On this page https://learn.microsoft.com/en-us/entra/identity-platform/permissions-consent-overview?WT.mc_id=Portal-Microsoft_AAD_RegisteredApps#administrator-consent
they say:
Permission requests that contain custom application scopes aren't considered high-privilege and thus, they don't require admin consent.
Therefore, if you create a custom permission for your app and request that alongside the other scopes, you don't need admin consent.
# given some application
resource "azuread_application" "example" {
display_name = "example"
identifier_uris = ["api://example"]
}
# we create a custom scope for it
resource "random_uuid" "custom_scope" {}
resource "azuread_application_permission_scope" "custom" {
application_id = azuread_application.example.id
scope_id = random_uuid.custom_scope.id
value = "Custom"
admin_consent_display_name = "Bypass admin consent"
admin_consent_description = join("", [
"By requesting this scope, admin consent is bypassed, according to: ",
"https://learn.microsoft.com/en-us/entra/identity-platform/permissions-consent-overview?WT.mc_id=Portal-Microsoft_AAD_RegisteredApps#administrator-consent",
])
}
# and we grant the application access to it
resource "azuread_application_api_access" "custom_scope" {
application_id = azuread_application.example.id
api_client_id = azuread_application.example.client_id
scope_ids = [random_uuid.custom_scope.id]
}
# we can asign any other scope to the application, for example for oidc
data "azuread_application_published_app_ids" "well_known" {}
data "azuread_service_principal" "msgraph" {
client_id = data.azuread_application_published_app_ids.well_known.result["MicrosoftGraph"]
}
resource "azuread_application_api_access" "msgraph" {
application_id = azuread_application.example.id
api_client_id = data.azuread_service_principal.msgraph.client_id
scope_ids = [
data.azuread_service_principal.msgraph.oauth2_permission_scope_ids["openid"],
data.azuread_service_principal.msgraph.oauth2_permission_scope_ids["email"],
data.azuread_service_principal.msgraph.oauth2_permission_scope_ids["profile"],
]
}
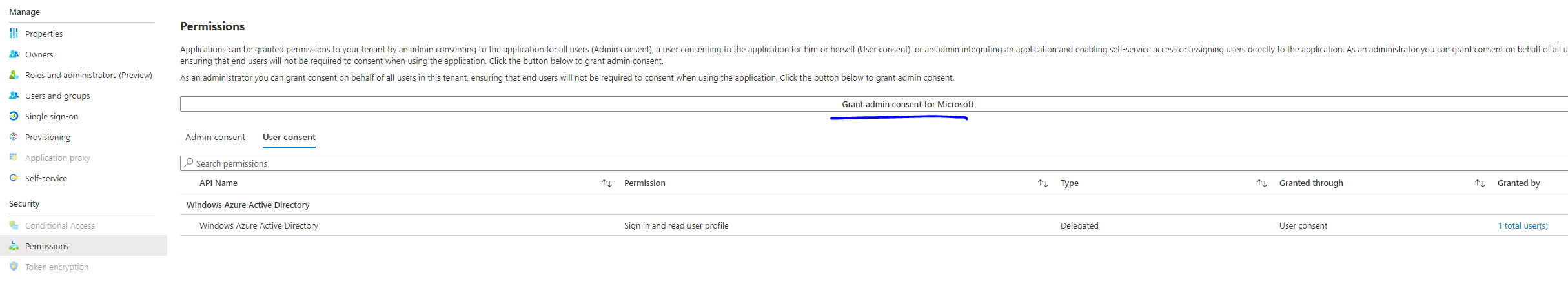
When configuring the client application, we can request the scopes, alongside the custom one in order to bypass the admin consent:
clientId: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
clientSecret: xyz
scopes:
- api://example/Custom # <-
- openid
- email
- profile
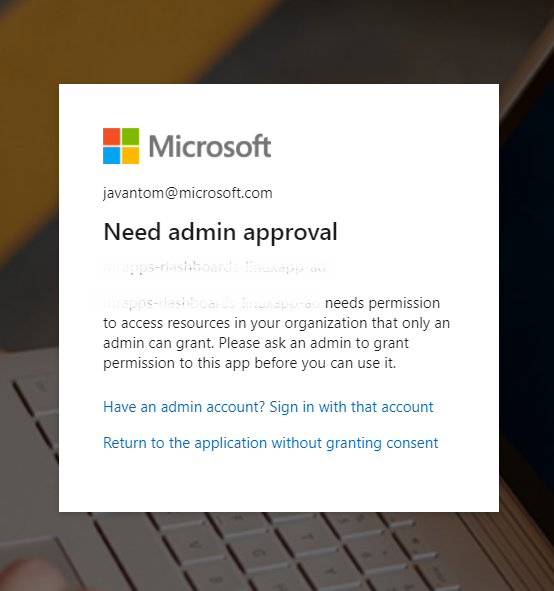
That said, I am wondering why it is like that. This seems like a foot gun. Like people accidentally disabling admin consent. Or the custom scope is really just for that, but then it is a strange way of implementing the consent bypass feature.
In my case, I don't even understand why this is required. Because the scope in the list are marked as "no admin consent required", in the UI.
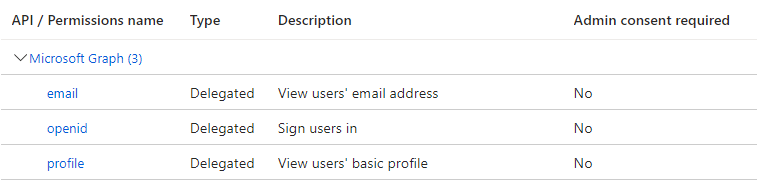
But in fact, I ran into the issue. That's why I'm here.