Yes you can do this. It is a bit tricky. You can prevent users from even trying to authenticate but only through the WAP. Which shouldn't be am issue as you aren't supposed to expose your ADFS to the Internet without a WAP anyways.
So when you enable the Extranet Lockout Protection, whether it is the 2012 R2 way or the 2016 way, the first thing the ADFS service account will do is look up the user in AD. If that call fails, the password provided at the time is not even tried. Preventing brute-force, password sprays and other guessing attempts (well also preventing even legit attempts from this user).
So if you can add a specific ACE on the users account you want to make invisible for ADFS. Something like this:
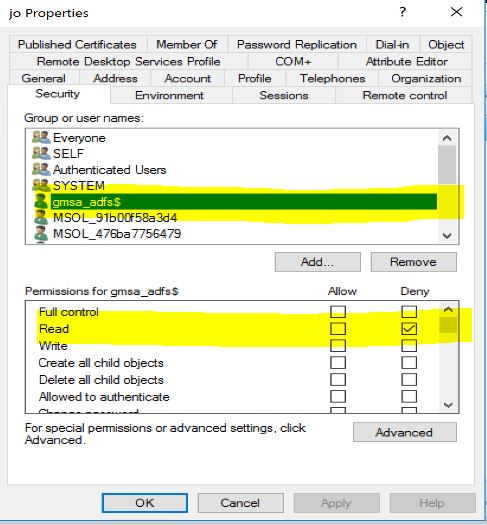
Then ADFS will have no clue the user exist and will fail right away. You can see the following error message in the debug logs:
ADNameTranslator.NameTranslateWithReferral: unable to resolve name v\jo , result code DS_NAME_ERROR_NOT_FOUND
ActiveDirectoryAccountStore - Name v\jo could not be translated to DN. Account is likley non-existent.
MsisLocalCpUserNameSecurityTokenHandler::UpdateAuthenticationContext: Identity v\jo Failed with exception: Microsoft.IdentityServer.Service.AccountPolicy.ADAccountLookupException: MSIS8022: Unable to find the specified user account.
But administrative accounts are usually protected by the adminSDHolder. Any additional ACEs will be remove within the hour unless you also add this ACE in the adminSDHolder container security descriptor. So you will be impacting all protected accounts and might have some undesirable side effects if some of your regular accounts also are privileged (which should not happened anyways, but who knows). You can try to evaluate the impact of adding the deny ACE aforementioned on the adminSDHolder object by running this command:
Get-ADUser -LDAPFilter "(&(objectClass=user)(objectCategory=person)(adminCount=1))"
This will give you the list of all currently protected user accounts in your domain.

