Integrating *NIX client in Active Directory using LDAP Part - I
In Windows 2003 R2 the active directory schema is RFC 2307 compliant particularly to hold the UNIX related attributes. This feature can be used to populate related attributes for objects like users, groups etc. An UNIX client like Solaris or Red Hat Linux 4 now take the full advantage of these attributes when configured to bind and talk to Active Directory using LDAP. Users can be authenticated against the Active Directory from these *NIX boxes. We will discuss the step-by-step (both Windows and *NIX environment) procedures to achieve this.
On a windows 2003 R2 we need a group, a user and populate the attributes. Once the group and users are created, the values for the attributes can be added any tool that allows us to interact directly with the schema like adsiedit. A simple vb script can also perform the same.
List of attributes for a group:
gidNumber – an unique number for the group in a domain
List of attributes for a user:
uid – generally the sAMAccountName
uidNumber – an unique number for the user in a domain
gidNumber – number same as of the gidNumber of the group to which this user belongs
msSFU30Name - generally the sAMAccountName
unixHomeDirectory – home directory for UNIX environment
loginShell – default shell for user
I am including a sample script to populate these attributes using a vb script here. To run it properly we need to put the correct domain name. Populating the group information can also be done by modifying this script.
A popular approach is to install “Identity Management for UNIX” and the use the UNIX attribute tab in the properties page of users and group to populate these attributes. But, this method forces us to add a value to “msSFU30NisDomain” attribute which is not all used in this whole scenario. If keeping this extra amount of data in the schema does not ring any bell, we can use this straight forward method.
on error resume next
Const ADS_SCOPE_SUBTREE = 2
Const ADS_PROPERTY_CLEAR = 1
Const ADS_PROPERTY_UPDATE = 2
dim samname,uidnumber
samname= InputBox("Enter SAMAccountName :")
Set objConnection = CreateObject("ADODB.Connection")
Set objCommand = CreateObject("ADODB.Command")
objConnection.Provider = "ADsDSOObject"
objConnection.Open "Active Directory Provider"
Set objCOmmand.ActiveConnection = objConnection
objCommand.CommandText = "Select distinguishedname from 'LDAP://DC=<xxx>,DC=<xxx>' " & "where objectCategory='person' and objectclass='user' and samaccountname='" & samname & "'"
objCommand.Properties("Page Size") = 1000
objCommand.Properties("Timeout") = 30
objCommand.Properties("Searchscope") = ADS_SCOPE_SUBTREE
objCommand.Properties("Cache Results") = False
Set objRecordSet = objCommand.Execute
objRecordSet.MoveFirst
Do Until objRecordSet.EOF
strUserDN = objRecordSet.Fields("distinguishedname").Value
set objuser = GetObject("LDAP://" & strUserDN & "")
uid = ""
objuser.GetInfoEx Array("uid", "sn"), 0
For Each value in objuser.GetEx("uid")
uid = uid & "" & value & ";"
Next
uid = Mid(uid,1,len(uid)-1)
uid = InputBox("Please Enter the value for the Uid value","",uid)
pos=InStr(uid,";")
if pos <> 0 and not isempty(uid) then
uidarray = Split(uid,";")
dim strarr()
dim i
For i = lbound(uidarray) to ubound(uidarray)
redim preserve strarr(i)
strarr(i) = uidarray(i)
Next
if (ubound(uidarray)>=0) then
objuser.PutEx ADS_PROPERTY_CLEAR,"uid", 0
objuser.SetInfo
objuser.GetInfoEx Array("uid"), 0
objuser.PutEx ADS_PROPERTY_UPDATE, "uid", strarr
objuser.SetInfo
end if
else
objuser.Put "uid", uid
objuser.SetInfo
end if
uidNumber = ""
uidNumber = objuser.Get("uidNumber")
uidNumber = InputBox("Please Enter the value for the uidNumber value","",uidNumber)
objUser.Put "uidNumber", uidNumber
objuser.setinfo
gidNumber = ""
gidNumber = objuser.Get("gidNumber")
gidNumber = InputBox("Please Enter the value for the gidNumber value","",gidNumber)
objUser.Put "gidNumber", gidNumber
objuser.setinfo
unixHomeDirectory = ""
unixHomeDirectory = objuser.Get("unixHomeDirectory")
unixHomeDirectory = InputBox("Please Enter the value for the unixHomeDirectory value","",unixHomeDirectory)
objUser.Put "unixHomeDirectory", unixHomeDirectory
objuser.setinfo
loginShell = ""
loginShell = objuser.Get("loginShell")
loginShell = InputBox("Please Enter the value for the loginShell value","",loginShell)
objUser.Put "loginShell", loginShell
objuser.setinfo
msSFU30Name = ""
msSFU30Name = objuser.Get("msSFU30Name")
msSFU30Name = InputBox("Please Enter the value for the msSFU30Name value","",msSFU30Name)
objUser.Put "msSFU30Name", msSFU30Name
objuser.setinfo
objuser.setinfo
set objuser = nothing
objRecordSet.MoveNext
Loop
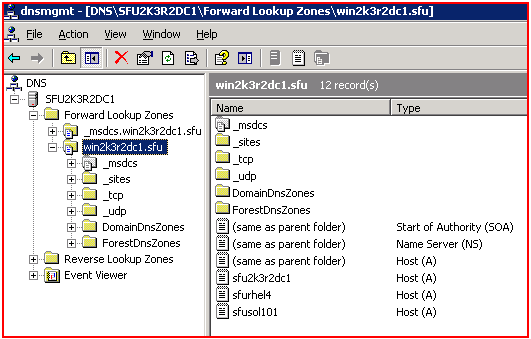
The next step is to add DNS record for the *NIX clients.
On the Microsoft Windows system, create a forward (A) and reverse (PTR) DNS record for the *NIX client. In addition, create a reverse (PTR) DNS record for the AD server. These records are required for Kerberos to function properly. The forward (A) DNS record for the Active Directory server is created automatically when configuring the Active Directory server.
We also need to Synchronizing the Clocks and Configuring Time Zones.
Time synchronization is essential for Kerberos to function properly. By default, only a 300-second clock skew is acceptable. Ensure that time zones on all Microsoft Windows and Solaris servers are configured properly. NTP can be used synchronize time.
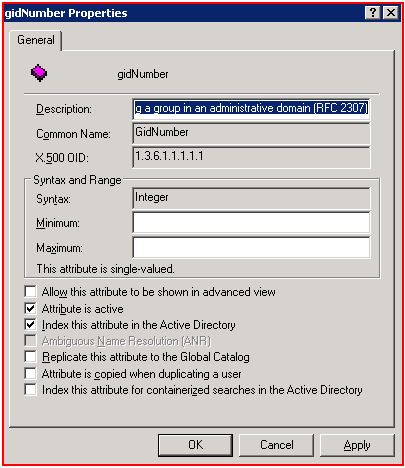
Indexing an attribute helps queries find objects that have that attribute more quickly and efficiently than if the attribute had no index. The Active Directory directory service index is built automatically by a background thread on the directory server.
On the Microsoft Windows system, index the following *NIX client attributes: uid, uidNumber and gidNumber. In Active Directory, indexes can be added by using the Schema Management Snap-In for the Microsoft Management Console. Btw, this snap-in must be registered first.
This almost completes the steps that need to be performed on the Windows side, except one; we will mention that in appropriate time.
In our next discussions we will see how a *NIX client can be joined in active directory.