Hello @Rakesh S , Thanks for reaching out.
Could you confirm type of certificate trying to import? Azure Key Vault supports .pem and .pfx certificate files for importing Certificates into Key vault. We support the following type of Import for PEM file format. A single PEM encoded certificate along with a PKCS#8 encoded, unencrypted key which has the following
-----BEGIN CERTIFICATE----- -----END CERTIFICATE-----
-----BEGIN PRIVATE KEY----- -----END PRIVATE KEY-----
When you are importing the certificate, you need to ensure that the key is included in the file itself. If you have the private key separately in a different format, you would need to combine the key with the certificate. Some certificate authorities provide certificates in different formats, therefore before importing the certificate, make sure that they are either in .pem or .pfx format. To learn more refer this article.
**Sample REST API call for importing .PFX certificate format: **
You must pass .pfx certificate in base64-encoded-byte format inside the “value:” parameter of POST request in the body section, use following PowerShell cmdlet for converting pfx file into base64-encoded-byte format.
- $fileContentBytes = get-content "C:\newfolder\cert.pfx" -Encoding Byte
- [System.Convert]::ToBase64String($fileContentBytes) | Out-File "c:\newfolder\pfx-base64-encoded-bytes.txt"
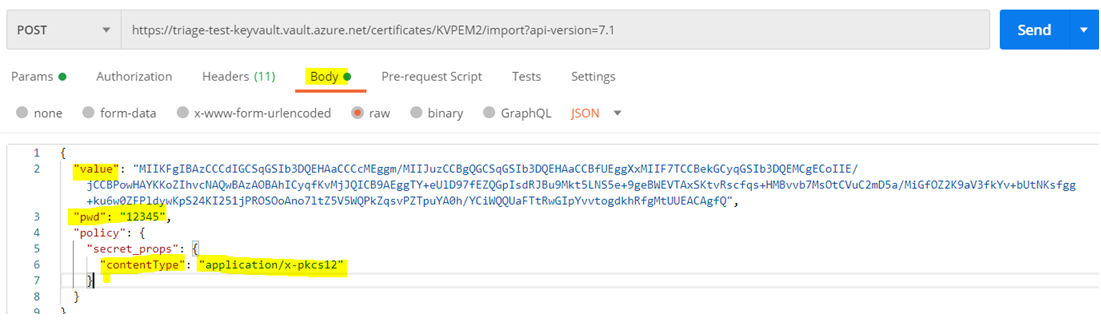
Once converted, just copy base64-encoded value and add them in the “value:” parameter. The "contentType" must be "application/x-pkcs12" and If the private key in base64EncodedCertificate is encrypted then mentioned in request body as shown below..
Sample Request
POST https://myvault.vault.azure.net/certificates/importCert01/import?api-version=7.1
Request Body
{
"value": "MIIKFgIBAzCCCdIGC----------------------SqGSIb3DQEHAaCCCcMEggm",
"pwd": "12345",
"policy": {
"secret_props": {
"contentType": "application/x-pkcs12"
}
}
}
Screenshot:
Note: "key_props parameters ("exportable": true , "kty": "RSA", "key_size": 2048 and "reuse_key": false) are optional one, if require then you can add them in the request body
**Sample REST API call for importing .PEM certificate format: **
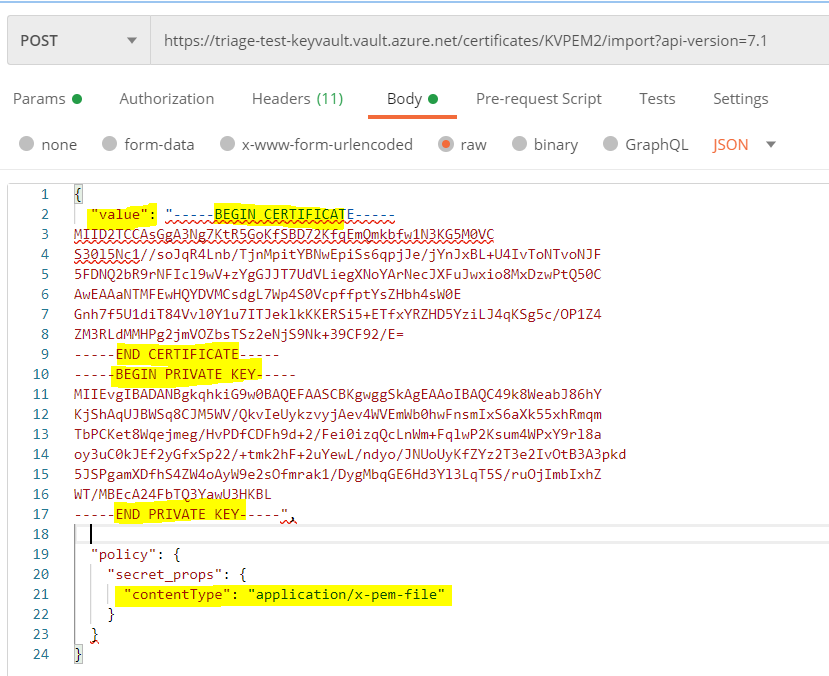
If you’re importing a certificate in PEM format, then "contentType" should be "application/x-pem-file" type. The value parameter will just be the raw text contents of your PEM file and need not to be in base64-encoded-byte, because PEM cert is already a text format, so base64-encoding doesn’t require.
Sample Request
POST https://myvault.vault.azure.net/certificates/importCert01/import?api-version=7.1
Request Body
{
"value": "-----BEGIN CERTIFICATE-----
MIID2TCCAsGgA3Ng7KtR5GoKfSBD72KfqEmQmkbfw1N3KG5M0VC
S30l5Nc1//soJqR4Lnb/TjnMpitYBNwEpiSs6qpjJe/jYnJxBL+U4IvToNTvoNJF
5FDNQ2bR9rNFIcl9wV+zYgGJJT7UdVLiegXNoYArNecJXFuJwxio8MxDzwPtQ50C
AwEAAaNTMFEwHQYDVMCsdgL7Wp4S0VcpffptYsZHbh4sW0E
Gnh7f5U1diT84Vvl0Y1u7ITJeklkKKERSi5+ETfxYRZHD5YziLJ4qKSg5c/OP1Z4
ZM3RLdMMHPg2jmVOZbsTSz2eNjS9Nk+39CF92/E=
-----END CERTIFICATE-----
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQC49k8WeabJ86hY
KjShAqUJBWSq8CJM5WV/QkvIeUykzvyjAev4WVEmWb0hwFnsmIxS6aXk55xhRmqm
TbPCKet8Wqejmeg/HvPDfCDFh9d+2/Fei0izqQcLnWm+FqlwP2Ksum4WPxY9rl8a
oy3uC0kJEf2yGfxSp22/+tmk2hF+2uYewL/ndyo/JNUoUyKfZYz2T3e2IvOtB3A3pkd
5JSPgamXDfhS4ZW4oAyW9e2sOfmrak1/DygMbqGE6Hd3Yl3LqT5S/ruOjImbIxhZ
WT/MBEcA24FbTQ3YawU3HKBL
-----END PRIVATE KEY-----",
"policy": {
"secret_props": {
"contentType": "application/x-pem-file"
}
}
}
Screenshot:
**There are a few separate issues here you need to be very careful about: **
• Private Key Format A certificate with a private key in a PEM file could have the key stored in various format. One very common one is PKCS#1, which is identified by the key being wrapped in -----BEGIN RSA PRIVATE KEY----- and -----END RSA PRIVATE KEY-----.
If you try to import such a certificate to Key Vault, however, you will get an error. This is because Key Vault will only accept a key in PKCS#8 format, which you will recognize because it’s wrapped in -----BEGIN PRIVATE KEY----- and -----END PRIVATE KEY-----.
You can easily use the openssl pkcs8 -topk8 command to convert the private key once you know to do this.
• Value Format The result is that the value parameter will just be the raw text contents of your PEM file. The content must use UNIX-style line separators (\n). Attempting to send the content using Windows-style line endings (\r\n) will just result in a confusing error such as The specified PEM X.509 certificate content is in an unexpected format. Please check if certificate is in valid PEM format.
Another common reason for the import to fail is that when you openssl to create/convert to PEM format cert, which add certain commentary text in the .pem file. For example, if you convert a PFX to a PEM using the below command:
openssl pkcs12 -in cert.pfx -out cert.pem
Then using "cat cert.pem", you might see something like:
Bag Attributes
localKeyID: D4 2F E7 46 EA BC 7F 00 35 1F 1A 2F 33 07 81 5F 31 7F 90 E7
subject=/CN=example.com
issuer=/CN=example.com
-----BEGIN CERTIFICATE-----
(etc)
Azure Key Vault does not understand any text in the .pem file that is not between -----BEGIN etc----- and -----END etc----- marks.
You can try to avoid these comments by concatenating the certificate (i.e. public key) and the private key together in a cat command:
openssl req -newkey rsa:2048 -new -nodes -x509 -days 3650 -keyout key.pem -out cert.pem
cat cert.pem key.pem > tobeimported.pem
The above command will produce a tobeimported.pem file that Key Vault understands.
Reference: https://github.com/MicrosoftDocs/azure-docs/issues/23558
--------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
