Claims aware Wcf service that consumes a custom STS
I thought of creating a step by step document on how to enable a WCF claims base that authenticates user through a custom STS.
Custom STS creation:
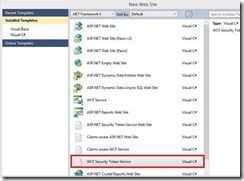
1- Open Visual Studio and choose File à New à Web Sites
2- Select “WCF Security Token Service” from the “New Web Site” windows
VS will automatically generate an STS which is also hosted in IIS.
There is an entry in the associated web.config which I would like to outline:
<appSettings>
<add key="IssuerName" value="ActiveSTS"/>
<add key="SigningCertificateName" value="CN=STSTestCert"/>
<add key="EncryptingCertificateName" value="CN=DefaultApplicationCertificate"/>
</appSettings>
In the above entries, the custom STS will use STSTestCert Certificate to sign the user token.
Likewise, DefaultApplicationCertificate will be used to encrypt the user token.
As I had my own cert, I made the following changes:
<appSettings>
<add key="IssuerName" value="ActiveSTS"/>
<add key="SigningCertificateName" value="CN=STSTestCert"/>
<add key="EncryptingCertificateName" value="CN=localhost"/>
</appSettings>
The remaining configuration can stay unchanged.
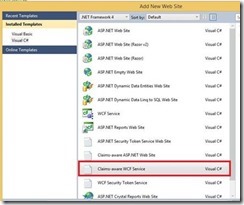
WCF service creation:
1- Create the claims aware WCF service
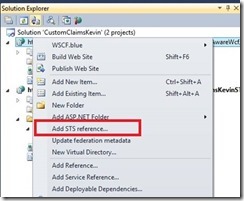
2- Right click on the WCF project and select “Add STS reference” from the menu
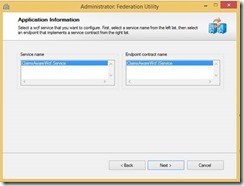
3- Verify that the path to the web.config is correct and pasted in the WCF url in “Application URI” combo box
4- Just click next
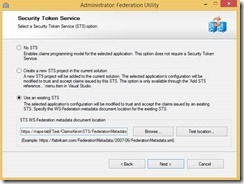
5- Choose “Use an existing STS” and paste in the STS metadata url in the “STS WS-Federation metadata document location” text box.
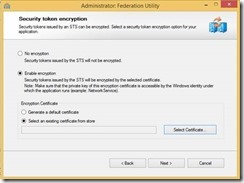
6- We would like to encrypt the claims token. Click on “Select an existing certificate from store” if you already possess one.
Otherwise, choose “Generate a default certificate” to get a self-sign cert which is only good for testing purpose.
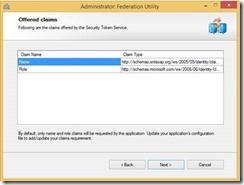
7- Click next as the windows below just shows the default claims that will be serviced to the customer.
8- Click next and terminate.
The config file in the wcf service will be updated. Below is how mine looked like:
1 <system.serviceModel>
2
3 <services>
4
5 <service name="ClaimsAwareWcf.Service" behaviorConfiguration="ClaimsAwareWcf.ServiceBehavior">
6
7 <endpoint address="" binding="ws2007FederationHttpBinding"
8
9 contract="ClaimsAwareWcf.IService" bindingConfiguration="ClaimsAwareWcf.IService_ws2007FederationHttpBinding" />
10
11 </service>
12
13 </services>
14
15 <behaviors>
16
17 <serviceBehaviors>
18
19 <behavior name="ClaimsAwareWcf.ServiceBehavior">
20
21 <federatedServiceHostConfiguration name="ClaimsAwareWcf.Service" />
22
23 <serviceMetadata httpGetEnabled="true" httpsGetEnabled="true" />
24
25 <serviceDebug includeExceptionDetailInFaults="false" />
26
27 <serviceCredentials>
28
29 <serviceCertificate findValue="7b2a501d8fe488c7b03f53e569081763d1326abc" storeLocation="LocalMachine" storeName="My" x509FindType="FindByThumbprint" /> <-------------------- This cert matches localhost cert in STS
30
31 </serviceCredentials>
32
33 </behavior>
34
35 </serviceBehaviors>
36
37 </behaviors>
38
39 <extensions>
40
41 <behaviorExtensions>
42
43 <add name="federatedServiceHostConfiguration" type="Microsoft.IdentityModel.Configuration.ConfigureServiceHostBehaviorExtensionElement, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" />
44
45 </behaviorExtensions>
46
47 </extensions>
48
49 <bindings>
50
51 <ws2007FederationHttpBinding>
52
53 <binding name="ClaimsAwareWcf.IService_ws2007FederationHttpBinding">
54
55 <security mode="TransportWithMessageCredential">
56
57 <message>
58
59 <issuerMetadata address="https://nape-lab/Test/ClaimsKevinSTS/Service.svc/mex" />
60
61 <issuer address="https://nape-lab/Test/ClaimsKevinSTS/Service.svc" />
62
63 <claimTypeRequirements>
64
65 <add claimType="https://schemas.xmlsoap.org/ws/2005/05/identity/claims/name" isOptional="true" />
66
67 <add claimType="https://schemas.microsoft.com/ws/2008/06/identity/claims/role" isOptional="true" />
68
69 </claimTypeRequirements>
70
71 </message>
72
73 </security>
74
75 </binding>
76
77 </ws2007FederationHttpBinding>
78
79 </bindings>
80
81 </system.serviceModel>
82
83 <microsoft.identityModel>
84
85 <service name="ClaimsAwareWcf.Service">
86
87 <audienceUris>
88
89 <add value="https://nape-lab/Test/ClaimsAwareWcf/Service.svc" />
90
91 </audienceUris>
92
93 <issuerNameRegistry type="Microsoft.IdentityModel.Tokens.ConfigurationBasedIssuerNameRegistry, Microsoft.IdentityModel, Version=3.5.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35">
94
95 <trustedIssuers>
96
97 <add thumbprint="C2E209589102D975A2807CA5D50BFC65FD67FEB5" <--------------------------------------- This cert matches the STSTestCert cert in STS
98
99 name="https://nape-lab/Test/ClaimsKevinSTS/Service.svc" />
100
101 </trustedIssuers>
102
103 </issuerNameRegistry>
104
105 </service>
106
107 </microsoft.identityModel>
108
109
110
111
WCF client creation:
In order to create a WCF client, you will need to Add a Service Reference to your client project.
This will generate new tags in your config file.
You can modify them as follows:
Config file:
1 <configuration>
2
3 <system.serviceModel>
4
5 <bindings>
6
7 <ws2007FederationHttpBinding>
8
9 <binding name="WS2007FederationHttpBinding_IService">
10
11 <security mode="TransportWithMessageCredential">
12
13 <message>
14
15 <issuer address="https://nape-lab/Test/ClaimsKevinSTS/Service.svc/IWSTrust13"
16
17 binding="ws2007HttpBinding" bindingConfiguration="ws2007" />
18
19 <issuerMetadata address="https://nape-lab/Test/ClaimsKevinSTS/Service.svc/mex" />
20
21 <tokenRequestParameters>
22
23 <trust:SecondaryParameters xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">
24
25 <trust:KeyType xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">https://docs.oasis-open.org/ws-sx/ws-trust/200512/SymmetricKey</trust:KeyType>
26
27 <trust:KeySize xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">256</trust:KeySize>
28
29 <trust:Claims Dialect="https://schemas.xmlsoap.org/ws/2005/05/identity"
30
31 xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">
32
33 <wsid:ClaimType Uri="https://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"
34
35 Optional="true" xmlns:wsid="https://schemas.xmlsoap.org/ws/2005/05/identity" />
36
37 <wsid:ClaimType Uri="https://schemas.microsoft.com/ws/2008/06/identity/claims/role"
38
39 Optional="true" xmlns:wsid="https://schemas.xmlsoap.org/ws/2005/05/identity" />
40
41 </trust:Claims>
42
43 <trust:KeyWrapAlgorithm xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">https://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p</trust:KeyWrapAlgorithm>
44
45 <trust:EncryptWith xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">https://www.w3.org/2001/04/xmlenc#aes256-cbc</trust:EncryptWith>
46
47 <trust:SignWith xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">https://www.w3.org/2000/09/xmldsig#hmac-sha1</trust:SignWith>
48
49 <trust:CanonicalizationAlgorithm xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">https://www.w3.org/2001/10/xml-exc-c14n#</trust:CanonicalizationAlgorithm>
50
51 <trust:EncryptionAlgorithm xmlns:trust="https://docs.oasis-open.org/ws-sx/ws-trust/200512">https://www.w3.org/2001/04/xmlenc#aes256-cbc</trust:EncryptionAlgorithm>
52
53 </trust:SecondaryParameters>
54
55 </tokenRequestParameters>
56
57 </message>
58
59 </security>
60
61 </binding>
62
63 </ws2007FederationHttpBinding>
64
65 <ws2007HttpBinding>
66
67 <binding name="ws2007">
68
69 <security mode="Message">
70
71 <message establishSecurityContext="false" />
72
73 </security>
74
75 </binding>
76
77 </ws2007HttpBinding>
78
79 </bindings>
80
81 <client>
82
83 <endpoint address="https://nape-lab/Test/ClaimsAwareWcf/Service.svc"
84
85 binding="ws2007FederationHttpBinding" bindingConfiguration="WS2007FederationHttpBinding_IService"
86
87 contract="ServiceClaimsRef.IService" name="WS2007FederationHttpBinding_IService" />
88
89 </client>
90
91 </system.serviceModel>
92
93 </configuration>
94
95
Calling the service:
1 static void Main(string[] args)
2
3 {
4
5 ServiceClient proxy = new ServiceClient();
6
7 Console.WriteLine(proxy.GetData(20));
8
9 Console.ReadKey();
10
11 }
12