Tutorial: Microsoft Entra integration with InsideView
In this tutorial, you'll learn how to integrate InsideView with Microsoft Entra ID. This integration provides these benefits:
- You can use Microsoft Entra ID to control who has access to InsideView.
- You can enable your users to be automatically signed in to InsideView (single sign-on) with their Microsoft Entra accounts.
- You can manage your accounts in one central location: the Azure portal.
To learn more about SaaS app integration with Microsoft Entra ID, see Single sign-on to applications in Microsoft Entra ID.
If you don't have an Azure subscription, create a free account before you begin.
Prerequisites
To configure Microsoft Entra integration with InsideView, you need to have:
- A Microsoft Entra subscription. If you don't have a Microsoft Entra environment, you can get a free account.
- An InsideView subscription that has single sign-on enabled.
Scenario description
In this tutorial, you'll configure and test Microsoft Entra single sign-on in a test environment.
- InsideView supports IdP-initiated SSO.
Add InsideView from the gallery
To set up the integration of InsideView into Microsoft Entra ID, you need to add InsideView from the gallery to your list of managed SaaS apps.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
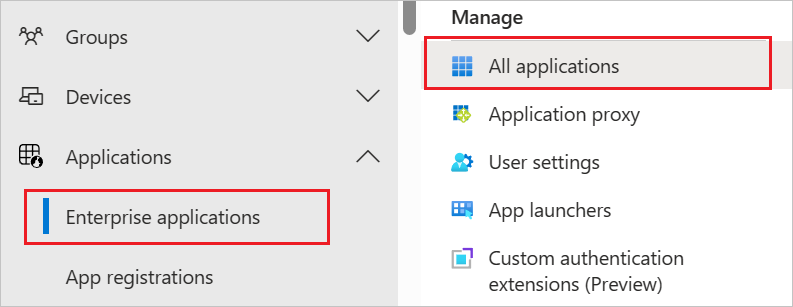
Browse to Identity > Applications > Enterprise applications.
To add an application, select New application at the top of the window:

In the search box, enter InsideView. Select InsideView in the search results and then select Add.

Configure and test Microsoft Entra single sign-on
In this section, you'll configure and test Microsoft Entra single sign-on with InsideView by using a test user named Britta Simon. To enable single sign-on, you need to establish a relationship between a Microsoft Entra user and the corresponding user in InsideView.
To configure and test Microsoft Entra single sign-on with InsideView, you need to complete these steps:
- Configure Microsoft Entra single sign-on to enable the feature for your users.
- Configure InsideView single sign-on on the application side.
- Create a Microsoft Entra test user to test Microsoft Entra single sign-on.
- Assign the Microsoft Entra test user to enable Microsoft Entra single sign-on for the user.
- Create an InsideView test user that's linked to the Microsoft Entra representation of the user.
- Test single sign-on to verify that the configuration works.
Configure Microsoft Entra single sign-on
In this section, you'll enable Microsoft Entra single sign-on.
To configure Microsoft Entra single sign-on with InsideView, take these steps:
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > InsideView
Select Single sign-on:
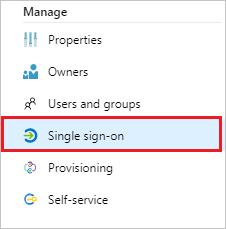
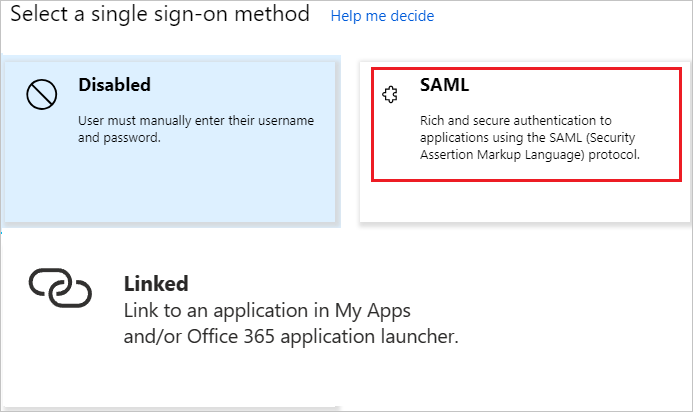
In the Select a single sign-on method dialog box, select SAML/WS-Fed mode to enable single sign-on:
On the Set up Single Sign-On with SAML page, select the Edit icon to open the Basic SAML Configuration dialog box:
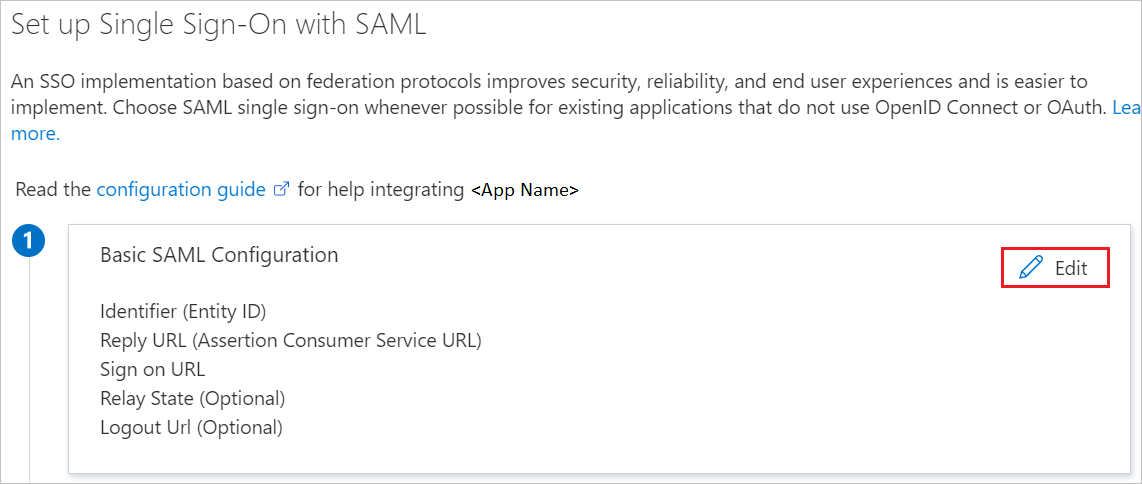
In the Basic SAML Configuration dialog box, take the following steps.
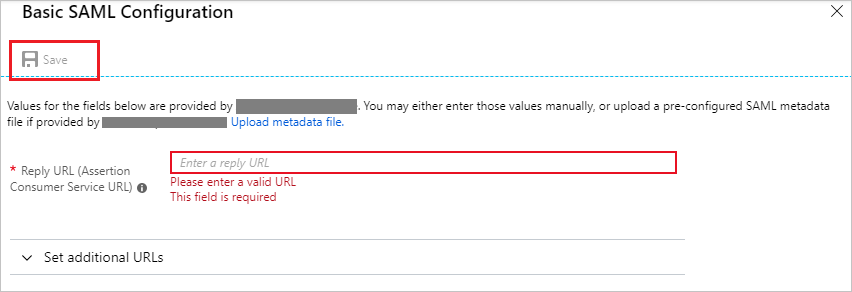
In the Reply URL box, enter a URL in this pattern:
https://my.insideview.com/iv/<STS Name>/login.ivNote
This value is a placeholder. You need to use the actual reply URL. Contact the InsideView support team to get the value. You can also refer to the patterns shown in the Basic SAML Configuration dialog box.
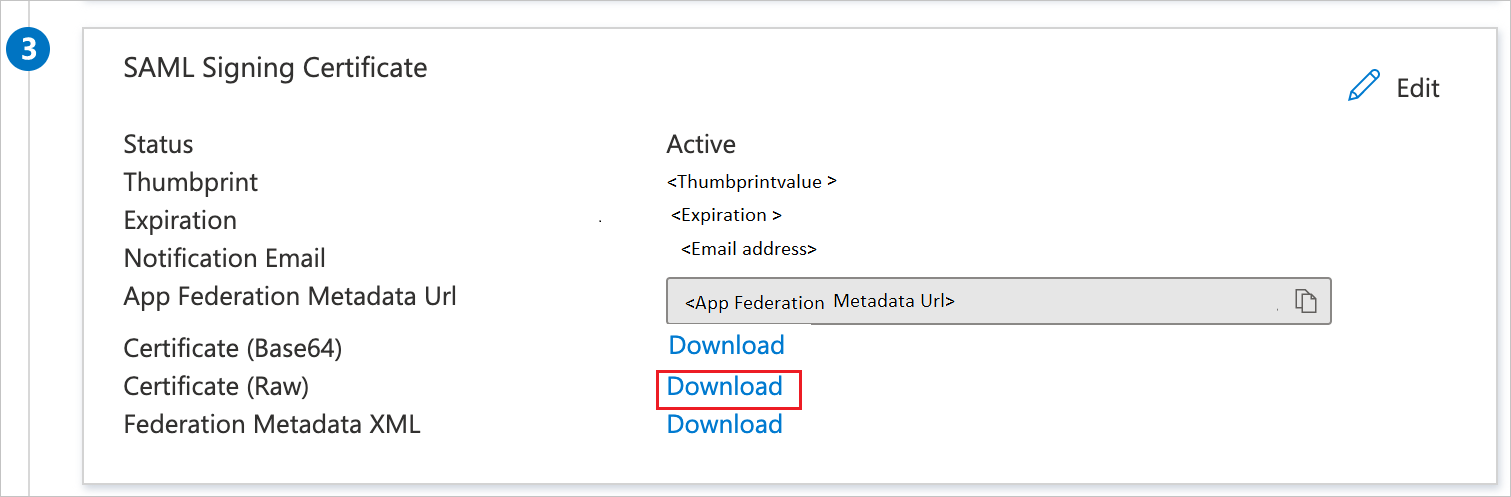
On the Set up Single Sign-On with SAML page, in the SAML Signing Certificate section, select the Download link next to Certificate (Raw), per your requirements, and save the certificate on your computer:
In the Set up InsideView section, copy the appropriate URLs, based on your requirements:
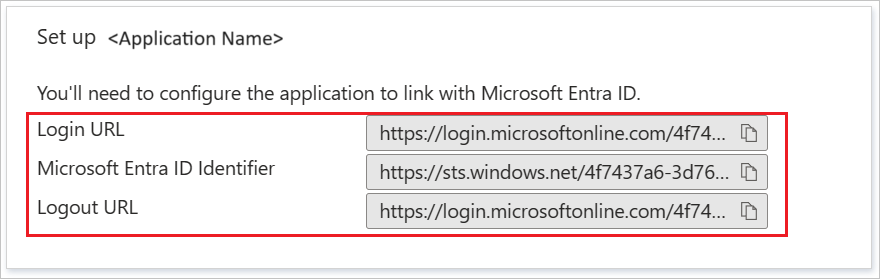
- Login URL.
- Microsoft Entra Identifier.
- Logout URL.
Configure InsideView single sign-on
In a new web browser window, sign in to your InsideView company site as an admin.
At the top of the window, select Admin, SingleSignOn Settings, and then Add SAML.
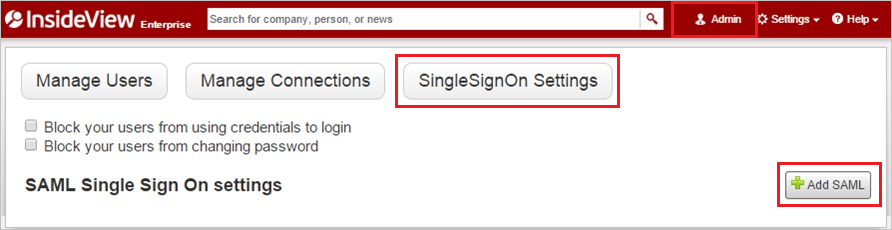
In the Add a New SAML section, take the following steps.
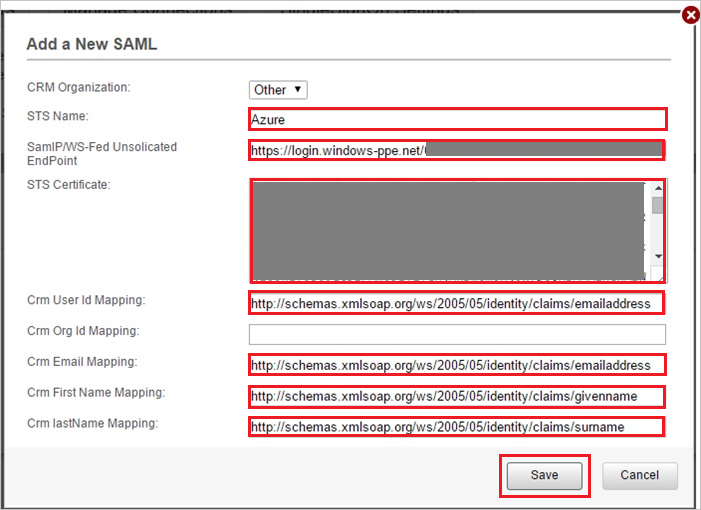
In the STS Name box, enter a name for your configuration.
In the SamlP/WS-Fed Unsolicited EndPoint box, paste the Login URL value that you copied.
Open the Raw certificate that you downloaded. Copy the contents of the certificate to the clipboard, and then paste the contents into the STS Certificate box.
In the Crm User Id Mapping box, enter
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress.In the Crm Email Mapping box, enter
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress.In the Crm First Name Mapping box, enter
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname.In the Crm lastName Mapping box, enter
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname.Select Save.
Create a Microsoft Entra test user
In this section, you'll create a test user named Britta Simon.
- Sign in to the Microsoft Entra admin center as at least a User Administrator.
- Browse to Identity > Users > All users.
- Select New user > Create new user, at the top of the screen.
- In the User properties, follow these steps:
- In the Display name field, enter
B.Simon. - In the User principal name field, enter the username@companydomain.extension. For example,
B.Simon@contoso.com. - Select the Show password check box, and then write down the value that's displayed in the Password box.
- Select Review + create.
- In the Display name field, enter
- Select Create.
Assign the Microsoft Entra test user
In this section, you'll enable Britta Simon to use Azure single sign-on by granting her access to InsideView.
Sign in to the Microsoft Entra admin center as at least a Cloud Application Administrator.
Browse to Identity > Applications > Enterprise applications > InsideView.
In the left pane, select Users and groups:
Select Add user, and then select Users and groups in the Add Assignment dialog box.
In the Users and groups dialog box, select Britta Simon in the users list, and then click the Select button at the bottom of the window.
If you expect a role value in the SAML assertion, in the Select Role dialog box, select the appropriate role for the user from the list. Click the Select button at the bottom of the window.
In the Add Assignment dialog box, select Assign.
Create an InsideView test user
To enable Microsoft Entra users to sign in to InsideView, you need to add them to InsideView. You need to add them manually.
To create users or contacts in InsideView, contact the InsideView support team.
Note
You can use any user account creation tool or API provided by InsideView to provision Microsoft Entra user accounts.
Test single sign-on
Now you need to test your Microsoft Entra single sign-on configuration by using the Access Panel.
When you select the InsideView tile in the Access Panel, you should be automatically signed in to the InsideView instance for which you set up SSO. For more information about the Access Panel, see Access and use apps on the My Apps portal.
Additional resources
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for