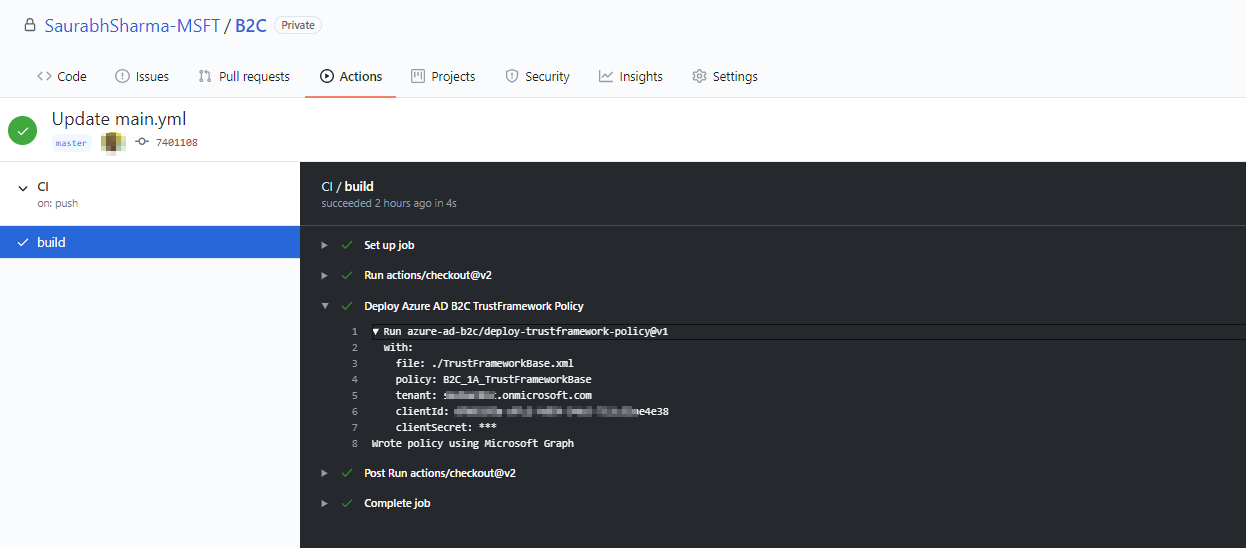
@Aspirant3434342-8925 I am able to deploy Azure AD B2C Trustframework policy using existing action template - https://github.com/marketplace/actions/deploy-azure-ad-b2c-trustframework-policy without any error. Here are the steps I have followed -
- I have created a GitHub repository and imported the existing template by going to "Set up a workflow yourself" from Actions tab on GitHub
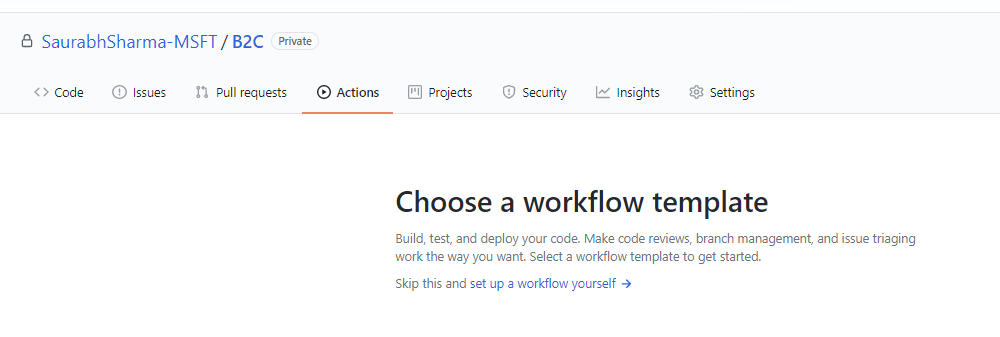
- Search Marketplace for action template you want to include (Deploy Azure AD B2C TrustFramework Policy)
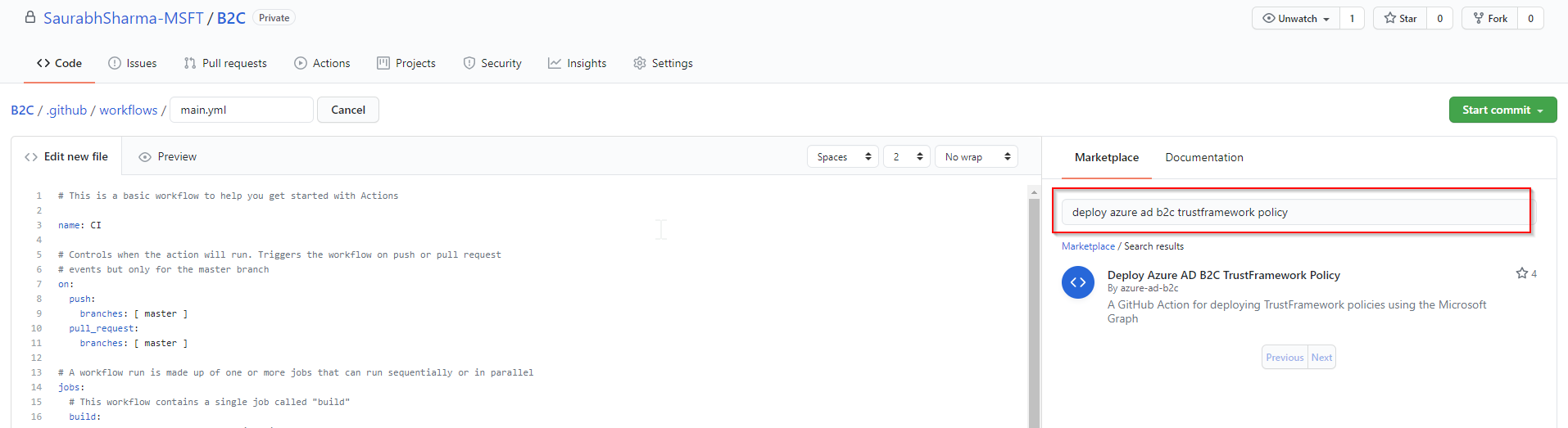
- Copy the snippet into your .yml file by clicking copy button.
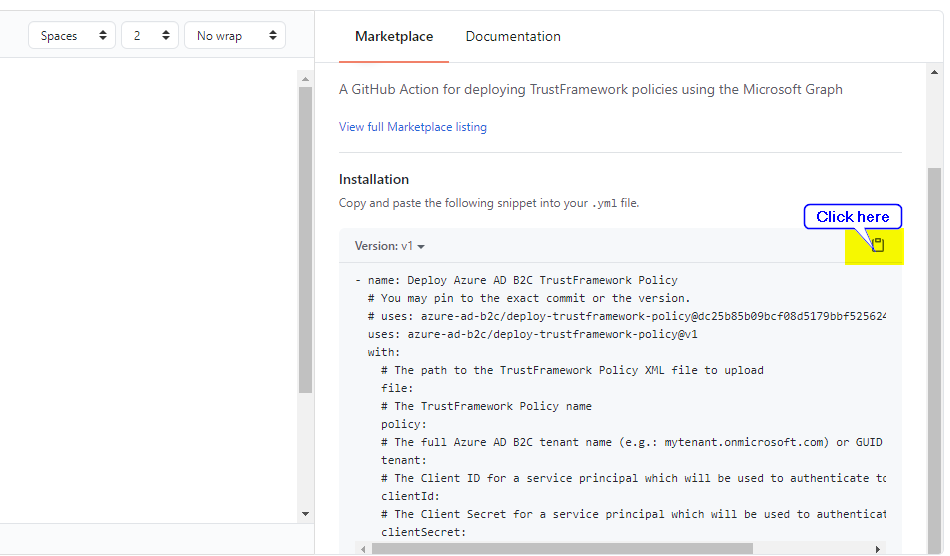
- Configure the environment variables in .yml file and add other details like file path, policy name.
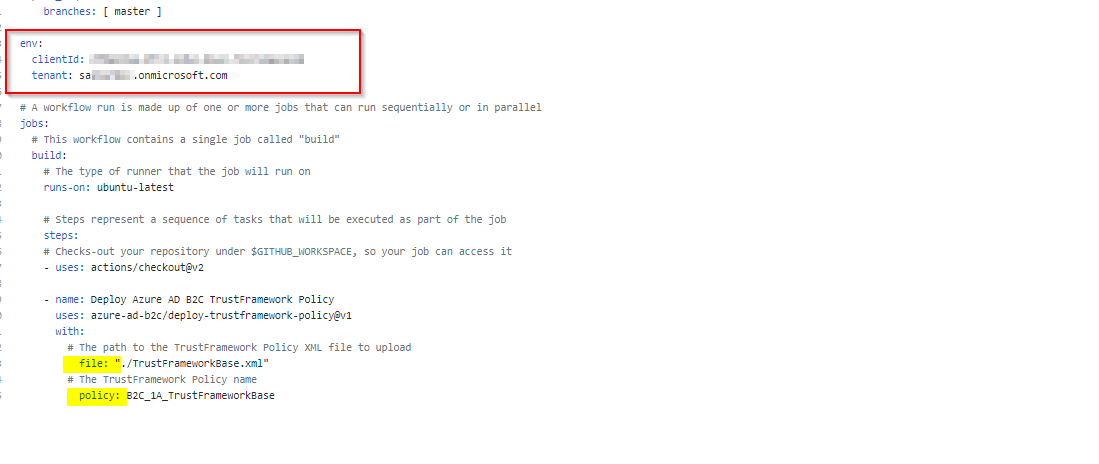
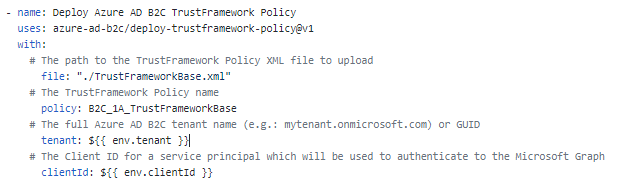
- For Tenant Name and client Id refer the variables using
${<!-- -->{ env.tenant }}and${<!-- -->{ env.clientId }}
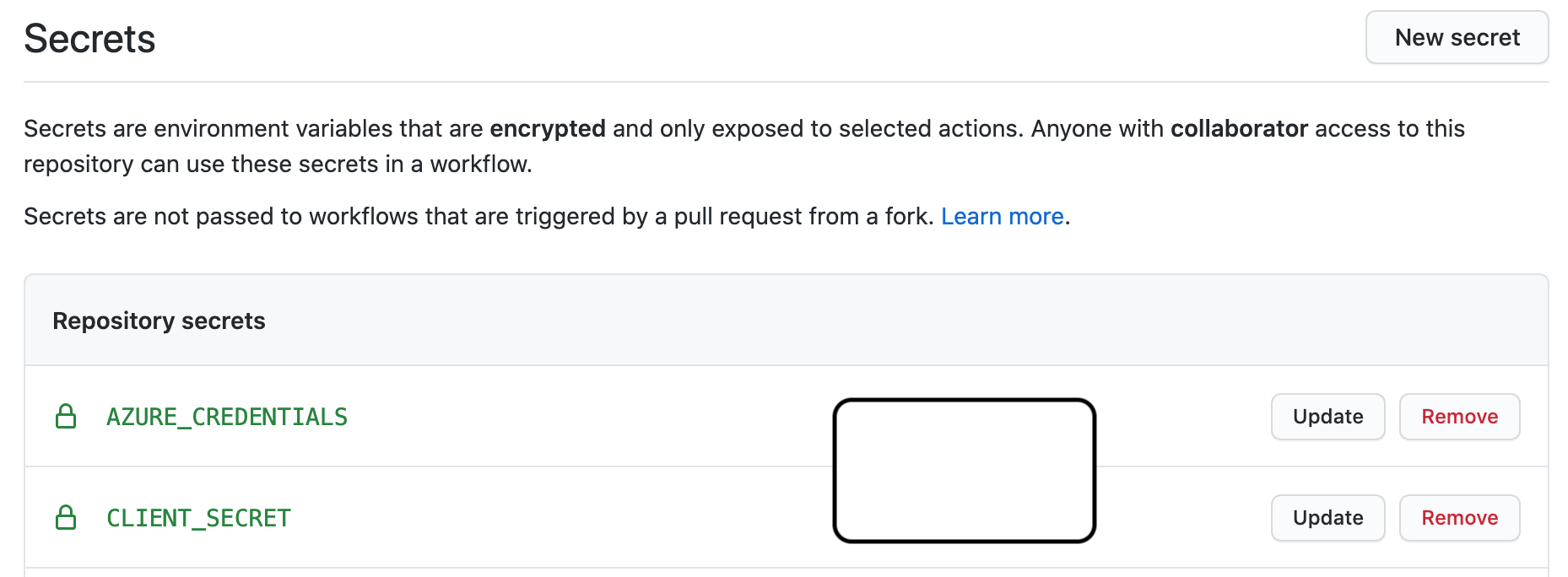
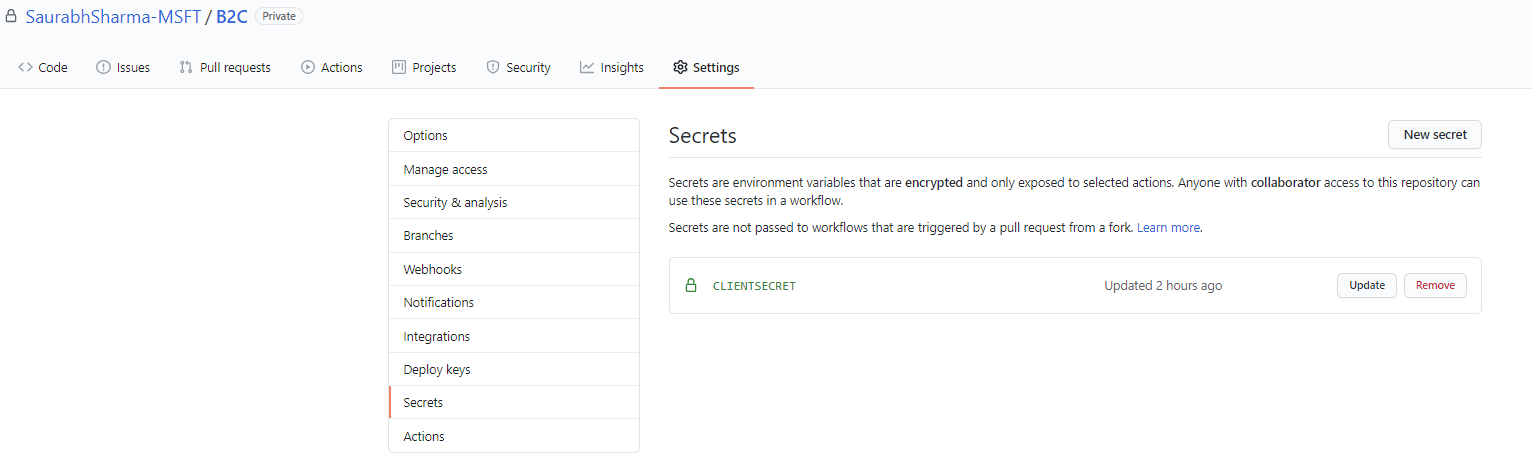
- Now for Client secret you need to setup "Secrets" in your repository settings to define a secret name and assign Client Secret value of the registered application.
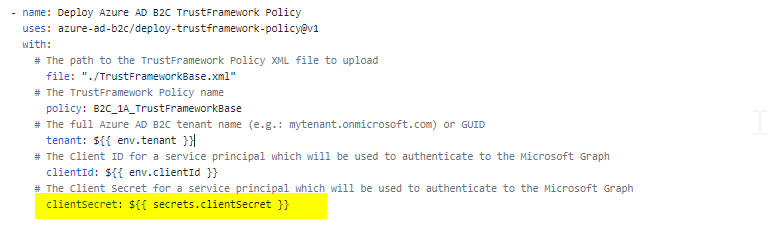
- You can refer to the stored secret in .yml file by using ${<!-- -->{ secrets.clientSecret }}
- Once you save the file you can check the Actions tab for build status.
- Once you save the file you can check the Actions tab for build status.