Enterprise PKI with Windows Server 2012 R2 Active Directory Certificate Services (Part 1 of 2)
My co-worker – Yung Chou – brings us Part 1 of a 2 Part blog post on using PKI in an enterprise networking environment.
Here is an excerpt of his article -
PKI is heavily employed in cloud computing for encrypting data and securing transactions. While Windows Server 2012 R2 is developed as a building block for cloud solutions, there is an increasing demand for IT professionals to acquire proficiency on implementing PKI with Windows Server 2012 R2. This two-part blog post series is to help those who, like me, perhaps do not work on Active Directory Certificate Services (AD CS) everyday while every so often do need to implement a simple PKI for assessing or piloting solutions better understand and become familiar with the process. I believe the most effective way to learn AD CS is to walk through the process, build a test lab, practice and learn from mistakes. You can download Windows Server 2012 R2 VMs from https://aka.ms/R2 and build a simple AD environment with Hyper-V like the following to test out these steps.
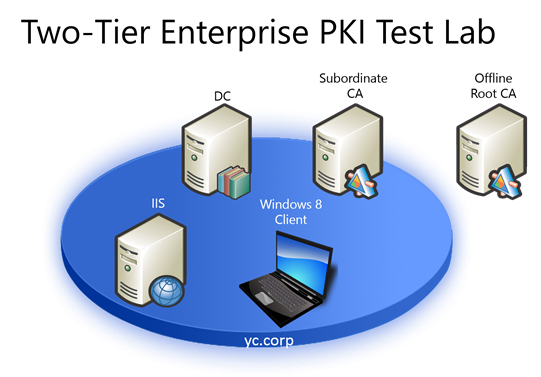
The following six steps form the core process of implementing PKI. The common practices are to first build a root CA with a standalone server, followed by configuring a subordinate CA on a member server for issuing certificates, while securing the root CA by taking it offline and bringing it back online only when issuing a subordinate CA certificate. Notice Part 1 include the first four steps, while the rest are in Part 2. All descriptions and screen captures are based on Windows Server 2012 R2.
Logical Steps
- Build a standalone root CA
- Create an enterprise subordinate CA
- Deploy certificate templates
- Enable certificate auto-enrollment
- Set certificate revocation policies
- Configure and verify private key archive and recovery
Yung continues on to describe in detail how to implement PKI for the Enterprise in his full article which can be found here -
Enterprise PKI with Windows Server 2012 R2 Active Directory Certificate Services (Part 1 of 2)
Cheers!