I went 1 by 1 through the Security Options (Policies) that I changed to improve security and found that one of the policies I was told to change to "Deny All" which was "Network security: Restrict NTLM: Incoming NTLM traffic" I changed it to "Allow all" and updated the group policies and I can now connect through RDP.
Hopefully this won't be a risk to my DC.
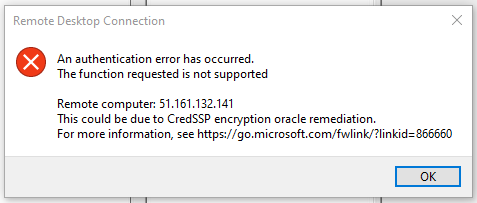
RDP - CredSSP Encryption Oracle Remediation error

After I installed the Hyper-V Role onto my server I've receiving this error when trying to login with RDP, I have already tried changing Encryption Oracle Remediation to Vulnerable, it didn't fix the issue and I reverted it after discovering the security risks of it.
The only things I did before this issue became apparent was removing IIS & Installing Hyper-V.
 ]1
]1
-
 Jessica 341 Reputation points
Jessica 341 Reputation points2021-03-28T01:49:19.983+00:00
2 additional answers
Sort by: Most helpful
-
GettnBetter 6 Reputation points
2021-03-28T03:13:50.747+00:00 This can be mitigated with a registry entry. I've found the primary reason for this is systems that are not up2date with Windows updates.
There are known workarounds: https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/credssp-encryption-oracle-remediation
-
Scrub404 1 Reputation point
2022-12-07T14:14:05.64+00:00 Since you are on Server 2019, I don't think the updates posted by GettnBetter will help
If you are on a domain, use the FQDN, IP or just the server name won't work , even if it resolves fine.
i.e. servername.domain.localI believe this is Kerberos related, Kerberos needs FQDN to connect.
NTLM has a few security risks associated with it, take caution.If your server is not on your domain, or you cant use Kerberos
Note: NTLM can be restricted in a domain via GPO preventing fallback option if Kerberos didn't work.
This will give you the CredSSP error.Try Enable-WSManCredSSP : https://learn.microsoft.com/en-us/powershell/module/microsoft.wsman.management/enable-wsmancredssp?view=powershell-7.3
The old registry and settings fixes for Server 2012 R2 & 2016 might still work in GettnBetter's post