Hi @Leonard, Jared ,
Thanks for reaching out.
I understand that you are trying to get access token to call protected API from your web application.
First we need to understand that Microsoft identity platform supports different authentication flows for different kinds of application scenarios.
Client Credential flow is commonly used for server-to-server interaction when your application can acquire a token to call a web API on behalf of itself.
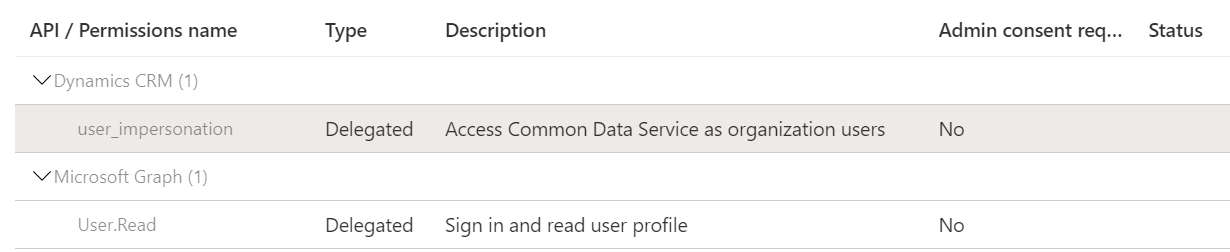
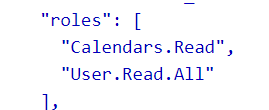
Client credentials flow exposes only application permissions to APIs which are granted directly to the application itself by an administrator.
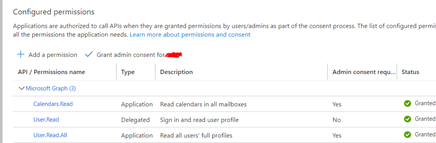
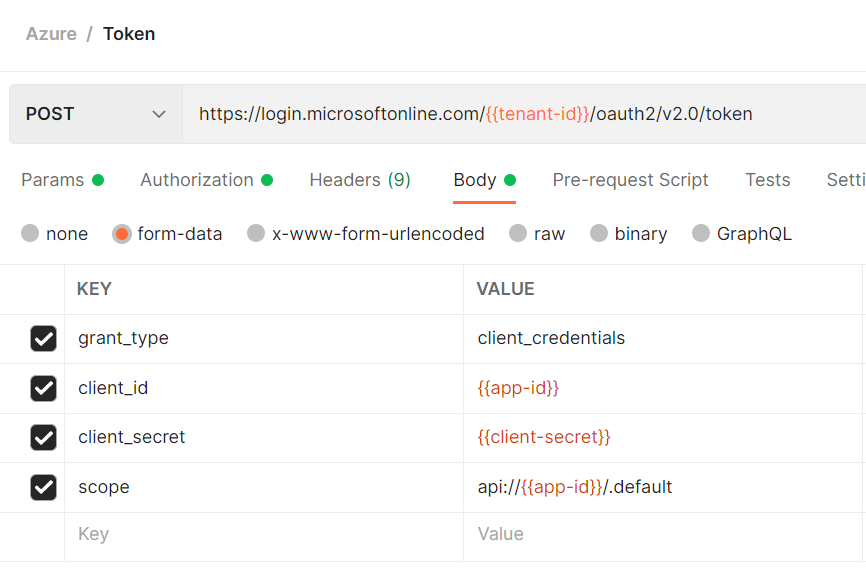
The scope for client credential would be https://graph.microsoft.com/.default. Based on this application identifies all the permissions which has been granted.
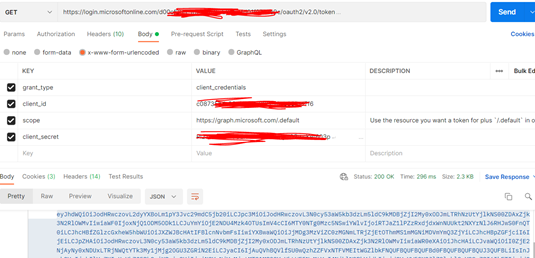
You can decode the access token you received using jwt.ms and validate the permissions in the access token to access the exposed API’s resources.
However, Here as you are using delegated permissions to call Dynamics CRM API which need to expose by web application as signed in user. I would recommend using Authorization code flow. This flow enables apps to securely acquire an access token that can be used to access resources secured by the Microsoft identity platform.
First request an authorize code begins with the client directing the user to the /authorize endpoint
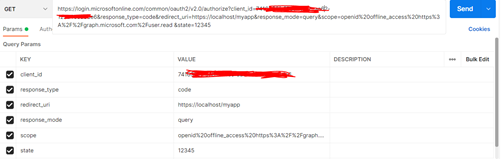
After signing in, your browser should be redirected to https://localhost/myapp/ with a code in the address bar.
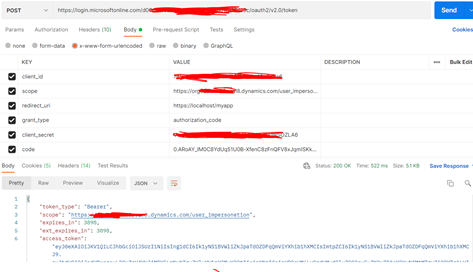
Now that you've acquired an authorization_code and have been granted permission by the user, you can request for an access_token to the resource by sending a POST request to the /token endpoint with the scope https://[my domain].crm.dynamics.com/
The access token identifies the intended recipient of the token by audience defined in the token.
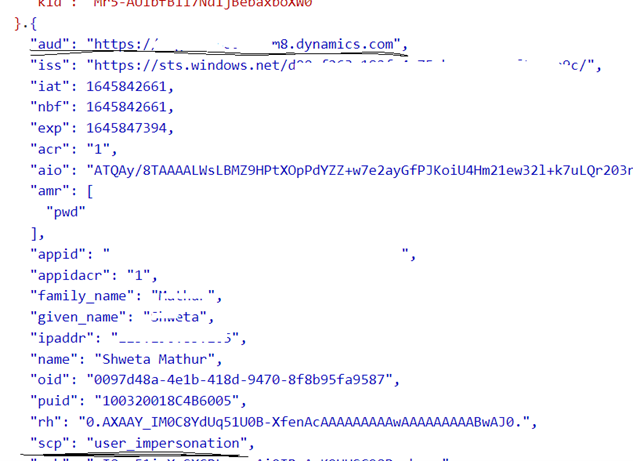
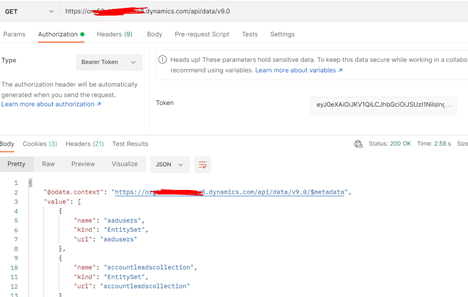
You can use the access token in requests to Dynamics 365/Dataverse API by including it in the Authorization header as bearer token.
Hope this will help.
Thanks,
Shweta
Please remember to "Accept Answer" if answer helped you.