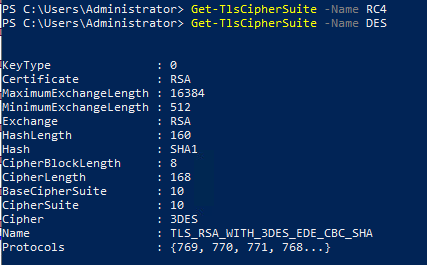
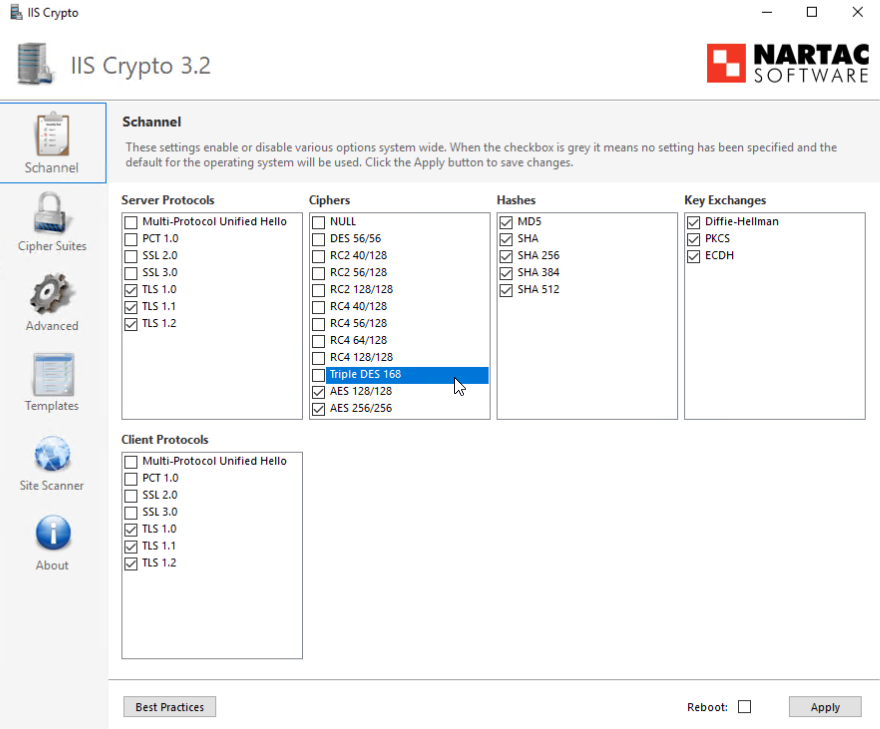
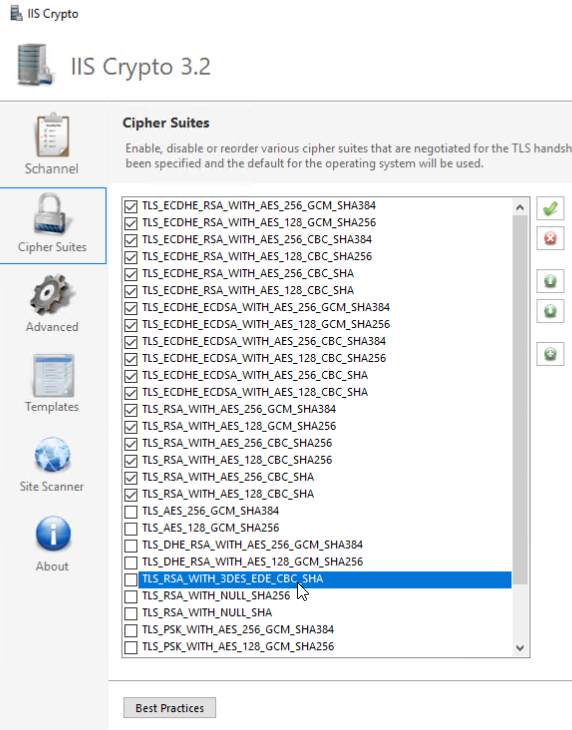
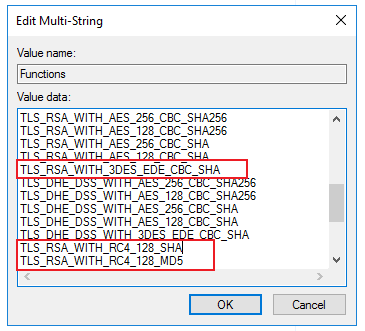
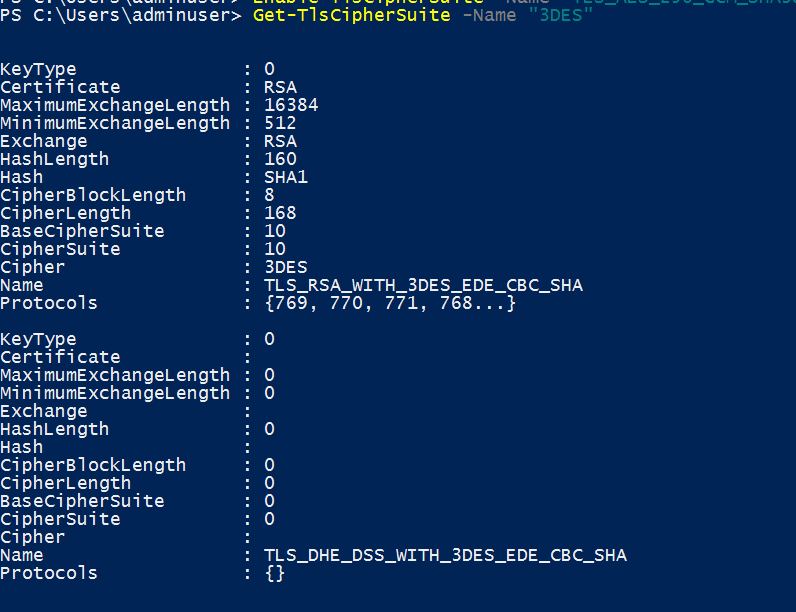
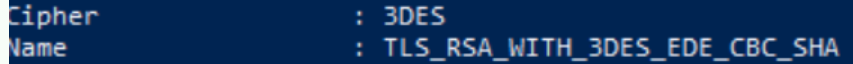
The recommended way of resolving the Sweet32 vulnerability (Weak key length) is to either disabled the cipher suites that contain the elements that are weak or compromised. You can disable I cipher suites you do you want by enabling either a local or GPO policy...
https://learn.microsoft.com/en-us/windows-server/security/tls/manage-tls
Since the cipher suites do have variation between the OS version, you can have a GPO for each OS version and a WMI filter on each GPO to target a specific OS version.
Microsoft does not recommend disabling ciphers, hashes, or protocols with registry settings as these could be reset/removed with an update.
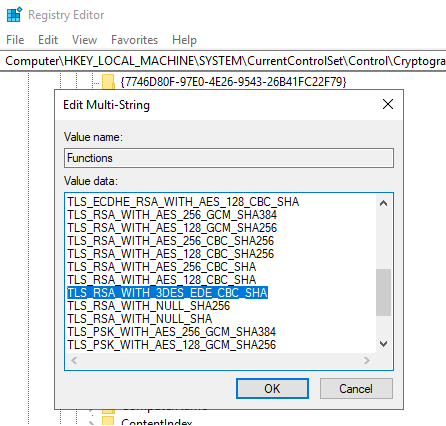
The preferred method is to choose a set of cipher suites and use either the local or group policy to enforce the list.
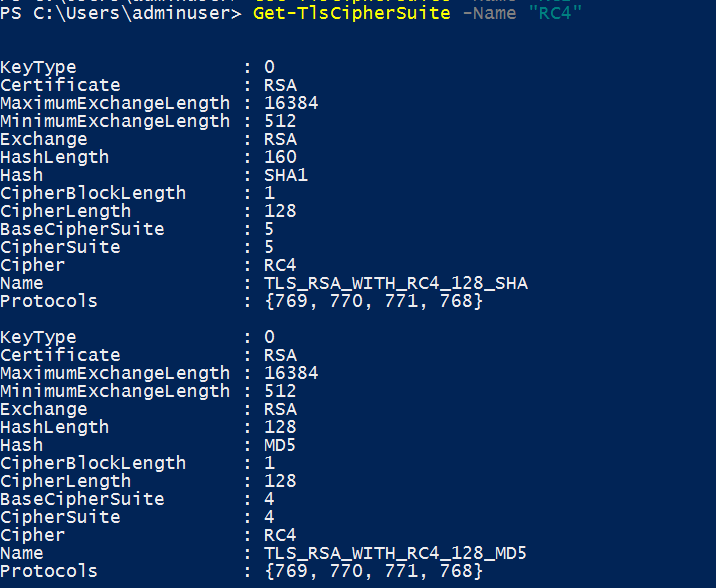
This allows you to select the cipher suites that support the TLS version you need and to select only cipher suites do not have weak or compromised elements like RC4, DES, MD5, EXPORT, NULL, and RC2.
Let look at an example of Windows Server 2019 and Windows 10, version 1809
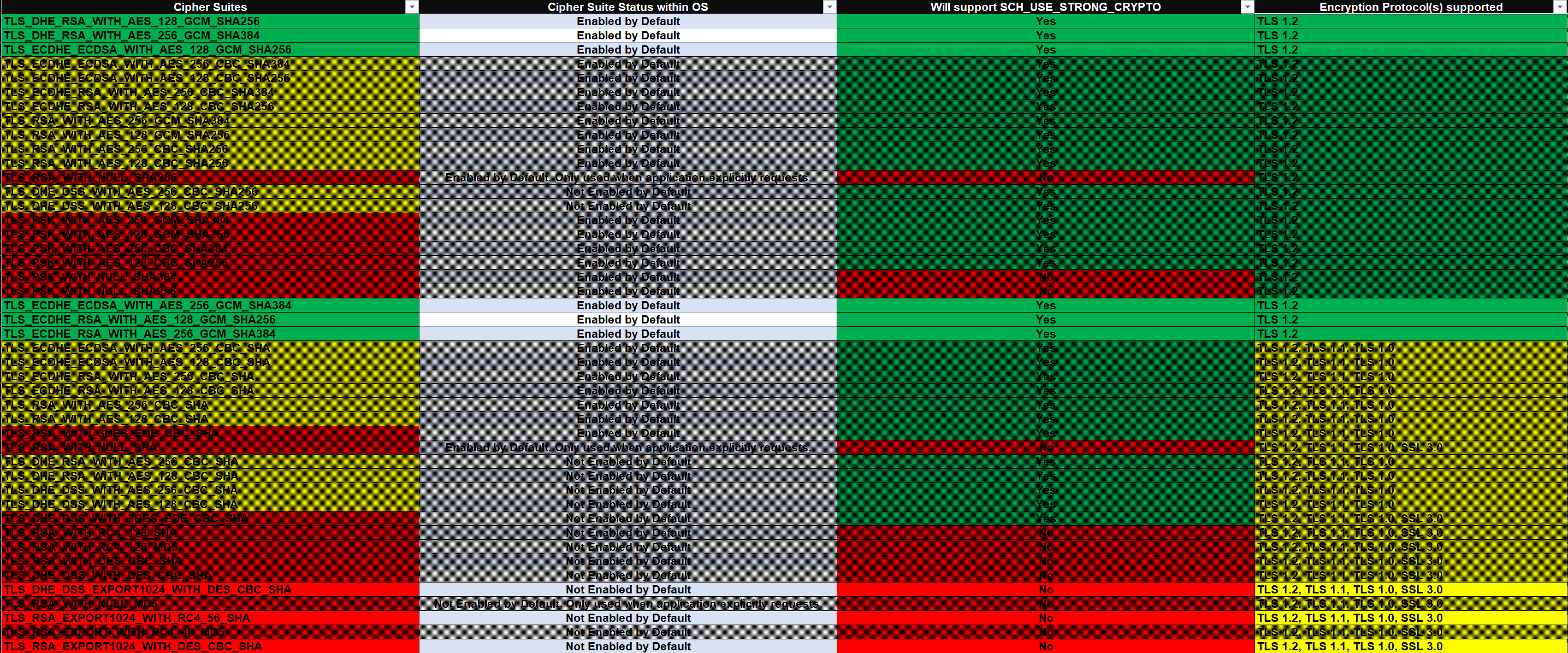
The cells in green are what we want and the cells in red are things we should avoid. Yellow cells represent aspects that overlap between good and fair (or bad)
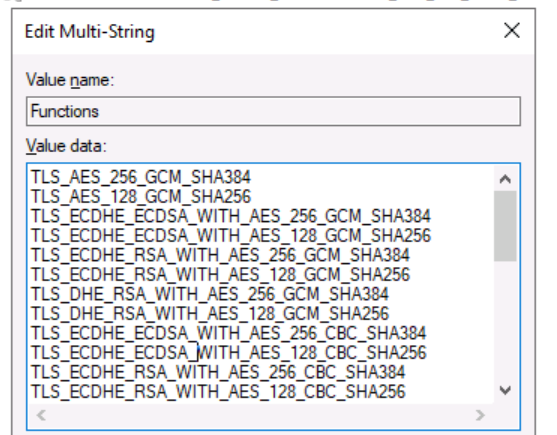
If we take only the cipher suites that support TLS 1.2, support SCH_USE_STRONG_CRYPTO and exclude the remaining cipher suites that have marginal to bad elements, we are left with a very short list.
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_DHE_RSA_WITH_AES_256_GCM_SHA384,TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
6 cipher suites that have strong elements, will support SCH_USE_STRONG_CRYPTO, and Perfect Forward Secret (PFS).
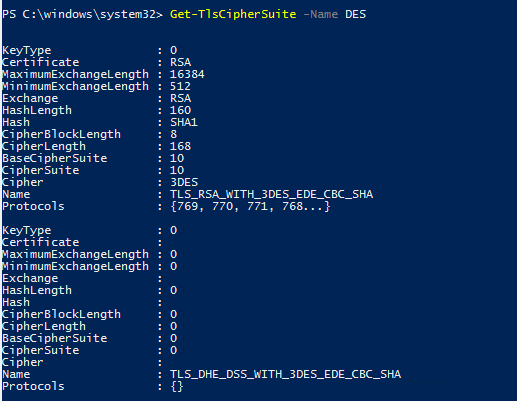
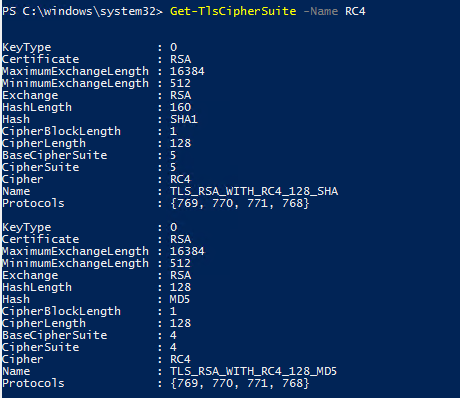
With this selection of cipher suites I do not have to disable TLS 1.0, TLS 1.1, DES, 3DES, RC4 etc. as there are no cipher suites that I am allowing that have those elements.

 ]
]