How to run the IT Environment Health Scanner in an EBS Environment
[Today’s post comes to us courtesy of Mark Stanfill]
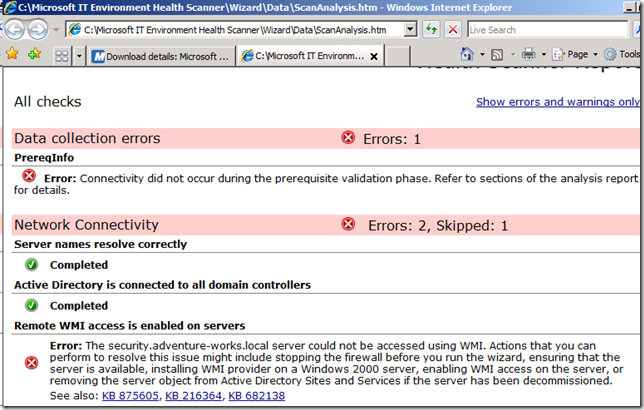
By default, TMG disallows WMI traffic as part of its security hardening. However, the Microsoft IT Environment Health Scanner (direct download) requires WMI to collect data for its analysis. To work around this limitation, you must temporarily create an exception to allow the Health Scanner to successfully complete. On a default run, you will see an error like the one below:
To prevent this error, you must explicitly configure TMG to allow WMI traffic from the computer where you are running the IT Environment Health Scanner. The steps below show us running the Health Scanner from the Messaging Server for demonstration purposes, but the same principles apply to running the tool from any server or workstation.
- Create an Access Rule in TMG
- Log on to the Management Server as an administrator and load the Forefront TMG Management console.
- Highlight the first rule in the Firewall Policy list. This will ensure that the new access rule is placed before any other rules that might interfere.
- Right-click Firewall Policy and select New and Access Rule…
- Follow the prompts in the New Access Rule Wizard, using the following settings (choose the defaults if not specified):
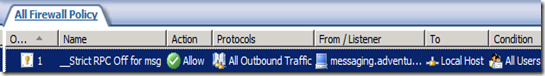
- Right-click on the newly created rule and choose Configure RPC Protocol from the drop-down list.
- Deselect Enforce strict RPC compliance
- Click OK to save and exit
- Edit the TMG System Policy
- Right-click on Firewall Policy in the Forefront TMG Management console and choose Edit System Policy…
- Select Authentication Services from the list on the right and then select Active Directory.
- Deselect Enforce strict RPC compliance
- Select OK to save the changes
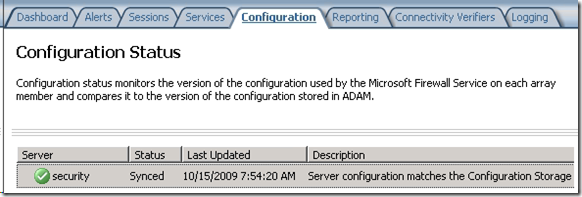
- Click Apply to save the changes to TMG. Wait until the configuration status under Monitoring shows that the changes have taken effect.
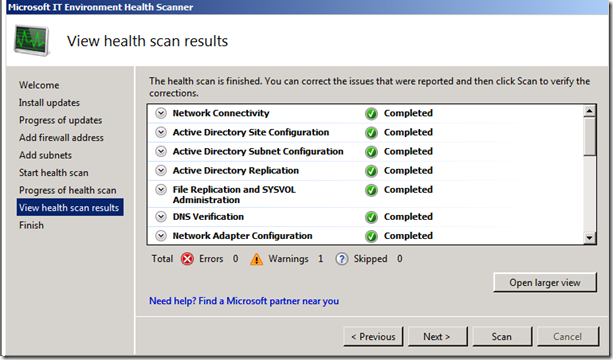
- Run IT Environment Health Scanner – Return to the server or workstation where you installed the Health Scanner and re-run the tool.
- Revert the Changes
- Return to the Management Server and disable or delete the access rule created in step 1 above.
- Re-enable strict RPC compliance on the Authentication Services\Active Directory system policy.
- Apply the changes.