Reduce AppFabric Calls to Active Directory for SharePoint Farms
AppFabric is a key part of any SharePoint 2013 as we all know by now. It’s used for many things indeed all over the product and AppFabric in turn uses Active Directory to make sure only authorised processes get access to the cache data.
Thus when SharePoint uses AppFabric, it opens a new TCP connection to it and AppFabric has to authenticate that connection with Active Directory; the same as when a user/browser connects to a Windows authentication protected website. Just as with the browser/IIS connection, there’s two ways of authenticating to AppFabric – NTLM or Kerberos, with NTLM being picked if Kerberos isn’t setup. Given Kerberos is a more efficient protocol at caching authorisation we want to use that over NTLM to reduce traffic to AD as it’s just better designed in that respect.
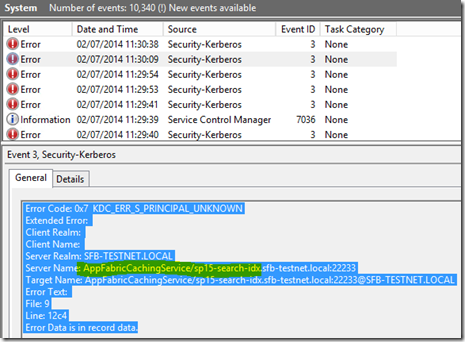
If you have Kerberos logging enabled on a web-front-end for example, something you’ll notice is these SPNs being requested and not being found:
Notice anything about the SPN? Yep, it’s the AppFabric server we’re trying to use – the client (SharePoint) is trying to connect via Kerberos and it’s not working so we have to fail-back silently to NTLM. That works of course as far as SharePoint’s concerned but we have generated more traffic than we wanted due to this security protocol fall-back.
Add AppFabric SPNs to Reduce Calls to Active Directory
As with HTTP, we want to use Kerberos for AppFabric authentication to reduce the extra logins to Active Directory. This is just done by adding the right SPNs to the app-fabric account in the form of:
- AppFabricCachingService/server:22233
- AppFabricCachingService/server.domain.fqdn:22233
This you do with either ADSI Edit or setspn; in my example:
- setspn -U -S AppFabricCachingService/sp15-search-crl:22233@SFB-TESTNET.LOCAL sfb-testnet\svc_cache
That should take care of both SPNs but you might want to try adding the NetBIOS one too manually – Win2012 will duplicate-check the SPN first anyway so there’s no risk. Check the security log again after the change with Kerberos logging enabled to double-check it’s worked if you’re unsure. First though, restart AppFabric (and if I remember right IIS might be necessary too) and you should be good to go – AppFabric will make significantly less calls to Active Directory as it’ll use a Kerberos token instead.
If this is of particular interest I can probably expand on this subject, but that’s it for now.
Cheers!
// Sam Betts