Claims are a concept in tokens used in auth flows - SAML, OIDC, etc - not in SCIM, which is a standard for provisioning rather than authentication or authorization.
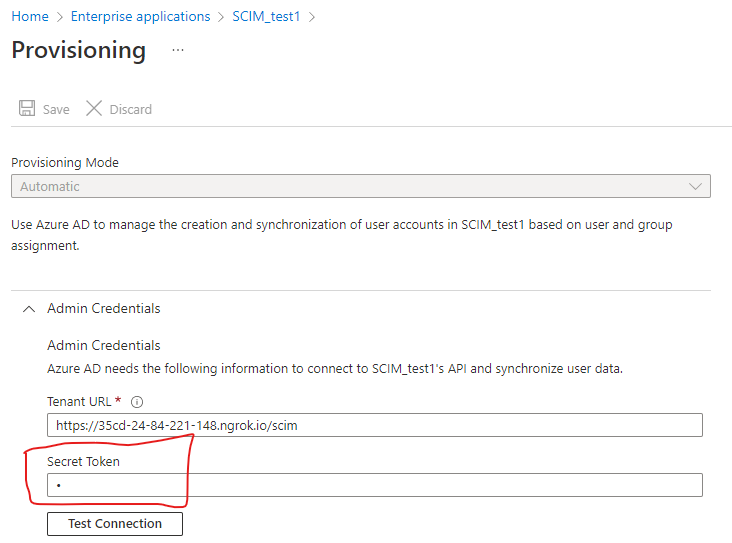
Our service only allows you to map a flow for attribute values from the source Azure AD object itself - such as a user or group - and not about other objects in the directory, such as the directory itself (i.e.: a directory ID, or the application ID/service principal ID of the application being used for provisioning). The inclusion of the Azure AD tenant ID in a header of the request is not required by the SCIM standard and I believe is not documented either - meaning it could be subject to change in the future, and should not have production dependencies built on it.
In order to distinguish what instance of the app is being provisioned to, you should build your web app to allow this to be determined either by a value in the SCIM URL (i.e.: https://example.xyz/UniqueValue/scim/v2/) or a value in the bearer token generated by your web app for usage by the SCIM provisioning config in Azure AD.