Certification Authority Enhanced RPC security
Hello
It’s Rafal Sosnowski from Microsoft Dubai Security PFE Team. Today I want to talk about CA Enhanced RPC security causing failing certificate requests on Windows XP. Of course Windows XP has been end of life since April 8th, 2014 however we can still find this OS in the field.
When trying to issue certificate on Windows XP from Windows Server 2012 (or 2012 R2) CA we got an error "The certificate request failed. The permissions on this certification authority do not allow the current user to enroll for certificates. "
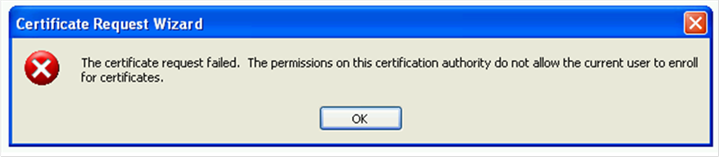
At first glance it has to be Permissions issue but when we verify them on CA and on the template level they are ok. If we go to the "Failed Request" container on CA we cannot see any request which has been denied by the CA. This is because the request is never delivered to the server.
Windows uses WCEE (Windows Client Certificate Enrollment) protocol to request and retrieve certificates from the Certification Authority (CA). This protocol is encapsulated into DCOM and sends information from XP/2003 in the clear text by default.
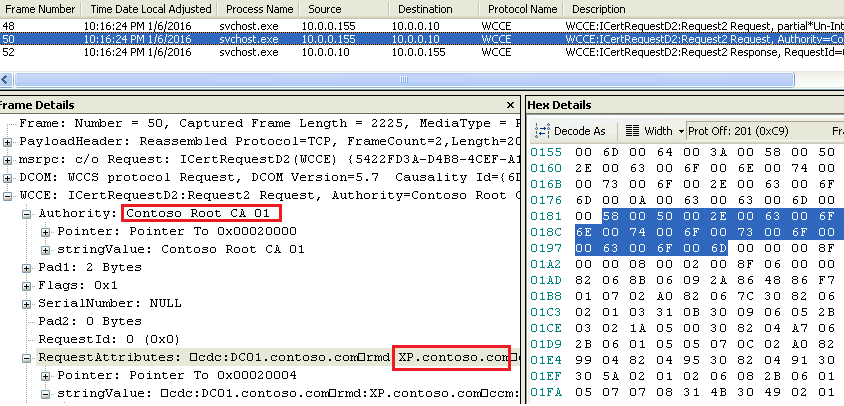
Let’s see the Network Trace first from Windows XP (certificate request):
And then response form the CA (certificate response):
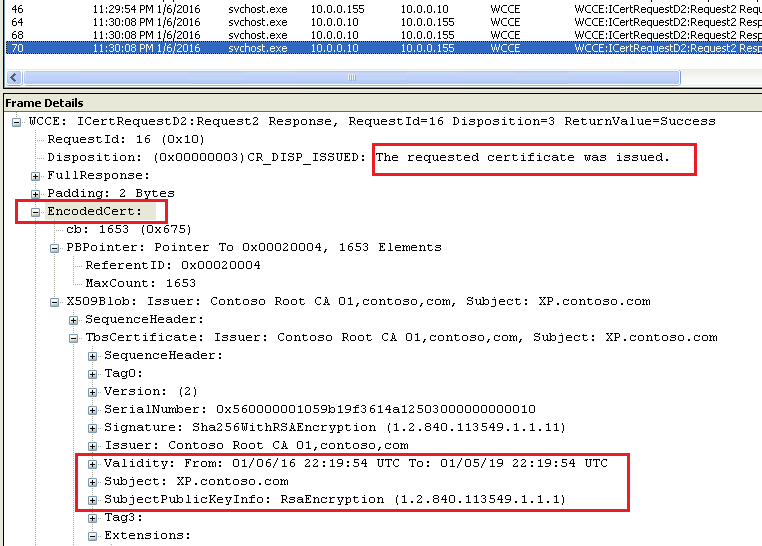
For both certificate request and certificate response we can see subject names, public key information, algorithms used, validity time of the certificate etc. Its fine as certificate request and certificate itself are considered public information and usually don’t convey any confidential data.
However, for very secured networks and concerned customers this kind of information can be considered sensitive as certificate can also contain e-mail address, user UPN, Service Principal Names, hostnames etc.
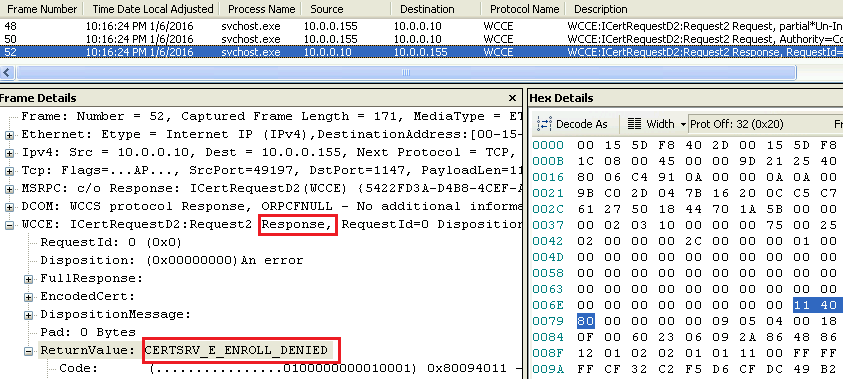
This is why Microsoft enabled by default “Enhanced RPC security” for certificate requests on CA running Windows Server 2012 R1 and 2012 R2. This feature is not supported by Windows XP/2003 acting as certificate requestor. The error received while trying to enroll for a cert on Windows XP, as mentioned at the beginning of this post, is “The certificate request failed. The permissions on this certification authority do not allow the current user to enroll for certificates. ". I know it is little misleading but this is how the response is interpreted by Windows XP.
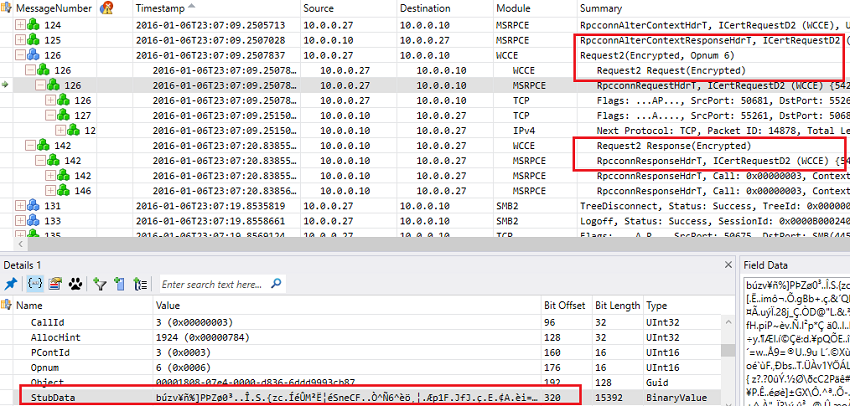
We can clearly see this in the network trace:
Enhanced RPC security for certificate request is enabled by default on CA running Windows Server 2012 and 2012 R2. It can be enabled on Certification Authority running previous Operating Systems by using command:
certutil -setreg CA\InterfaceFlags +IF_ENFORCEENCRYPTICERTREQUEST
When this feature is enabled both Certificate request and certificate response from CA are encrypted:
Short version:

So how to let Windows XP enroll certificates from Windows 2012/2012R2 CA?
- Upgrade Windows clients to higher OS as XP is not supported anymore
- Disable Enhanced RPC security for certificate requests by removing the flag on the CA and restart the service:
certutil -setreg CAInterfaceFlags -IF_ENFORCEENCRYPTICERTREQUEST
According to my tests even if you lower the RPC security on the Windows 2012 CA - Windows 10 will still negotiate higher security level and encrypt the request.