The Use of Cloud Storage Services to Distribute Malware
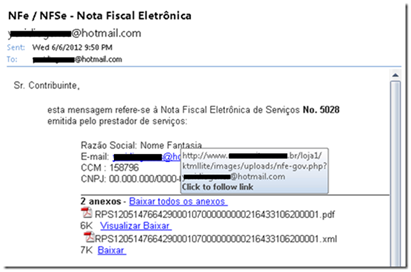
Recently I received an interesting e-mail (in Portuguese) and it was clearly a phishing e-mail, however I got curious to understand what it was and decided to investigate further. The e-mail content is shown below:
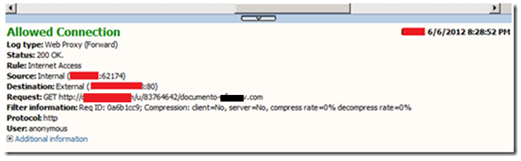
The destination URL shows up in the screenshot above because I pointed the cursor to the link and clearly it shows that it was not a valid link for the purpose of the e-mail content. I copied the URL and pasted in a isolated workstation in my lab environment. In this lab environment I have Forefront TMG in the edge which is also isolated from my production network. Once I pasted this link in the browser this is what TMG showed to me:
I’m not going to reveal the full URL, but this is a free cloud storage service. As this is a free cloud storage service (and valid one), TMG (leveraging Microsoft Reputation Services) categorize this as Personal Network Storage as shown below:
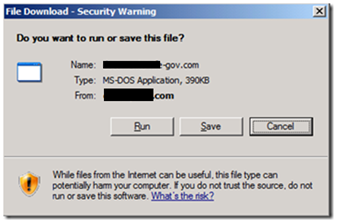
Since it passed through this filter successfully it landed in the user’s workstation with the following message:
Notice that the name of the file is actually the name of the domain trying to appear as a valid GOV domain (since the content has to do with GOV document). Using IDA PRO to disassembler the file was possible to see that the executable file as build using Borland Delphi:
There was some calls to verify disk space:
…and some other things, which are not part of the scope of this post. The goal here is to show the following points:
- Cloud Storage services can be used in malicious scenarios like this one, where a phishing e-mail is sent to persuade the user to click and download something that appears to be valid.
- The edge device that is filtering the content might not be able to block this access because it seems to be coming from a valid location.
- If the malware is exploiting a zero day vulnerability, the endpoint protection (anti-virus) might not be able to catch and block the malware.
So where everything started? A phishing e-mail persuading the user to click on something. While we all know that the end user is the weakest point in the security chain, we need to continually work in a defense in depth approach where all points are mitigated. Technology can help until certain point and educate the users can complement that. In an article that I wrote almost one year ago I explain why is important to invest in Security Awareness training and the same thing stands true today.
Note: I originally wrote this text as part of an article about Cloud Storage Services Security to the 7th Edition of the Brazilian Portuguese Magazine called “Segurança Digital” (Digital Security). The full magazine (in PDF and Portuguese) is available here (the article is on page 39).