@thenewmessiah
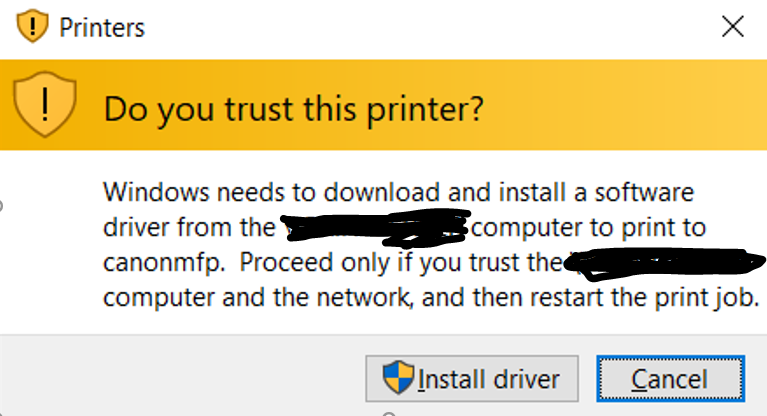
The new Windows default for Point an Print connections to shared printers is admin rights.
You can work through this with the registry setting on the client system.
The "RpcAuthnLevelPrivacyEnabled" set to 1 prevents the client systems, and the print server, from connecting to Linux machines pretending to be Windows print servers. Do you have Linux in your environment where you may have concerns?
To work through no administrative requirements for connections to Windows shared printers, then you can use a print driver on the server which is never downloaded to the client system. These drivers are known as Type 4 print drivers. You can find these on Windows update and from printer vendors. Type 4 print drivers have existed for nine years. More than 10 if you used Windows 8 in preview versions.
Since there is no software copied making the printer connection, then the attack service is gone.
There are group policies to specifically provide access to only print servers you control and if you manage all the Windows clients I also suggest closing down the remote spooler RPC endpoint on the client systems. Disable the Computer policy which Allow clients to connect to spooler . If the client is actually sharing a printer, the RPC endpoint is open but how many Windows clients are sharing a printer in your organization?
If you obtain your Type 4 drivers from Windows Update or if you are running 2012R2 you can use the drivers provided with the operating system. The client can get the driver from WU if a Type 4 driver is up there.
Admin rights for printer connection when software is downloaded from the server. It's the new world of Windows and it will not be changing.
Thanks