TLS on Azure App Services
I wrote this article some time ago “How to disable TLS 1.0 on an Azure App Service Web App” that explains some of the reasons TLS was not configurable on the Azure App Service platform. There were many customers who wanted to disable TLS 1.0 so they could remain or become PCI compliant and at the time of writing that article, it was only possible to disable TLS 1.0 on the ASE platform.
Here is a good post about this on the Azure App Service forums “TLS plans for Azure App Service ”
Before I begin, I get the opportunity to interview many people and one of the *trick-ish questions I ask is “What is the difference between SSL and TLS?”, do you know the answer? The answer is at the end of the article.
Well, you can be certain that, I would expect this as a customer of Microsoft that they provide us with the capability for being PCI compliant and they are/have. If you were or are the administrator of an Azure App Service you would have received an email with contents similar to the following.
- You will be (**are) able to require minimal TLS version (1.1 or 1.2) for your App Service. Configurable via the Azure portal or ARM templates.
- After, see dates here, all newly created App Services will require TLS 1.2. However, you will be able to lower the required TLS version (it’s configurable) to support older browsers, but you ought to consider the security implications of that.
If you have questions about that your can log them on the App Service forum or on StackOverflow.
Outgoing requests
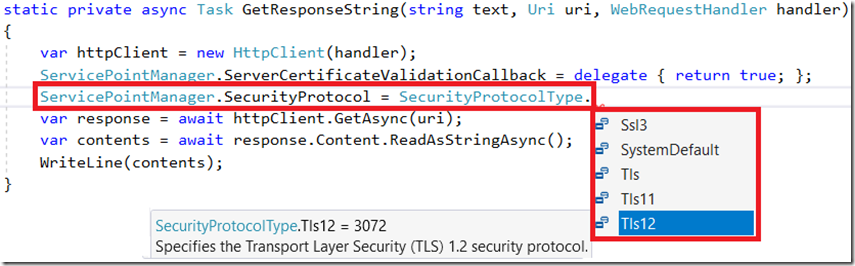
It is a common scenario that applications hosted on the Azure App Service platform call other services (Web APIs) hosted in different locations using HTTPS. I.e. site / API not hosted on Azure App Services. I am unaware of any restrictions which will stop outgoing communications that use SSL or TLS because this can be coded into your application. I.e. when you are instantiating/configuring the System.Net.Http.HttpClient, I can choose the SecurityProtocol to use when I make the outgoing connection, as seen in Figure 1.
Figure 1, how to configure SSL / TLS protocol from code
- Until it is no longer able to set SSL3, TLS, TLS11 from the .NET code I would expect the platform to support those outgoing protocols. Interesting and I wonder how many people actually set that and how difficult it would be to change.
- This is the most important point, if the web site or web API that your application calls into (from your App Service) start requiring TLS 1.2 and you have coded it to use some other or not enforced the protocol type, then this is something you and the owner of the API you call need to work out.
You can also set the outgoing SSL Protocol using System.Security.Authentication.SslProrocols enum, check it out here.
***My recommendation is to move away from anything less than TLS 1.2 faster than ASAP.
Nice to know
Although customers who have chosen to deploy their application on the Azure App Service platform do not need to worry so much about what is happening behind the scenes. It is still often interesting for some to know. If you choose the Windows stack for your App Service then requests to your web site are responded to from IIS. Here are some nice articles that discuss how TLS is configured on a Windows server.
- Managing SSL/TLS Protocols and Cipher Suites
- How to restrict the use of certain cryptographic algorithms and protocols in Schannel.dll
*What is a SSL certificate, What is a TLS certificate? Answer: SSL stands for Secure Socket Layer and was developed by Netscape in 1994, TLS stands for Transport Layer Security and is simply an updated, more secure version of SSL. I like this article. If the candidate could then discuss the differences between encryption and hashing, that would be very impressive.
**I used ‘are’ because the use of ‘will be’ vs. ‘are’ have different timeframe meanings. As I write this article, the ability to configure this is not available, but I know the ability is coming before the PCI compliance deadline.