Secure communication and work management with Microsoft Kaizala
Co-authored by Nitu Narula

In today’s mobile-centric world, instant messaging apps and chat platforms have disrupted business communication. However, when workers communicate with teammates over public mobile messaging platforms, businesses have no control over security protocols. They cannot control dissemination of sensitive data in chat groups, control group access on an individual level or verify the identity of group members. Storing data in local servers to comply with local data protection regulations and erasing data on employees’ private devices is also not possible on these platforms.
In essence, while these platforms have made it easier for teams to communicate, they also present a number of security challenges:
- Maintaining data ownership
- Managing and getting visibility on users
- Preventing data leakage when an employee leaves an organization
- Data residency compliance
Although mainstream chat platforms and traditional enterprise security solutions might be able to address cyber attacks and malware, they are unable to meet deeper business security and local compliance requirements. When we created Kaizala for real-time business communication and coordination, our focus was on securing data in the increasingly mobile-centric business landscape. To enable communication in a secure manner, crucial data required to be protected not just from external attacks, but also from internal points of failure, device-level security gaps and risks of human error.
Our team at Microsoft thus took a broader view of enterprise data security and ingrained comprehensive security and compliance features that protect business interactions on Kaizala at a deeper level. Here’s how Kaizala was built to be secure by design:
Compliance framework
Kaizala is built on Office 365 trust and secure principles. The Office 365 compliance framework details the protocols that need to be followed while handling user and customer data. Kaizala is placed in Category A for high compliance with the framework, which means it has a strong commitment to privacy, doesn’t mine customer data for advertising purposes and doesn’t offer voluntary disclosure of private data to law enforcement agencies.
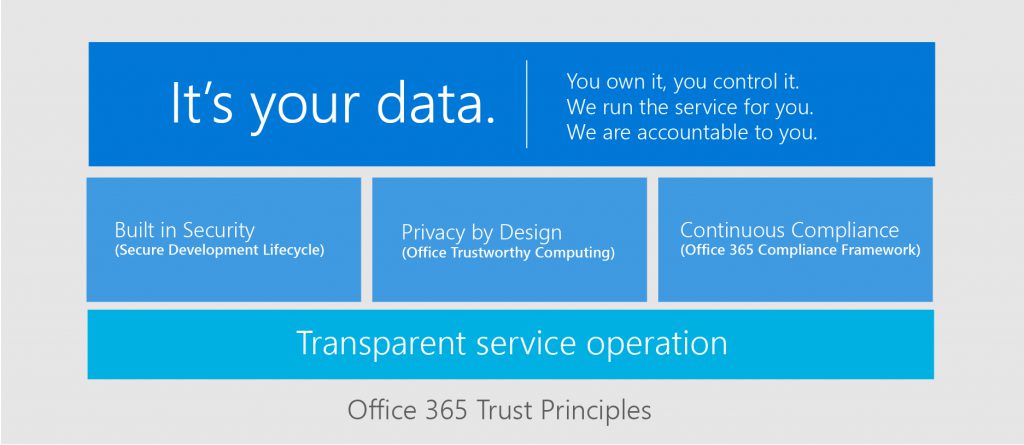
A range of compliance features augment Kaizala’s data protection:
- Data is stored locally in Azure data centers to meet local data regulatory requirements. Data in messages, attachments and contacts details from Indian phone numbers, for example, is stored locally in Microsoft Azure data centers located in India. This feature is exclusive to Indian phone numbers.
- Organization groups on Kaizala have access to a consolidated Tenant User List (TUL) that includes all users who are members of the tenant’s organization groups. Admins can request specific data for each user on a group, easily identifying them and instantly revoking access for any unauthorized users.
- When access is revoked and a user is removed from an organization’s group, Kaizala automatically erases all the group’s data from the client device. This is a unique feature that helps secure company data when a former employee or unauthorized user is removed from an organization group.
These unique features help Kaizala go beyond the standard compliance requirements and provide augmented data protection to businesses, employees, and customers.
Security features
Kaizala resides on the Office 365 & Microsoft Azure cloud platforms, which are industry leaders in cloud security. Our team’s experience of working with large corporations as well as small enterprises has enabled us to create a highly sophisticated cloud platform that handles data responsibly.
Security and privacy features are woven into every step of the design process. Security development lifecycle (SDL) helps our engineers and designers address and resolve security concerns from the initial planning stages to the eventual launch of a product. We have created detailed diagrams for data flow and threat models to help identify security concerns while designing Kaizala.
Multiple layers of security make the service platform secure at every level, from data to physical security.
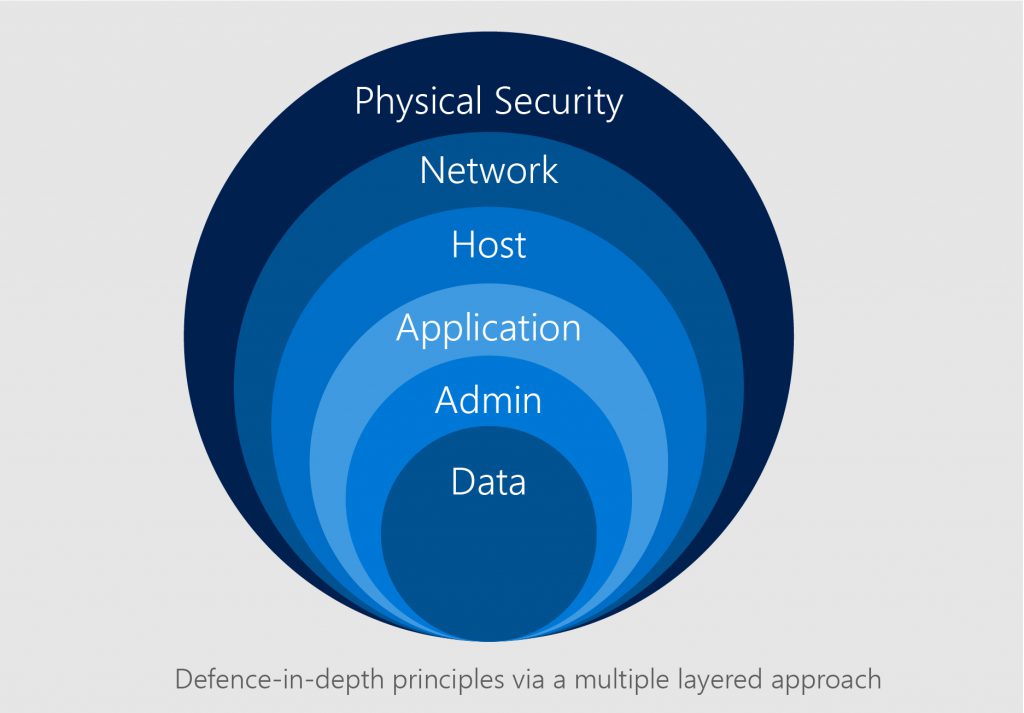
By automating processes and monitoring, security is enhanced by eliminating human intervention. The system constantly scans for anomalies and abnormal behavior to identify threats, malware, and bugs. Anti-malware software is baked into the system and the automated process of identifying threats makes it more secure and agile. Meanwhile, users are offered sophisticated tools to monitor activities on the platform. They can control access to every aspect of their data, prevent unauthorized access and confirm new updates and patches to the software securely.
Our team works with an "Assume Breach" mindset. This means engineers and developers working on Kaizala assume that a data breach has already occurred and their patchwork is crucial in resolving the issue at the earliest. With this mindset, our team has built four pillars of security into the Kaizala system:
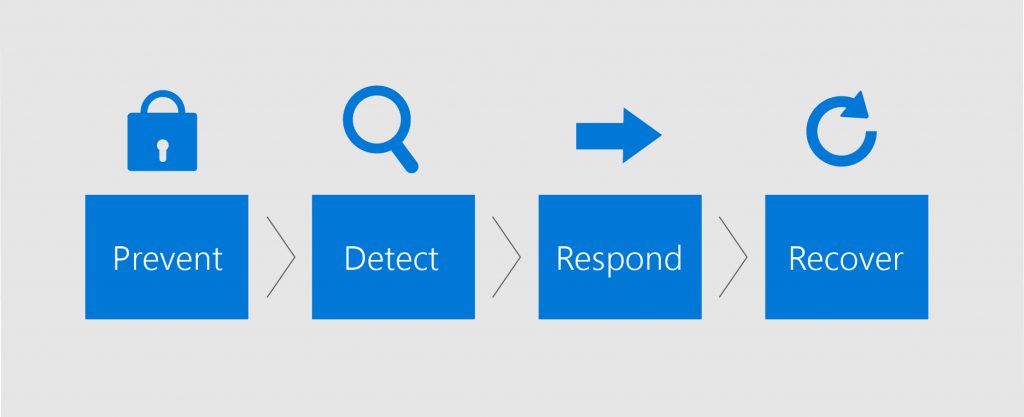
- Prevent: A system of continuous monitoring and incremental improvements help keep Kaizala secure. Tools such as multi-factor authentication and DDoS detection help mitigate the risk of an attack on data.
- Detect: A massive internal analysis system collects and collates security alerts. Machine learning is applied to these external and internal alerts to improve the way the system detects threats.
- Respond: The system automatically responds to a data breach by shutting off access to sensitive data and applying tools to resolve the issue.
- Recover: Once the threat has been resolved, the system updates the necessary components and brings the service back online for regular use.
Privacy and encryption
Data encryption at rest helps us secure data flowing across the Kaizala network. FIPS 140-2 (Federal Information Processing Standard) compliant hashing algorithms, approved by the Microsoft Crypto Board, are used to encrypt data and manage cryptographic keys. We regularly scan the source code to ensure long-term data security.
Communication across the Kaizala platform is carried out over the HTTPS protocol. Only TLS 1.2 is enabled, which exceeds basic standards for security. We go a step further and configure TLS 1.2 to disable TLS compression and insecure renegotiation.
Centralized secret management tools help provide discreet access to admins in the Office Services Infrastructure environment. All user data is stored on the device’s internal memory and quarantined from other apps and external storage devices through Application Sandbox.
Group security on Kaizala goes a step further. One Time Passwords (OTPs) and Azure Active Directory services are used to verify each user and allow admins to control who joins a group. Group admins can ask for more identity details from each user and manage the way files and messages are shared, forwarded, or copied between members.
Deeper security management with Microsoft Intune
Admins can use Microsoft Intune for advanced management of Kaizala. The cloud-based mobile device management (MDM) and mobile application management (MAM) solution allows admins to control data on groups more thoroughly.
Intune enables unparalleled control of the Kaizala ecosystem. Admins can implement the need for a mobile PIN, restrict data transfer, block screen sharing, and even wipe off data on the group at regular intervals. Businesses using Intune alongside Kaizala can combine seamless communication with the highest level of data control. With these features, single-use devices can be created for an entire pool of employees. Admins retain access control for specific devices and users, which allows the team to bring their own devices to work and connect to the system without compromising data security.
Earning trust with a relentless commitment to security
The importance of security in everyday business communication cannot be undermined. With customers entrusting us with their data, building security into our apps by design is not only a vital imperative but a relentless commitment.
Kaizala has been engineered from the ground-up with compliance, security, encryption, and privacy features that set it apart from other enterprise-focused apps. The level of security built into the app by design exceeds industry standards. This is how stakeholders such as employees, customers and partners can communicate through the platform with peace of mind knowing that their most valuable asset remains protected with industry-leading best-practices.
-