Thank you Karlie,
The document you provided is useful and very similar instructions to what I have used to configure one RD gateway and central NPS server successfully.
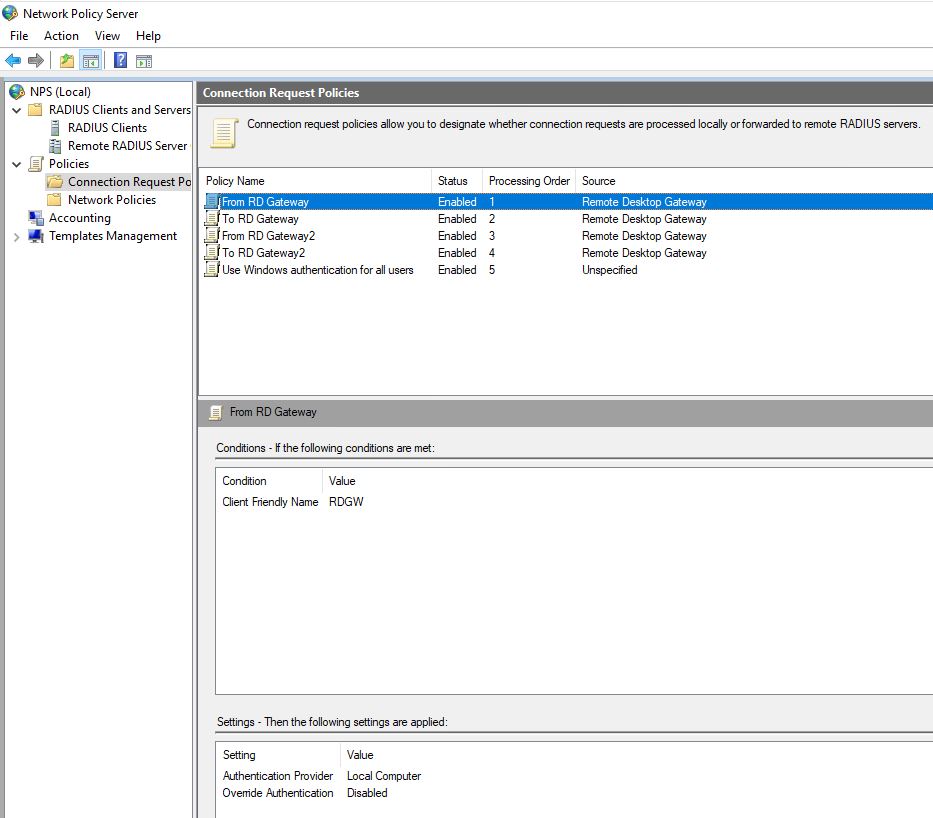
My issue is this, the two gateway servers are not a HA pair. They are separate Gateways, with will have different public SSL certificates, which have different RAP policies pointing to different farms / resources.
What I am having difficulty with is configuring the central NPS server so that if it receives requests from rdwebgw.domain.com it knows to send the Azure response back to rdwebgw.domain.com and if it receives request from rdwebgw2.domain.com it knows to send response back to rdwebgw2.domain.com.
I cannot seem to find any example of how the rules should look on the NPS server.
Perhaps I will need a central NPS server for each RD gateway, which is fine, just need to know whether I am wasting my time trying to get central NPS working with two completely separate RD Gateway servers.
Regards,
Scott.