Setup and configuration
We briefly discussed how to setup or enable PrintVerifier here. But I thought setup and configuration deserve a dedicated post. So here goes.
- Install: PrintVerifier is part of the AppVerifier install package. You can download AppVerifier from here.
- Settings: Enable PrintVerifier for the desired processes. The graphical way to do this is by opening AppVerifier, adding the application/process you want to verify and checking the Printing group box. You can also check the PrintAPI and/or PrintDriver boxes individually. Some typical processes that we enable verification in our internal testing are:
- Spoolsv.exe (core print spooler service)
- PrintFilterPipelineSvc.exe (filter pipeline host process)
- Splwow64.exe (64-bit print thunk process for 32-bit application printing)
- All print test applications
- Debugger setup: The application being verified should run under a user-mode debugger since it will break into a debugger when an error occurs. See the section titled "Debugger install and setup" in the AppVerifier help documentation for more info.
That's pretty much it in terms of setup. But there are some nuances that need to be called out here.
- AppVerifier settings are not persisted for running processes. So in order for any changes to the settings to persist, you need to restart the application/process.
- The settings are persistent until explicitly deleted. Therefore, no matter how many times you launch an application it will start with AppVerifier enable until the settings are deleted.
- If you are verifying your driver, you need to enable AppVerifier for the process in whose context your driver will be loaded. UI plug-ins are loaded in the application process context, while rendering plug-ins are for the most part loaded in the spooler process context. As for XPSDrv filters, they are loaded in the filter pipeline server process context.
- Do NOT enable PrintVerifier for system processes such as csrss.exe, lsass.exe, winlogon.exe etc.
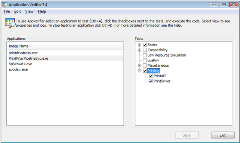
Here is a screen shot of the AppVerifier UI with the Basics and Printing layers enabled for a few processes.
AppVerifier also supports command line setup. I am including a snapshot of the command line usage below.
D:\>appverif -?
Application Verifier 3.3.0047
Copyright (c) Microsoft Corporation. All rights reserved.
Application Verifier Command Line Usage:
-enable TEST ... -for TARGET ... [-with [TEST.]PROPERTY=VALUE ...]
-disable TEST ... -for TARGET ...
-query TEST ... -for TARGET ...
-configure STOP ... -for TARGET ... -with PROPERTY=VALUE...
-verify TARGET [-faults [PROBABILITY [TIMEOUT [DLL ...]]]]
-export log -for TARGET -with To=XML_FILE [Symbols=SYMBOL_PATH] [StampFrom=LOG_STAMP] [StampTo=LOG_STAMP] [Log=RELAT
IVE_TO_LAST_INDEX]
-delete [logs|settings] -for TARGET ...
-stamp log -for TARGET -with Stamp=LOG_STAMP [Log=RELATIVE_TO_LAST_INDEX]
-logtoxml LOGFILE XMLFILE
-installprovider PROVIDERBINARY
Available Tests:
Heaps
COM
RPC
Handles
Locks
Memory
TLS
Exceptions
DirtyStacks
LowRes
DangerousAPIs
TimeRollOver
Threadpool
Hangs
HighVersionLie
FilePaths
KernelModeDriverInstall
InteractiveServices
Security
Encryption
LuaPriv
PrintAPI
PrintDriver
Service
(For descriptions of tests, run appverif.exe in GUI mode.)
Examples:
appverif -enable handles locks -for foo.exe bar.exe
(turn on handles locks for foo.exe & bar.exe)
appverif -enable heaps handles -for foo.exe -with heaps.full=false
(turn on handles and normal pageheap for foo.exe)
appverif -enable heaps -for foo.exe -with full=true dlls=mydll.dll
(turn on full pageheap for the module of mydll.dll in the foo.exe
appverif -enable * -for foo.exe
(turn on all tests for foo.exe)
appverif -disable * -for foo.exe bar.exe
(turn off all tests for foo.exe & bar.exe)
appverif -disable * -for *
(wipe out all the settings in the system)
appverif -export log -for foo.exe -with to=c:\sample.xml
(export the most recently log associated with foo.exe to c:\sample.xml)
appverif /verify notepad.exe /faults 5 1000 kernel32.dll advapi32.dll
(enable fault injection for notepad.exe. Faults should happen with
probability 5%, only 1000 msecs after process got launched and only
for operations initiated from kernel32.dll and advapi32.dll)
As you can see you can perform a number of tasks from the command line which makes for easy scripting. In fact, that is precisely what we do in our internal testing. Every time one of our test machines gets re-imaged, our machine management harness runs a script that installs AppVerifier and enables PrintVerifier on a pre-defined list of processes. We also run a script to setup the processes in this list to always run under a user-mode debugger. This ensures that we always catch PrintVerifier breaks in the debugger allowing folks to debug through a live session.