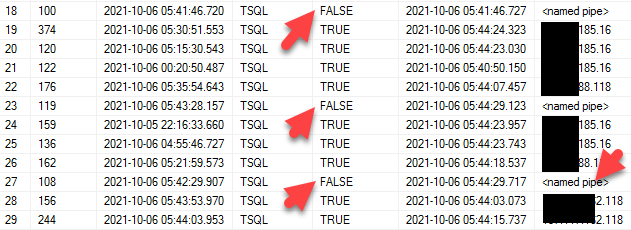
All connections coming from SSMS to Azure SQL are encrypted even if the you don't set "Encrypt connection" setting on. Azuire SQL Database only allows encrypted connections.
When a client first attempts a connection to SQL Azure, it sends an initial connection request. Consider this a "pre-pre-connection" request. At this point the client does not know if SSL/Encryption is required and waits an answer from SQL Server/SQL Azure to determine if SSL is indeed required throughout the session (not just the login sequence, the entire connection session). A bit is set on the response indicating so. Then the client library disconnects and reconnects armed with this information.
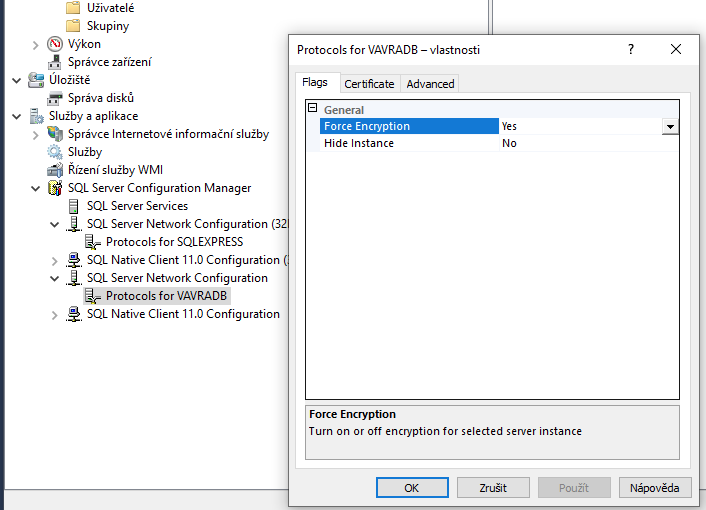
When you set "Encrypt connection" setting on SSMS you avoid the "pre-pre-connection", you are preventing any proxy from turning off the encryption bit on the client side of the proxy, this way attacks like man-in-the-middle attack are avoided.
When secure connections are needed, please enable "Encrypt connection" setting.
You can run the following command to verify all connections to Azure SQL are encrypted:
select * from sys.dm_exec_connections.