL will be displayed in the lower area of window.
- Copy and paste the Blob SAS token and URL values in a secure location. They'll only be displayed once and cannot be retrieved once the window is closed.
Step:2 Connect to the blob container using the SAS url using Storage Explorer
- In the Select Resource panel of the Connect to Azure Storage dialog, select the blob Container.
- Select Shared access signature (SAS) and select Next.
- Enter a display name for your connection and the SAS URI for the resource. Select Next.
- Review your connection information in the Summary panel. If the connection information is correct, select Connect.Better way is to Create SAS tokens for your storage containers with desired permissions and share it with your users and User should install the Storage Explorer and connect to the Blob container with provided SAS tokens to upload the files. Step:1 Create SAS tokens in the Azure portal. Go to the Azure portal and navigate to your container (Your storage account → containers → your container)
- Generate SAS from the drop-down menu.
- Define Permissions by checking and/or clearing the appropriate check box:
- Your target container or file must have designated read, create, write and list access to upload the files to the container.
- Specify the signed key Start and Expiry times.
- Review then select Generate SAS token and URL.
- The Blob SAS token query string and Blob SAS URL will be displayed in the lower area of window.
- Copy and paste the Blob SAS token and URL values in a secure location. They'll only be displayed once and cannot be retrieved once the window is closed.
Step:2 Connect to the blob container using the SAS url using Storage Explorer
- In the Select Resource panel of the Connect to Azure Storage dialog, select the blob Container.
- Select Shared access signature (SAS) and select Next.
- Enter a display name for your connection and the SAS URI for the resource. Select Next.
- Review your connection information in the Summary panel. If the connection information is correct, select Connect.
Similar thread for reference - https://learn.microsoft.com/en-us/answers/questions/1339578/guest-access-for-azure-data-lake-gen-2
Hope this answer helps! Please let us know if you have any further queries. I’m happy to assist you further.
Please "Accept the answer” and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.