Hello,
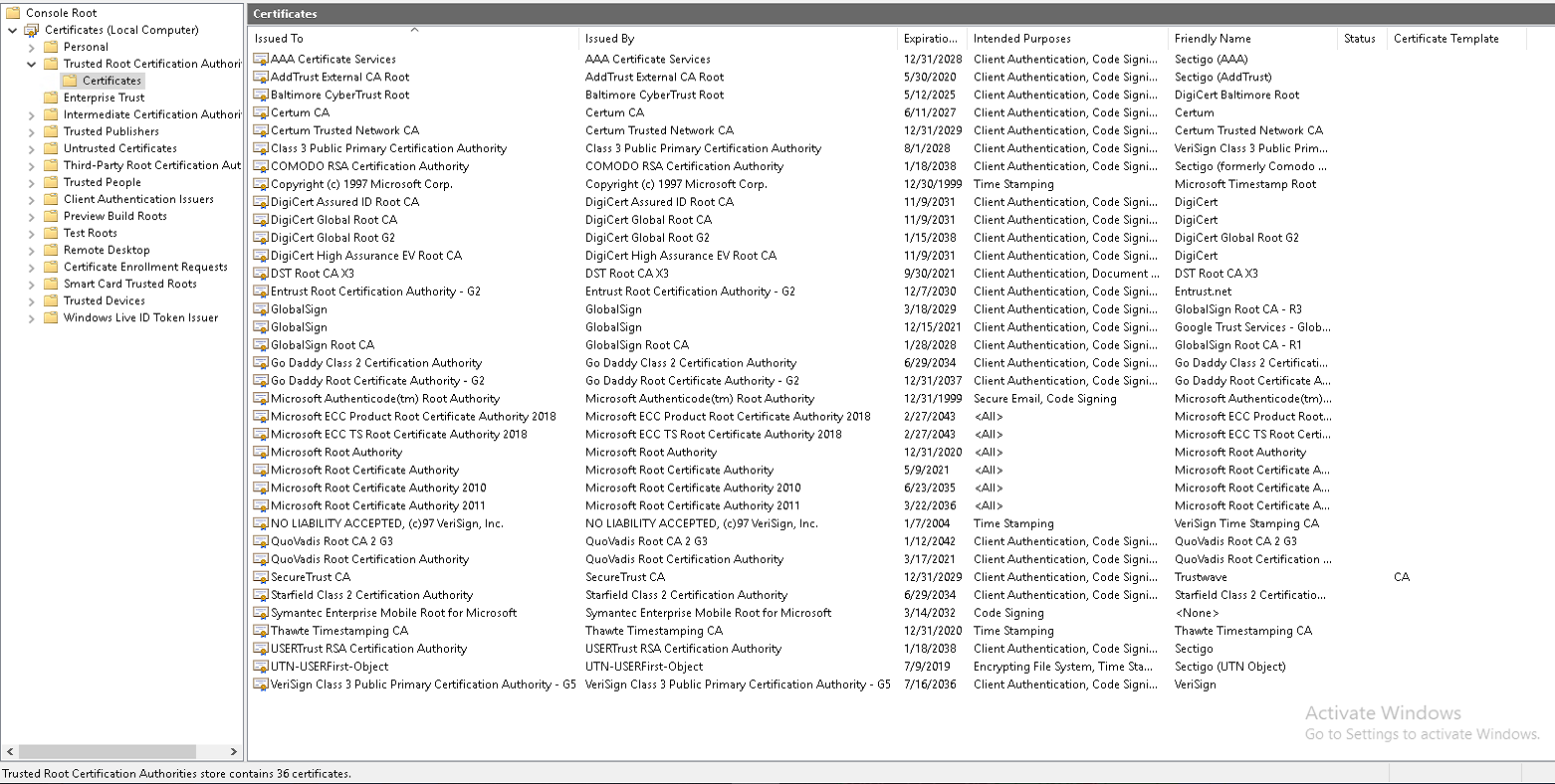
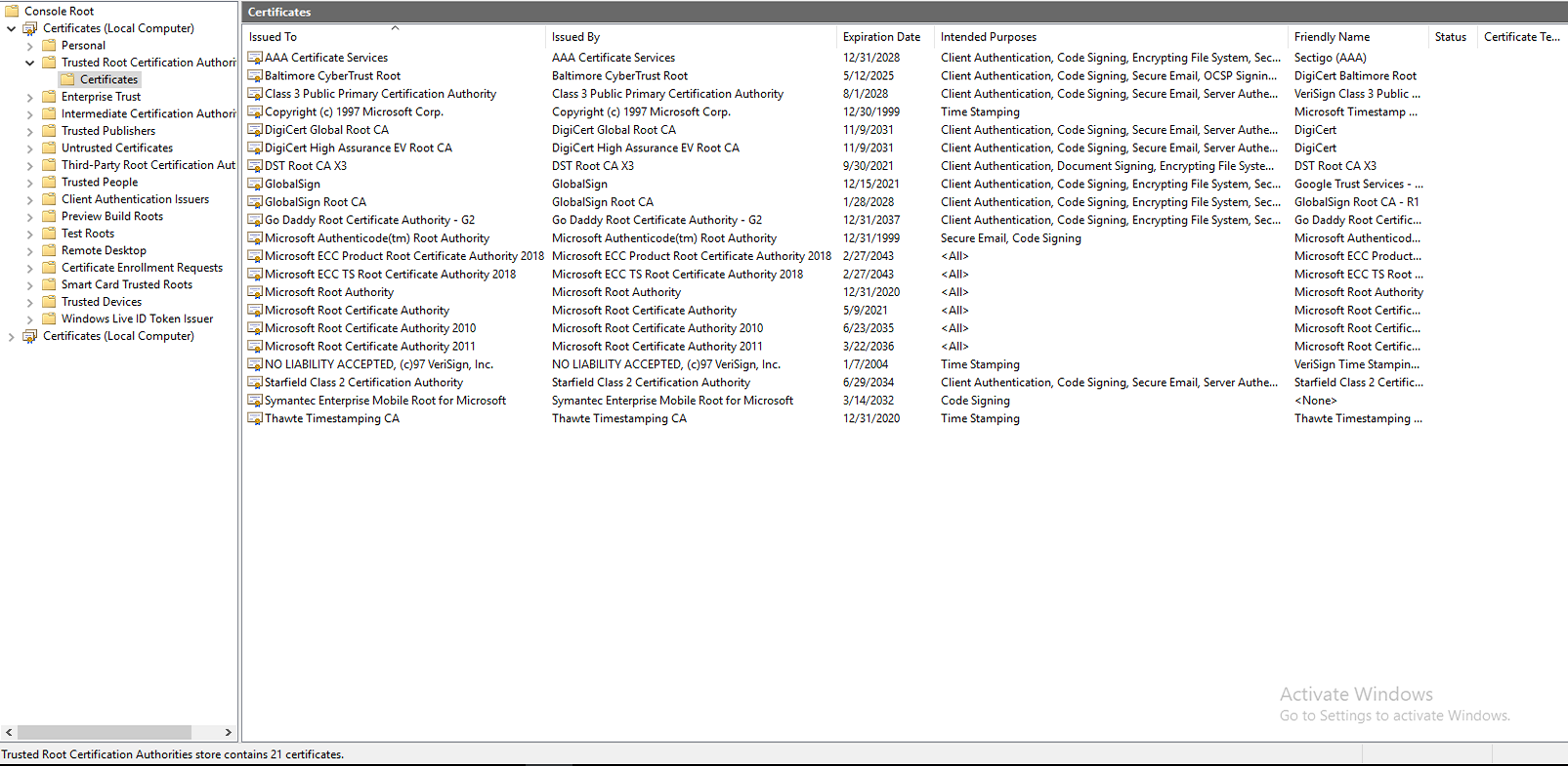
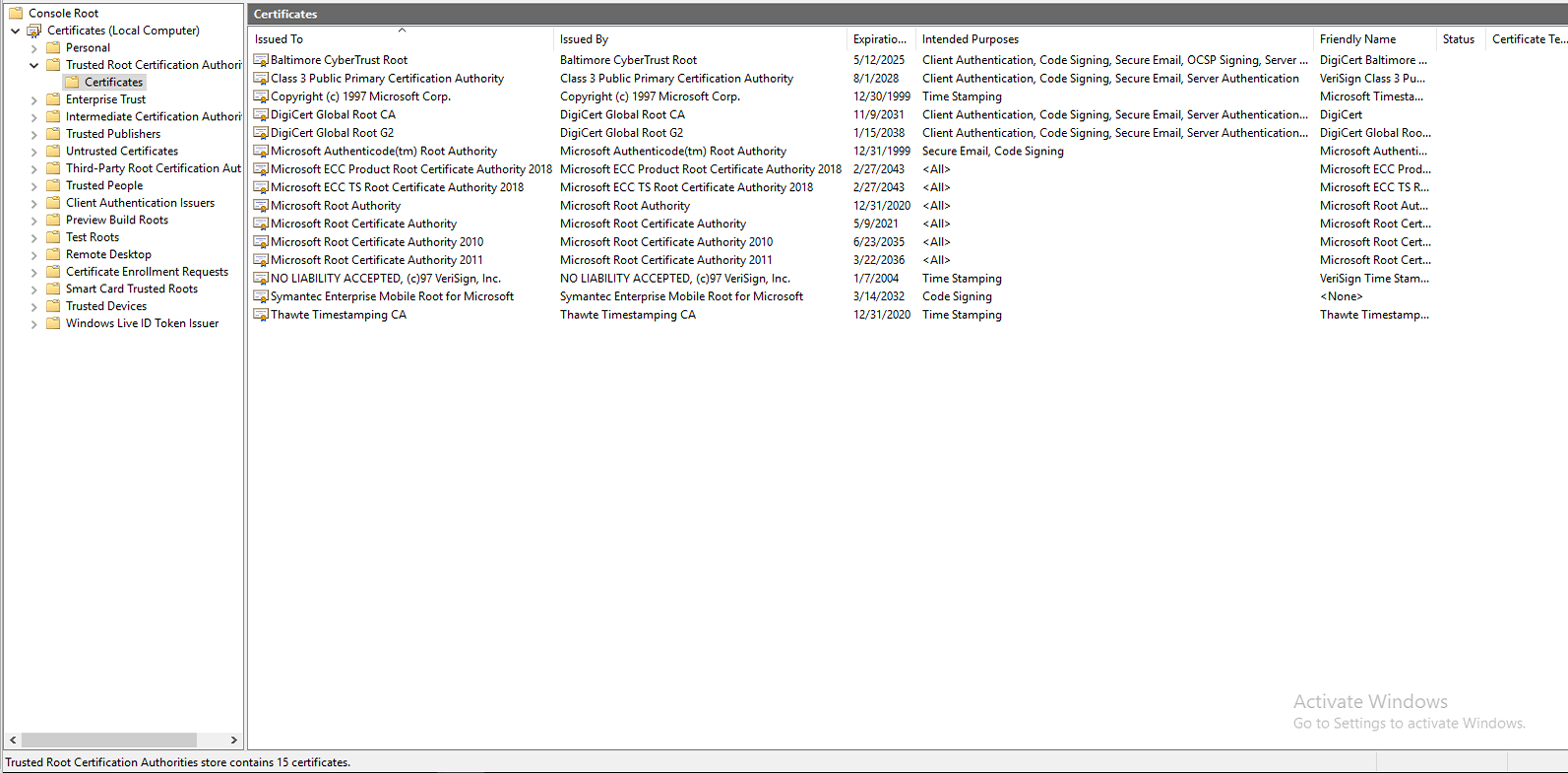
Very simple: 3 Windows 2019 servers, all installed at the same time with the same media. Create new domain on one DC (first image). Then promote the other two servers to DCs in the new domain. All done in a couple of hours. Issue visible immediately. Nothing else was done, nothing installed, nothing removed, no GPOs, nothing
No issue at this point, just trying to understand why in case there is a cert issue in the future, I've noticed this many times over the years in other domains, I just assumed in the past that some work was done that would cause the number of Trusted CA certs to vary between DCs but I don't think that's the case now. Please see attached screen shots