I am trying to get a c# console application running, that is synchronizing the global termstore from an xml on a regular basis. This is gonna be supposed a timerjob, that will run in the windows schedueler.
The target ist a SharePoint 2016 environment.
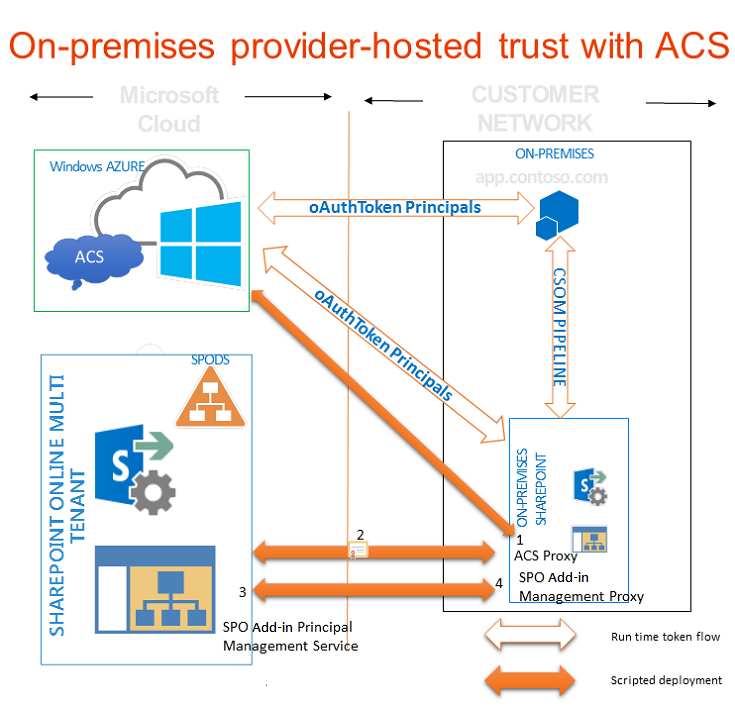
Since we dont wanna use a service account for that purpose, we want to use the app-only mode based on this https://learn.microsoft.com/en-us/sharepoint/dev/solution-guidance/security-apponly-azureacs
If I understood the tutorial correctly, the same approach should also work for an on-premise environment?
SharePoint App-Only is the older, but still very relevant, model of setting up app-principals. This model works for both SharePoint Online and SharePoint 2013/2016/2019 on-premises and is ideal to prepare your applications for migration from SharePoint on-premises to SharePoint Online.
I could successfully get this whole console application running against our sharepoint online dev-tenant using the following code.
But now when I try to get this running in the SharePoint 2016 environment, it keeps failing.
I did the exact same thing as I did for the SharePoint Online. I created an app (via appnewreg.aspx), granted the same permissions (via appinv.aspx) and exchanged the siteUrl, clientId and clientSecret accordingly.
string siteUrl = "MySiteUrl";
string clientId = "ClientId";
string clientSecret = "ClientSecret";
using (var clientContext = new AuthenticationManager().GetACSAppOnlyContext(siteUrl, clientId, clientSecret))
{
var web = clientContext.Web;
clientContext.Load(web, w => w.Title);
clientContext.ExecuteQuery();
Console.WriteLine(web.Title);
};
Yet I cant get the console application running.
Receiving the following error:
The remote server returned an error: (400) Bad Request. - {"error":"invalid_request","error_description":"AADSTS90002: Tenant '8a450d28-f099-4c54-bcb9-ddced3a8c499' not found. Check to make sure you have the correct tenant ID and are signing into the correct cloud. Check with your subscription administrator, this may happen if there are no active subscriptions for the tenant.\
So my question is, how can I authenticate within a C# console application with the app-only model? Or is that not possible for SharePoint 2016?
From my understanding, I dont need a provider hosted app for my usecase neither do I need high trust or low trust? Is that correct?