How to register a daemon app that calls web APIs
For a daemon application, here's what you need to know when you register the app.
Supported account types
When creating the application in your in Microsoft Entra tenant, choose one of the following options for your app registration:
- Accounts in this organizational directory only. This choice is the most common one because daemon applications are written by line-of-business (LOB) developers.
- Accounts in any organizational directory. You'll make this choice if you're an Independent Software Vendor (ISV) providing a utility tool to your customers. You'll need your customers' tenant admins to approve it.
Authentication - no reply URI needed
In the case where your confidential client application uses only the client credentials flow, the reply URI doesn't need to be registered. It's not needed for the application configuration or construction. The client credentials flow doesn't use it.
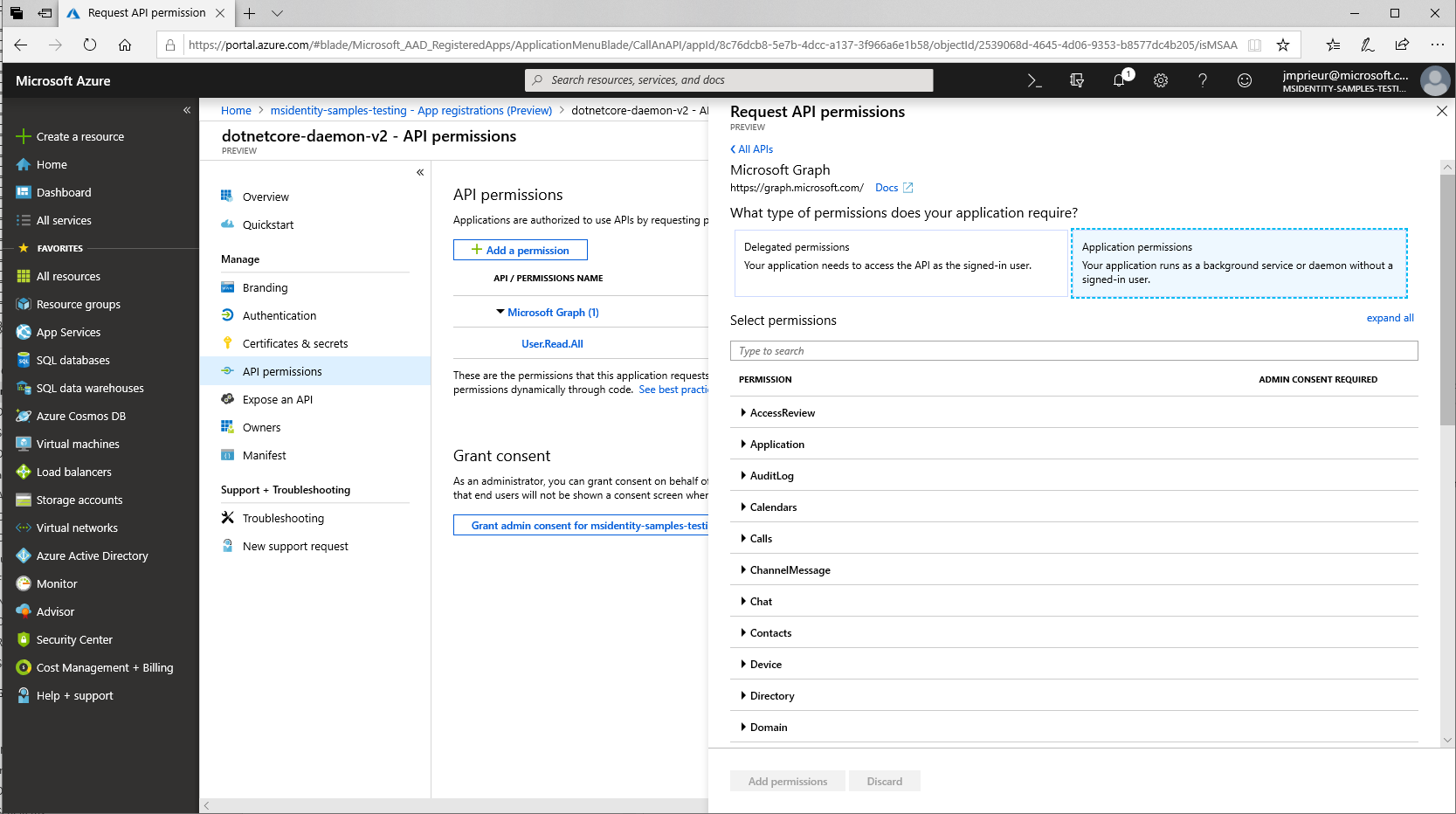
API permissions - app permissions and admin consent
A daemon application can request only application permissions to APIs (not delegated permissions). On the API permissions page for the application registration, after you've selected Add a permission and chosen the API family, choose Application permissions, and then select your permissions.
The web API that you want to call needs to define Application permissions (app roles), not delegated permissions. For details on how to expose such an API, see Protected web API: App registration - when your web API is called by a daemon app.
Daemon applications require that a tenant admin pre-consent to the application calling the web API. Tenant admins provide this consent on the same API permission page by selecting Grant admin consent to our organization
If you're an ISV building a multitenant application, you should read the section Deployment - case of multitenant daemon apps.
If you're new to identity and access management (IAM) with OAuth 2.0 and OpenID Connect, or even just new to IAM on the Microsoft identity platform, the following set of articles should be high on your reading list.
Although not required reading before completing your first quickstart or tutorial, they cover topics integral to the platform, and familiarity with them will help you on your path as you build more complex scenarios.
Authentication and authorization
Microsoft identity platform
Next steps
Move on to the next article in this scenario, App code configuration.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for