How to update managed identity for connect AKS to ACR
p.shapurau
16
Reputation points
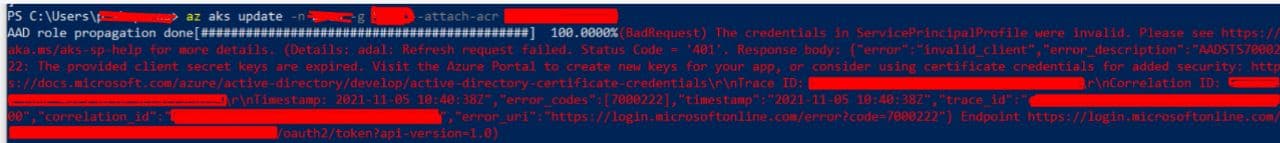
I have a long ago created cluster connected to the Azure container register. A year later, the managed identity for the cluster expired and my cluster does not see containers to the Azure container register. Please tell me step by step and specifically what should I do, how to update the managed identity?
I have seen many links and articles on this topic on the Internet, but nothing specific. I think the solution should be clear and simple. this question will often come up in people after a year.