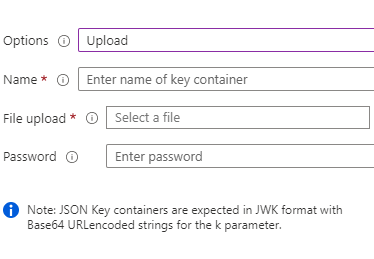
you need upload the private key with the password
policy keys => upload =>
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I am using B2C custom policies to federate to the external Azure AD Identity Provider. I was successful before when federating with client secrets, but trying to switch to certificates now, and getting an error "No url encoding for asymmetric keys". Here is what I did as a Proof Of Concept:
<CryptographicKeys>
<Key Id="client_secret" StorageReferenceId="B2C_1A_MyB2CPolicy" />
</CryptographicKeys>
{
"Key": "SendErrorTechnicalProfile",
"Value": "OpenIdConnectProtocolProvider"
},
{
"Key": "Exception",
"Value": {
"Kind": "Handled",
"HResult": "80131500",
"Message": "An invalid OAuth response was received: \"{0}\".",
"Data": {
"IsPolicySpecificError": false
},
"Exception": {
"Kind": "Handled",
"HResult": "80131515",
"Message": "No url encoding for asymmetric keys",
"Data": {}
}
}
}
What am I doing wrong?
Also, is there any documentation on how to do it?
you need upload the private key with the password
policy keys => upload =>
