Hi,
Any events logged on the source computer?
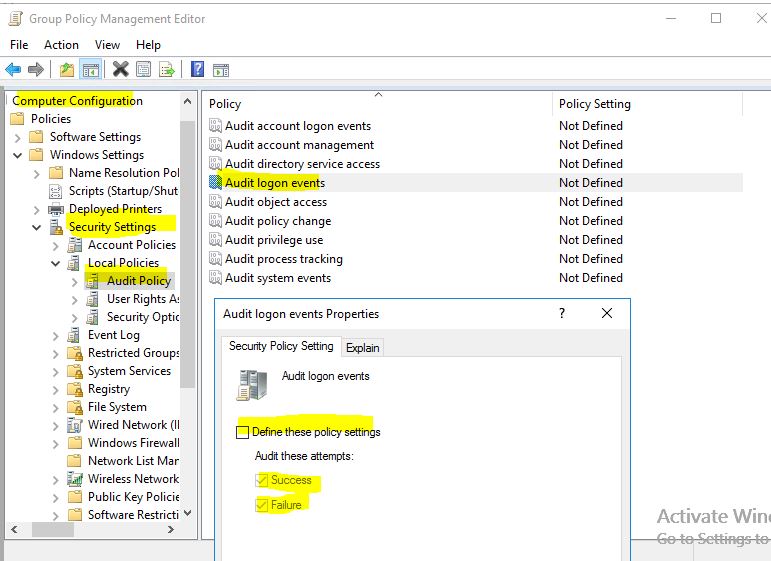
If not ,i would suggest you enable the audit policy on the source workstation as following:
If there are any progress, welcome to share here!
Best Regards,
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I've got many user's lockout my limit is 20 bad password As you can see in the picture the event 4776 is present many times in the same minute it can't be an user attempt. Netlogon log are registering the pid but it is not possible catch it in the destination computer , the process associated is gone after the bad password event. Moreover on the client machine there is not in security event the error replicated i've done the same conclusions of Mr. Joe Alves here https://social.technet.microsoft.com/Forums/en-US/64c744f7-265c-46d4-a59e-35bafc17e3fd/kerberos-preauth-lockouts?forum=winserversecurity But I don't understand what it means whe he says "To fix it I created a normal domain account and used that on both servers." there is a particular procedure to follow? my accounts are all created with Active Direcry User and Computer ... Thank you Luca ![79631-image.png][1] [1]: /api/attachments/79631-image.png?platform=QnA
Hi,
Any events logged on the source computer?
If not ,i would suggest you enable the audit policy on the source workstation as following:

If there are any progress, welcome to share here!
Best Regards,
With lockoutstatus I've noticed that the user count comes from 0 to 1 attempt browsing network folders but go to 11 when opening an empty word document
Can be KMS related?
Further investigations drives me to a network problem maybe related to ADFS
All my shared mapped drives are done with ADFS 6 (Windows 2019) when the monitored user try to open a network share the lockoutstatus count goes up sometimes with 2 other with 4 or 6 0xC000006A
The real weird thing is that in the netlogon log the pid mentioned
[LOGON] [3424] : SamLogon: Network logon of user from PC Entered
03/24 08:14:23 [LOGON] [3424] : SamLogon: Network logon of user from PC Returns 0xC000006A
will never appear in Procmon
i've started monitoring with this program the target machine but in 5 milion events the PID 3424 is missinig
so on with other PID'S ant other attempts
In NETLOGON log is shown the Thread not the PID
03/24 14:32:15 [LOGON] [9880] SamLogon: Network logon of user from PC Entered
03/24 14:32:15 [LOGON] [9880] SamLogon: Network logon of user from PCP Returns 0xC000006A
The PID is shown in the windows security events file of the pdc
<EventID>4776</EventID>
<Version>0</Version>
<Level>0</Level>
<Task>14336</Task>
<Opcode>0</Opcode>
<Keywords>0x8010000000000000</Keywords>
<TimeCreated SystemTime="2021-03-24T13:32:26.441369800Z" />
<EventRecordID>81355893</EventRecordID>
<Correlation />
<Execution ProcessID="652" ThreadID="9880" />
<Channel>Security</Channel>
<Computer>serverzacmi1.zacmi.lan</Computer>
so the process incriminated is lssas.exe but what is wrong?

Hello Luca,
Similar kind of problem we have faced recently with 5 active directory domain users. my lockout attempt limited to 5 times. And this becomes very frequent when this work-from-home situation started.
This might be due to multiple reasons I guess. Here is the step-by-step how I resolved it.
Domain controller > Event logs > Filter > 4740 (account lockout ) - (domain username)
Here you can get "Caller Computer Name"
:(The name of the computer account (e.g. Client34 ) from which the login attempt was generated)
Goto > Client34 System > Check if there are any network mapped drives and disconnect them.
The reason why we need to disconnect network mapped drives is when you first time saved the mapped drive you save the credentials so it won't ask the password even when you restarted the system. Consider you changed the domain user password and this mapped drive still tries to connect the network mapped drive with the same old password, after it attempted multiple times the account will be locked out.
2.Also check, you not logging into a temporary domain profile and make sure you logged into the system with an updated domain user password.
3.If you are using SSO, for domain and Outlook, Remove the saved credentials from the credentials manager and check.
Wishing you very good luck.
Regards,
Ram