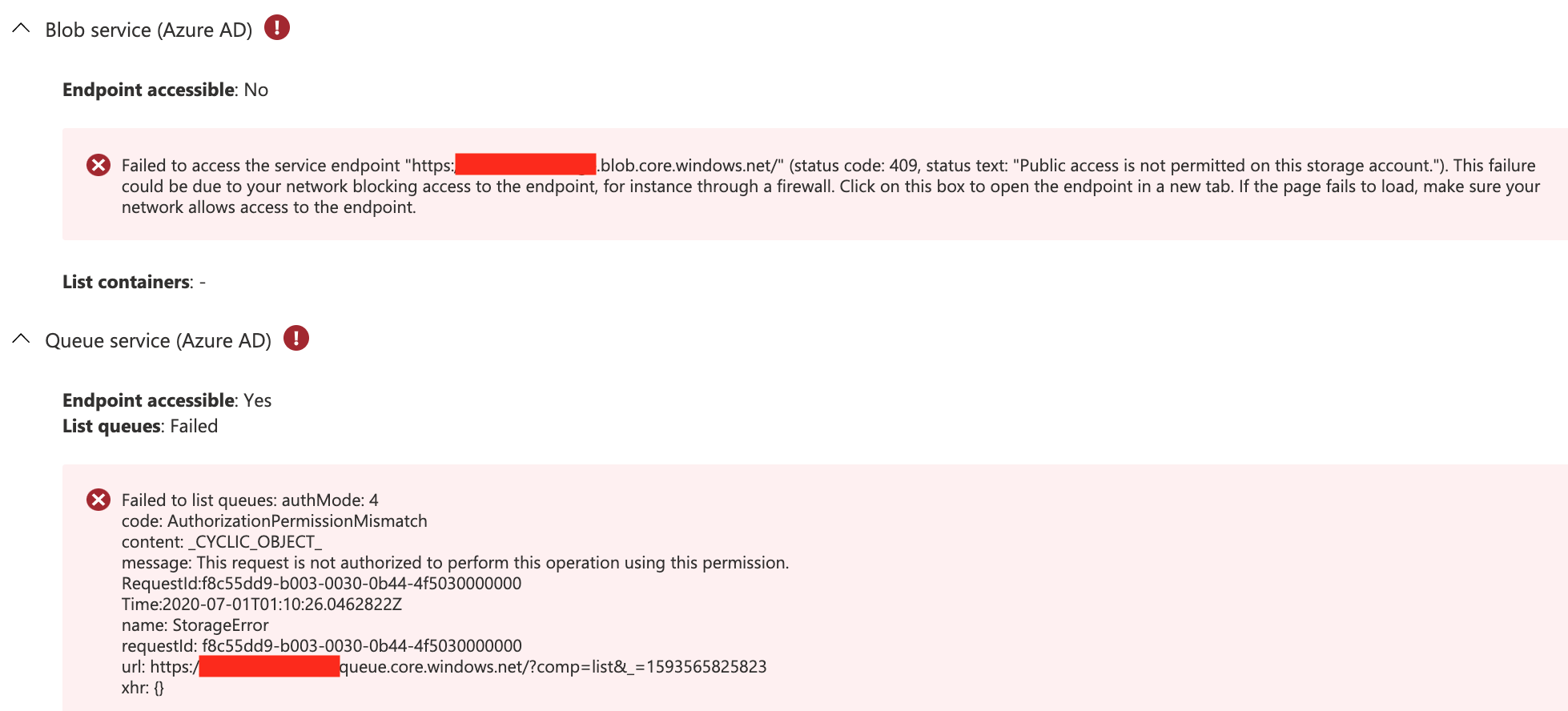
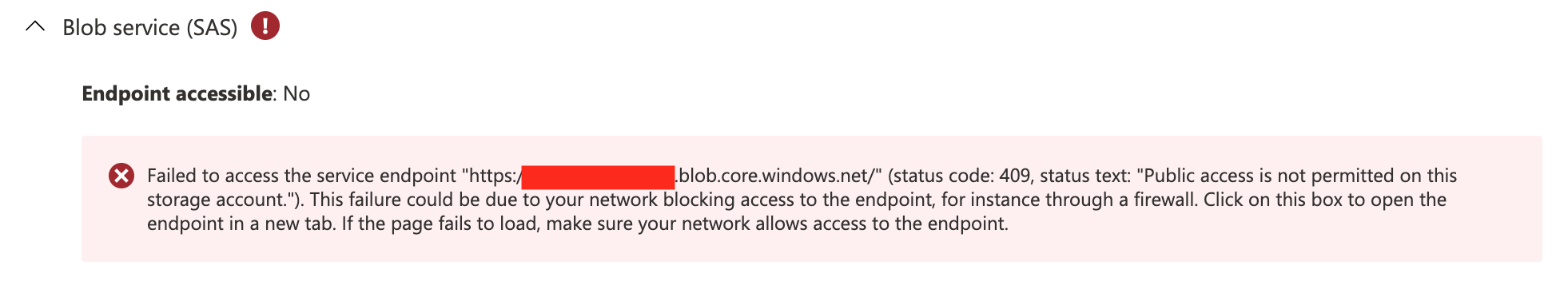
We created a new Storage Account on Azure. And, when we perform the Connectivity Check, it shows that Blob service (SAS) endpoint is not accessible with message "Public access is not permitted on this storage account." The status code is 409.
The Storage Account was upgraded from V1 to General-Purpose V2. Is that causing this issue?
Also, "Generate SAS and connection string" button in "Shared access signature" is disabled and greyed out.
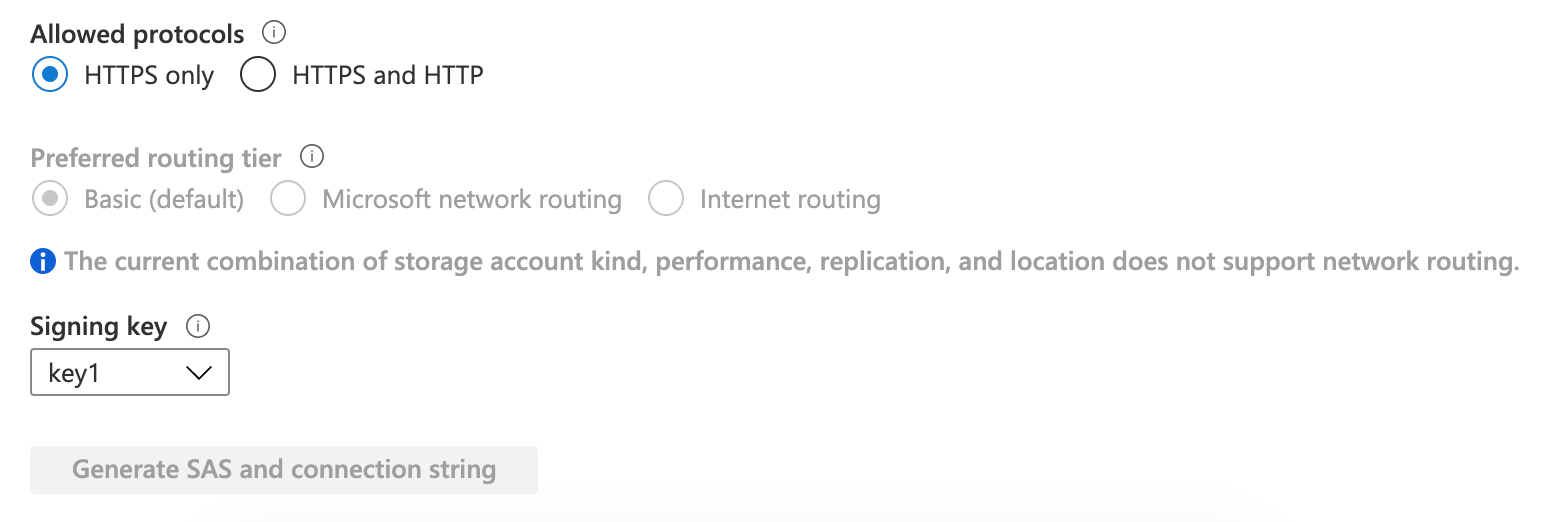
How do we create and enable this endpoint? My search so far doesn't point to any solution to create/enable this over the Portal. Is it possible only through the REST API?
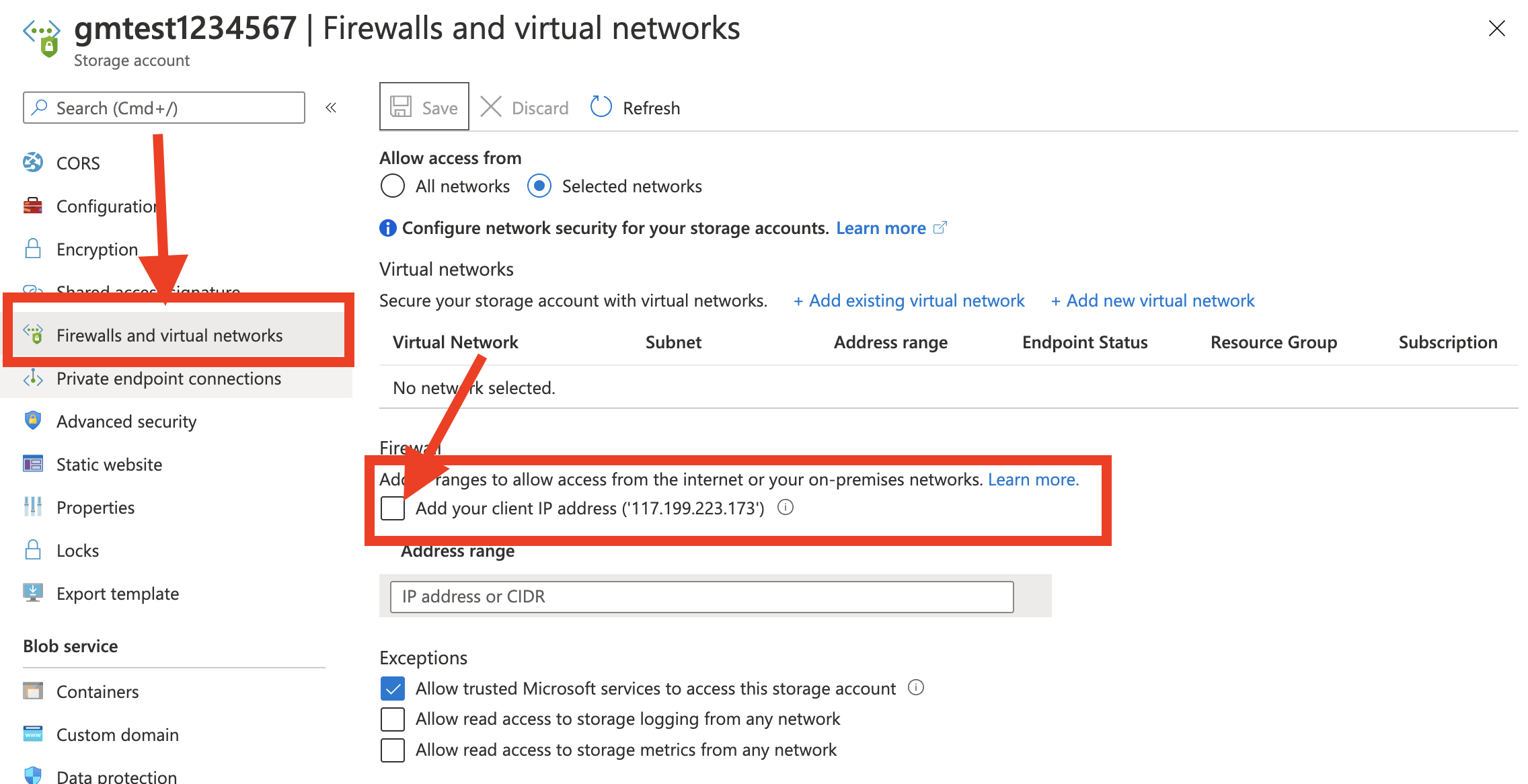
Blob service (SRP) check, Share Access Signature check is successful. There is no private endpoint, firewall created and access is allowed from "All Networks".
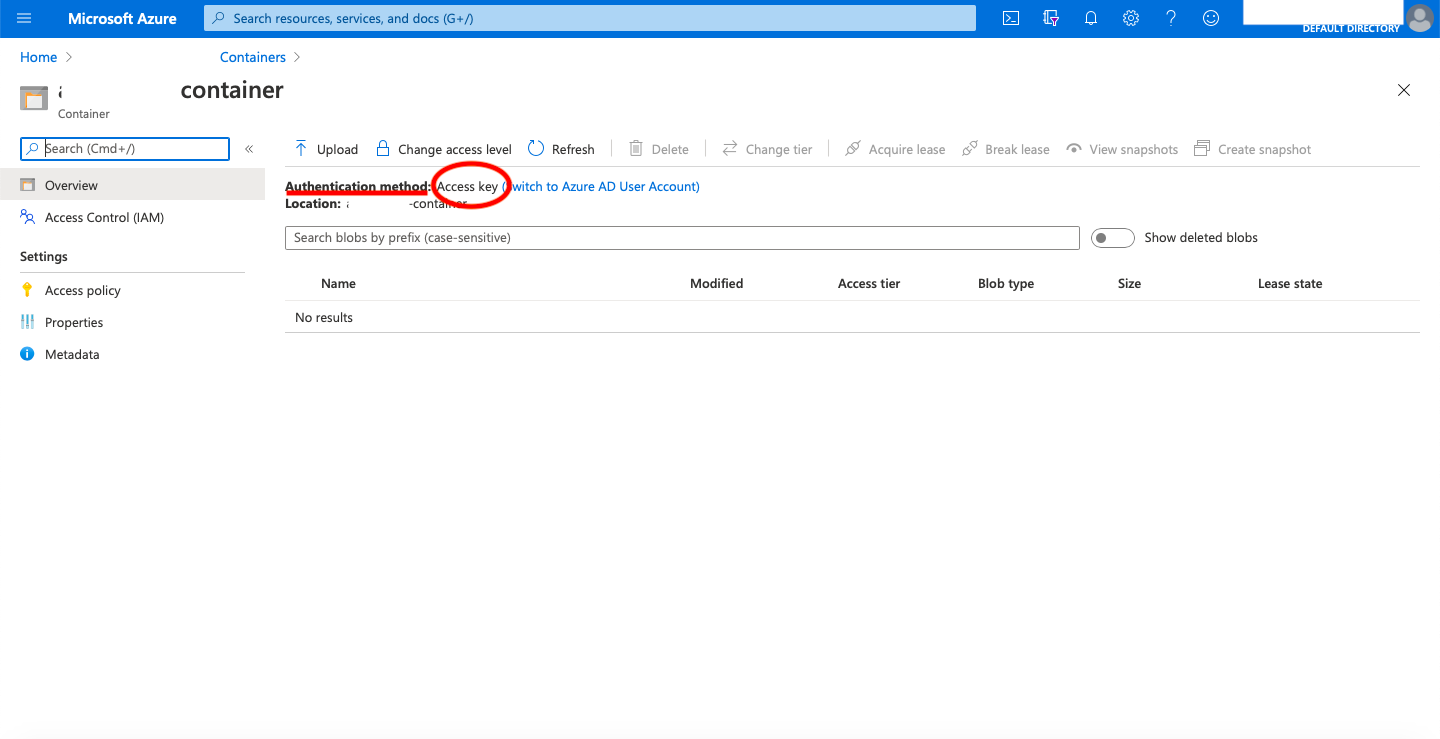
Accessing blob from client side with Storage Account Key with an API is currently failing with error code 403.
Also, we are successfully able to fetch the blob details from "Microsoft Azure Storage Explorer" connected with the 'Connection String' of the Storage Account.
Additional Details :
I can also see that "Blob service (Azure AD)" endpoint is not accessible, but "Queue service (Azure AD) endpoint is.