Back up Azure VMs in a Recovery Services vault
This article describes how to back up Azure VMs in a Recovery Services vault, using the Azure Backup service.
In this article, you learn how to:
- Prepare Azure VMs.
- Create a vault.
- Discover VMs and configure a backup policy.
- Enable backup for Azure VMs.
- Run the initial backup.
Note
This article describes how to set up a vault and select VMs to back up. It's useful if you want to back up multiple VMs. Alternatively, you can back up a single Azure VM directly from the VM settings.
Before you start
- Review the Azure VM backup architecture.
- Learn about Azure VM backup, and the backup extension.
- Review the support matrix before you configure backup.
In addition, there are a couple of things that you might need to do in some circumstances:
- Install the VM agent on the VM: Azure Backup backs up Azure VMs by installing an extension to the Azure VM agent running on the machine. If your VM was created from an Azure Marketplace image, the agent is installed and running. If you create a custom VM, or you migrate an on-premises machine, you might need to install the agent manually.
Note
The functionality described in the following sections can also be accessed via Backup center. Backup center is a single unified management experience in Azure. It enables enterprises to govern, monitor, operate, and analyze backups at scale. With this solution, you can perform most of the key backup management operations without being limited to the scope of an individual vault.
Create a Recovery Services vault
A Recovery Services vault is a management entity that stores recovery points that are created over time, and it provides an interface to perform backup-related operations. These operations include taking on-demand backups, performing restores, and creating backup policies.
To create a Recovery Services vault:
Sign in to the Azure portal.
Search for Backup center, and then go to the Backup center dashboard.
On the Overview pane, select Vault.
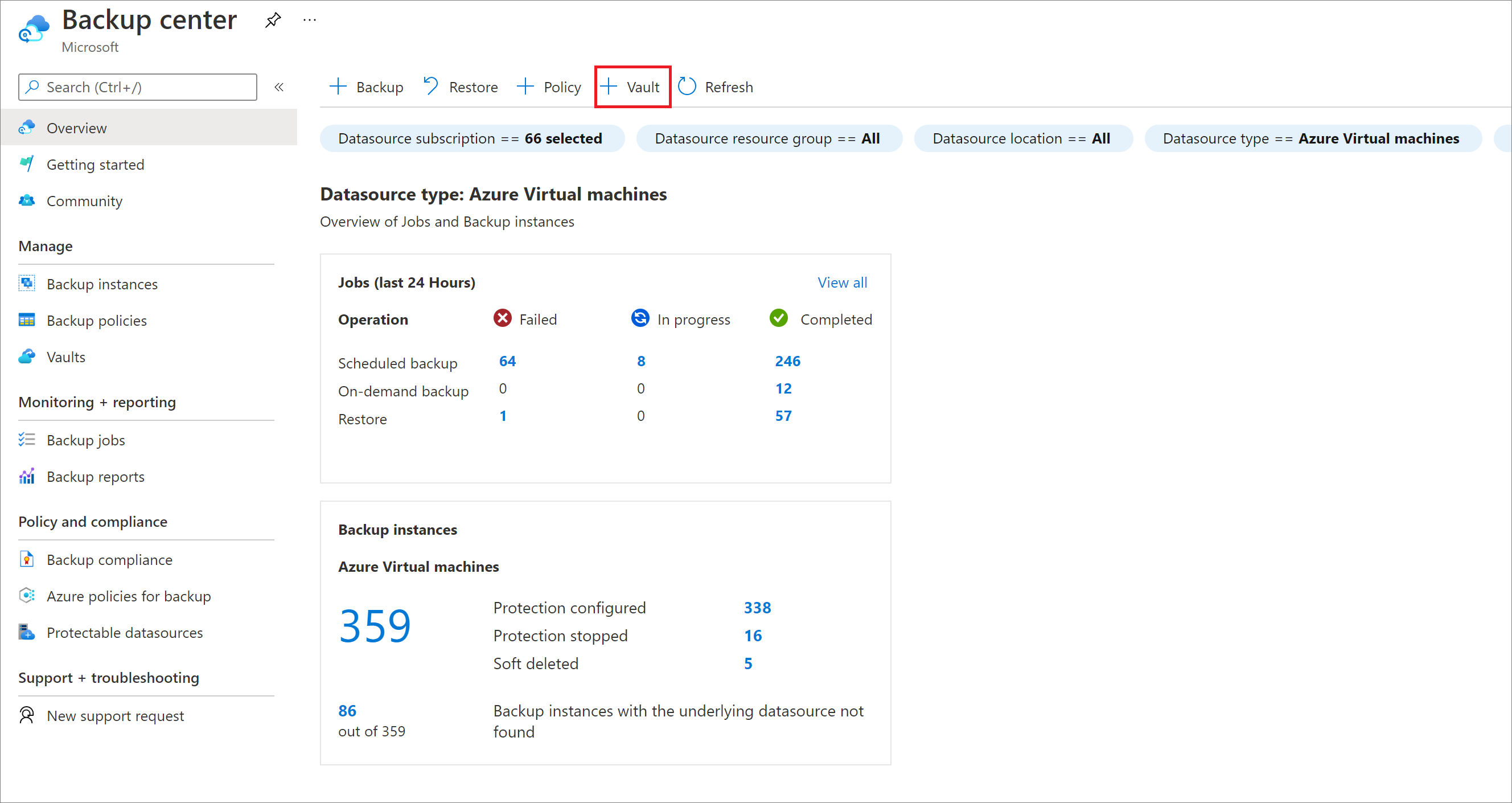
Select Recovery Services vault > Continue.
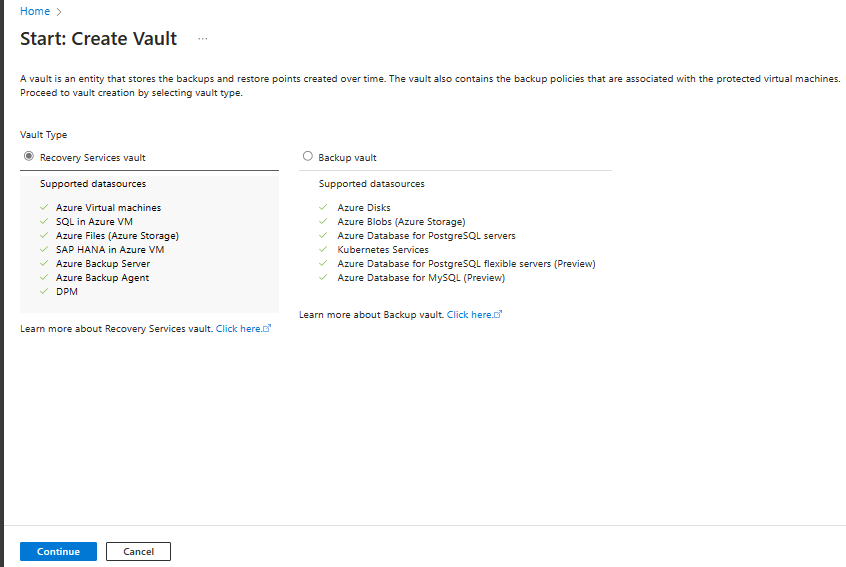
On the Recovery Services vault pane, enter the following values:
Subscription: Select the subscription to use. If you're a member of only one subscription, you'll see that name. If you're not sure which subscription to use, use the default subscription. There are multiple choices only if your work or school account is associated with more than one Azure subscription.
Resource group: Use an existing resource group or create a new one. To view a list of available resource groups in your subscription, select Use existing, and then select a resource in the dropdown list. To create a new resource group, select Create new, and then enter the name. For more information about resource groups, see Azure Resource Manager overview.
Vault name: Enter a friendly name to identify the vault. The name must be unique to the Azure subscription. Specify a name that has at least 2 but not more than 50 characters. The name must start with a letter and consist only of letters, numbers, and hyphens.
Region: Select the geographic region for the vault. For you to create a vault to help protect any data source, the vault must be in the same region as the data source.
Important
If you're not sure of the location of your data source, close the window. Go to the list of your resources in the portal. If you have data sources in multiple regions, create a Recovery Services vault for each region. Create the vault in the first location before you create a vault in another location. There's no need to specify storage accounts to store the backup data. The Recovery Services vault and Azure Backup handle that automatically.
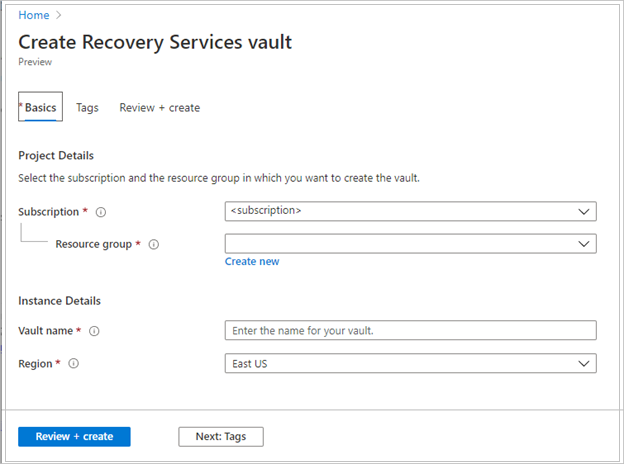
After providing the values, select Review + create.
To finish creating the Recovery Services vault, select Create.
It can take a while to create the Recovery Services vault. Monitor the status notifications in the Notifications area at the upper right. After the vault is created, it appears in the list of Recovery Services vaults. If the vault doesn't appear, select Refresh.
Note
Azure Backup now supports immutable vaults that help you ensure that recovery points once created can't be deleted before their expiry as per the backup policy. You can make the immutability irreversible for maximum protection to your backup data from various threats, including ransomware attacks and malicious actors. Learn more.
Modify storage replication
By default, vaults use geo-redundant storage (GRS).
- If the vault is your primary backup mechanism, we recommend you use GRS.
- You can use locally redundant storage (LRS) for a cheaper option.
- Zone-redundant storage (ZRS) replicates your data in availability zones, guaranteeing data residency and resiliency in the same region.
Modify the storage replication type as follows:
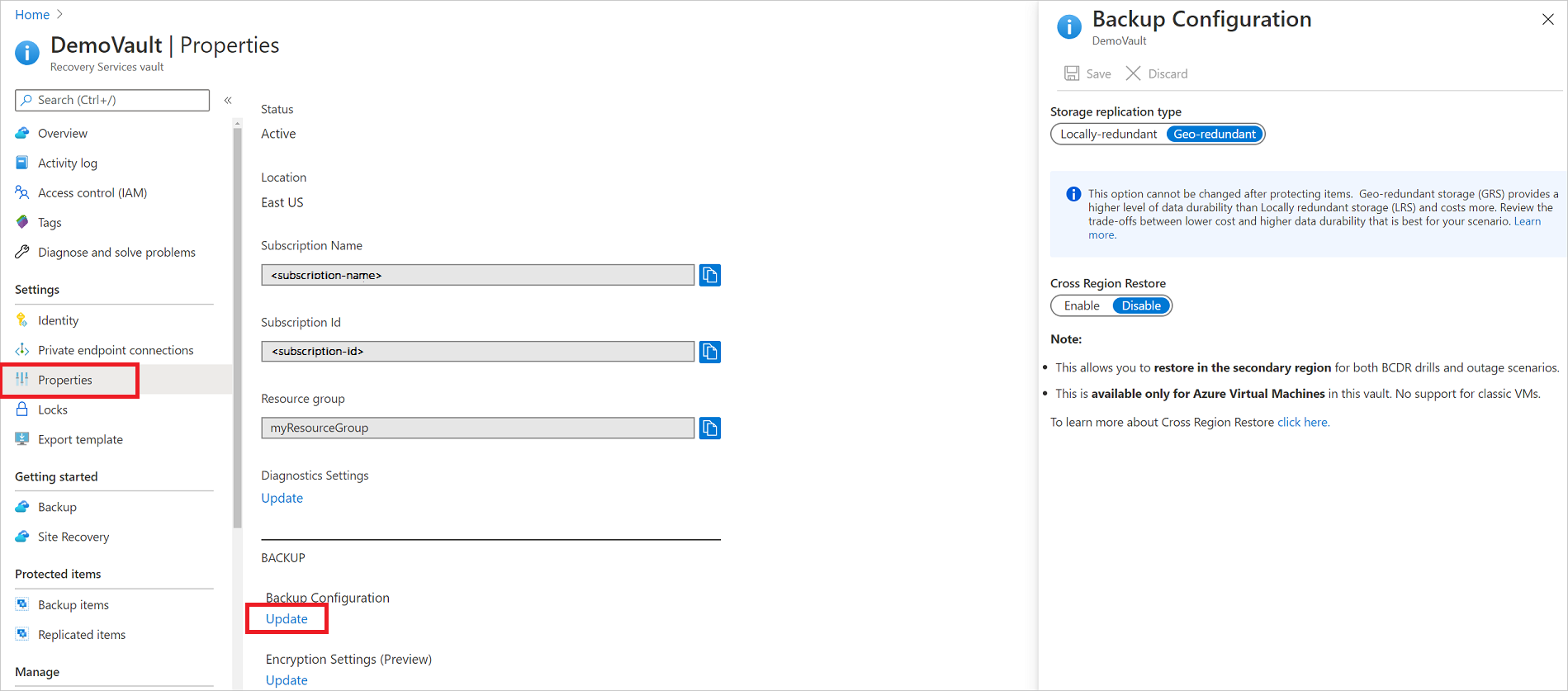
In the new vault, select Properties in the Settings section.
In Properties, under Backup Configuration, select Update.
Select the storage replication type, and select Save.
Note
You can't modify the storage replication type after the vault is set up and contains backup items. If you want to do this you need to recreate the vault.
Apply a backup policy
To apply a backup policy to your Azure VMs, follow these steps:
Go to the Backup center and click +Backup from the Overview tab.
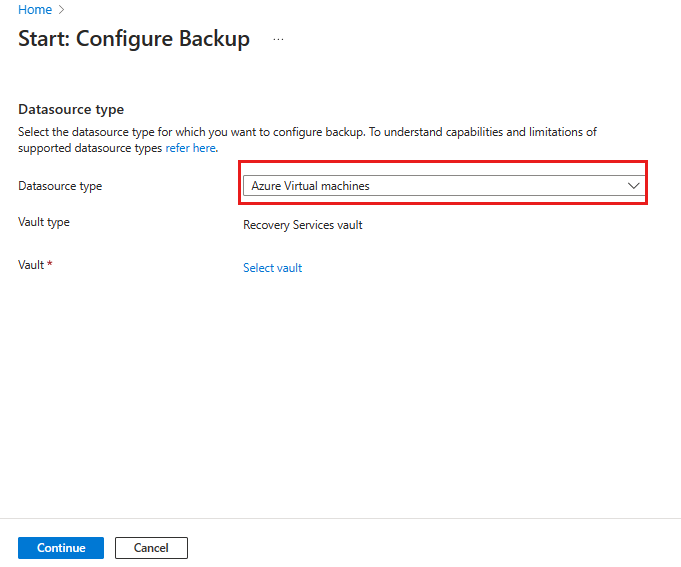
Select Azure Virtual machines as the Datasource type and select the vault you have created. Then click Continue.
Assign a Backup policy.
The default policy backs up the VM once a day. The daily backups are retained for 30 days. Instant recovery snapshots are retained for two days.
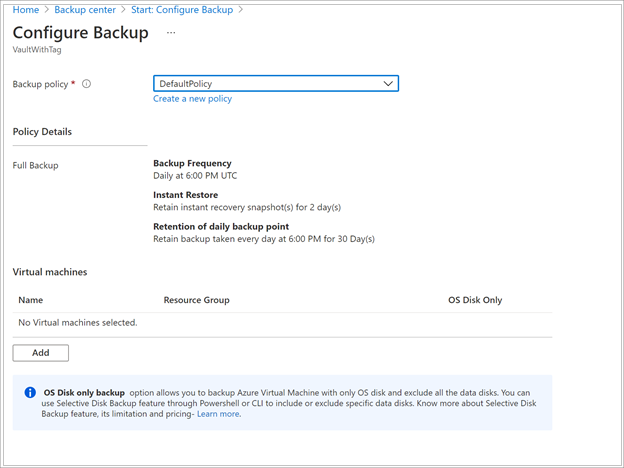
If you don't want to use the default policy, select Create New, and create a custom policy as described in the next procedure.
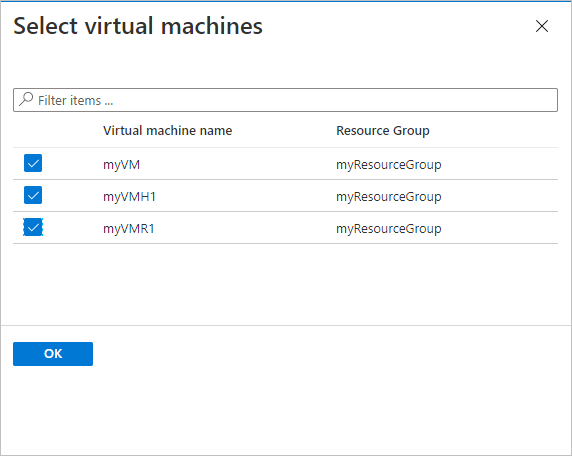
Under Virtual Machines, select Add.

The Select virtual machines pane will open. Select the VMs you want to back up using the policy. Then select OK.
The selected VMs are validated.
You can only select VMs in the same region as the vault.
VMs can only be backed up in a single vault.
Note
All the VMs in the same region and subscription as that of the vault are available to configure backup. When configuring backup, you can browse to the virtual machine name and its resource group, even though you don’t have the required permission on those VMs. If your VM is in soft deleted state, then it won't be visible in this list. If you need to re-protect the VM, then you need to wait for the soft delete period to expire or undelete the VM from the soft deleted list. For more information, see the soft delete for VMs article.
In Backup, select Enable backup. This deploys the policy to the vault and to the VMs, and installs the backup extension on the VM agent running on the Azure VM.
After enabling backup:
- The Backup service installs the backup extension whether or not the VM is running.
- An initial backup will run in accordance with your backup schedule.
- When backups run, note that:
- A VM that's running has the greatest chance for capturing an application-consistent recovery point.
- However, even if the VM is turned off, it's backed up. Such a VM is known as an offline VM. In this case, the recovery point will be crash-consistent.
- Explicit outbound connectivity isn't required to allow backup of Azure VMs.
Create a custom policy
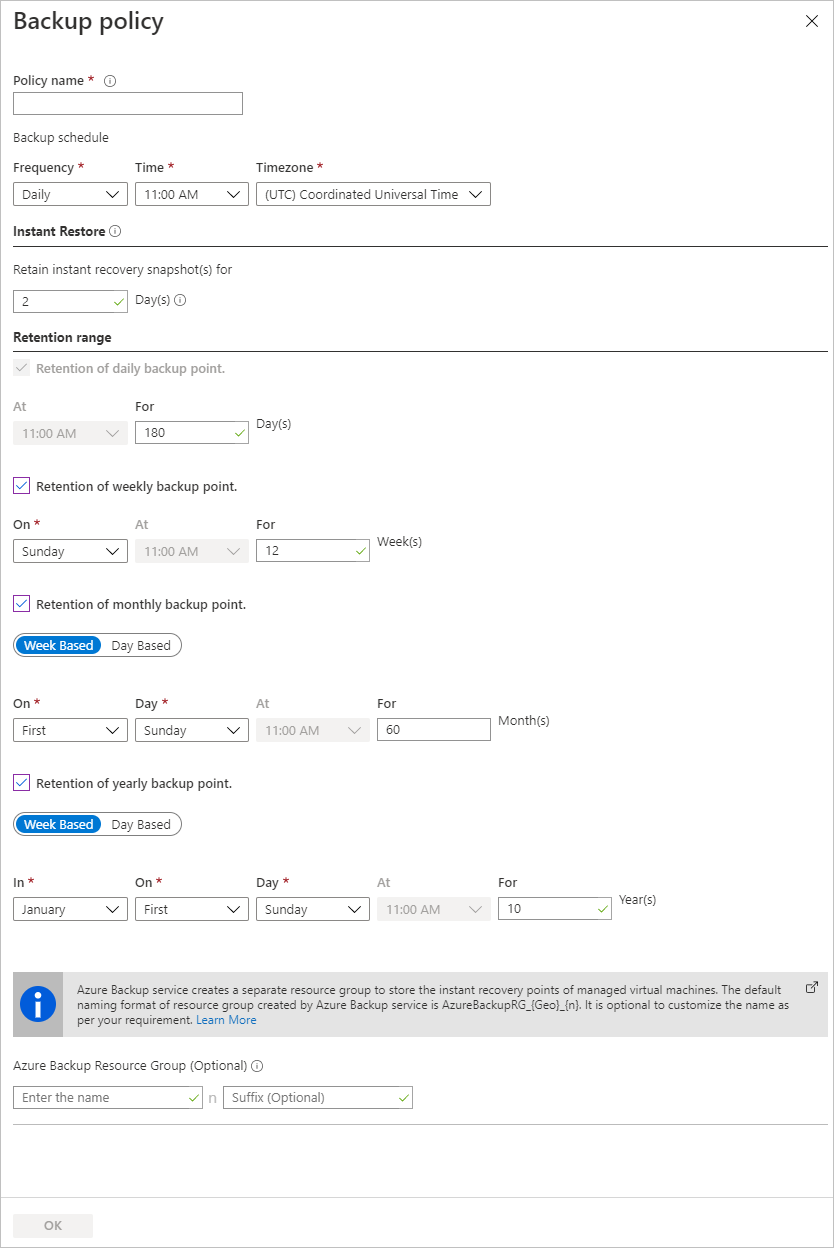
If you selected to create a new backup policy, fill in the policy settings.
In Policy name, specify a meaningful name.
In Backup schedule, specify when backups should be taken. You can take daily or weekly backups for Azure VMs.
In Instant Restore, specify how long you want to retain snapshots locally for instant restore.
- When you restore, backed up VM disks are copied from storage, across the network to the recovery storage location. With instant restore, you can leverage locally stored snapshots taken during a backup job, without waiting for backup data to be transferred to the vault.
- You can retain snapshots for instant restore for between one to five days. The default setting is two days.
In Retention range, specify how long you want to keep your daily or weekly backup points.
In Retention of monthly backup point and Retention of yearly backup point, specify whether you want to keep a monthly or yearly backup of your daily or weekly backups.
Select OK to save the policy.
Note
To store the restore point collection (RPC), the Backup service creates a separate resource group (RG). This RG is different than RG of the VM. Learn more.
Note
- Azure Backup doesn't support automatic clock adjustment for daylight-saving changes for Azure VM backups. As time changes occur, modify backup policies manually as required.
- If you want hourly backups, then you can configure Enhanced backup policy. For more information, see Back up an Azure VM using Enhanced policy.
Trigger the initial backup
The initial backup will run in accordance with the schedule, but you can run it immediately as follows:
- Go to the Backup center and select the Backup Instances menu item.
- Select Azure Virtual machines as the Datasource type. Then search for the VM that you have configured for backup.
- Right-click the relevant row or select the more icon (…), and then click Backup Now.
- In Backup Now, use the calendar control to select the last day that the recovery point should be retained. Then select OK.
- Monitor the portal notifications. To monitor the job progress, go to Backup center > Backup Jobs and filter the list for In progress jobs. Depending on the size of your VM, creating the initial backup may take a while.
Verify Backup job status
The Backup job details for each VM backup consist of two phases, the Snapshot phase followed by the Transfer data to vault phase.
The snapshot phase guarantees the availability of a recovery point stored along with the disks for Instant Restores and are available for a maximum of five days depending on the snapshot retention configured by the user. Transfer data to vault creates a recovery point in the vault for long-term retention. Transfer data to vault only starts after the snapshot phase is completed.
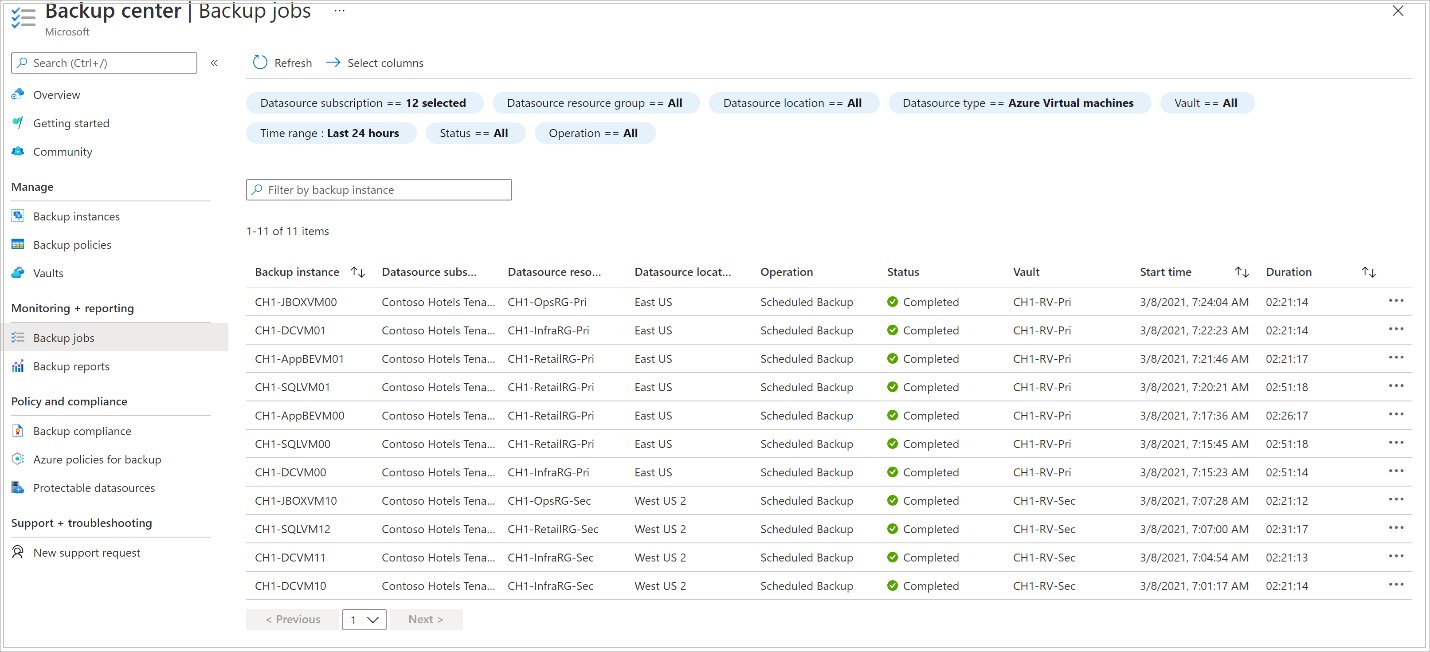
There are two Sub Tasks running at the backend, one for front-end backup job that can be checked from the Backup Job details pane as given below:
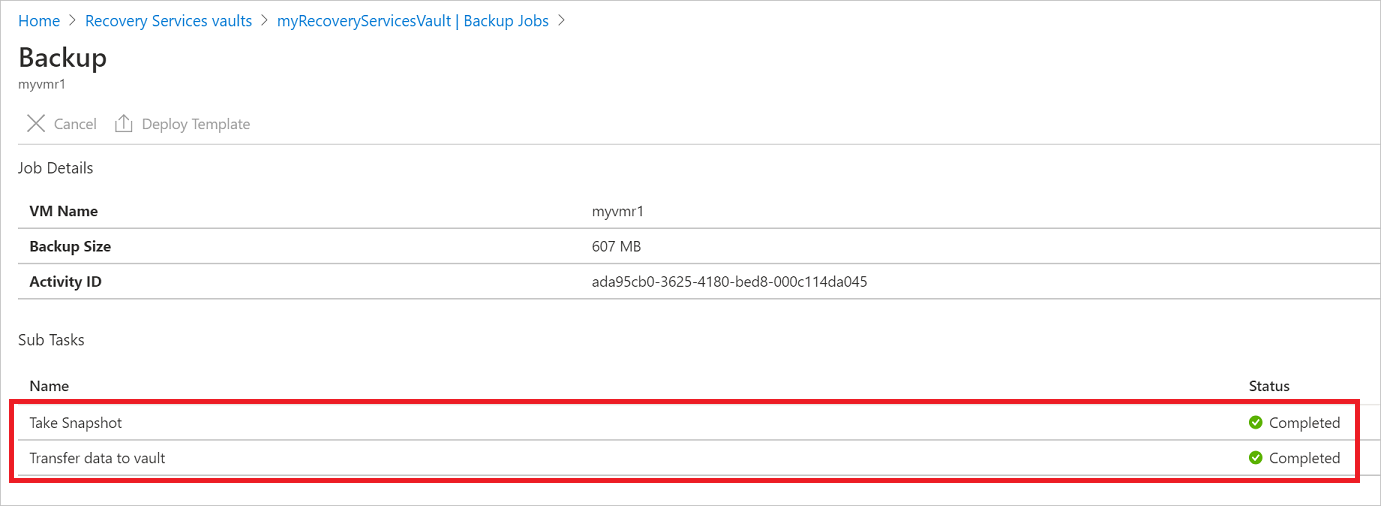
The Transfer data to vault phase can take multiple days to complete depending on the size of the disks, churn per disk and several other factors.
Job status can vary depending on the following scenarios:
| Snapshot | Transfer data to vault | Job Status |
|---|---|---|
| Completed | In progress | In progress |
| Completed | Skipped | Completed |
| Completed | Completed | Completed |
| Completed | Failed | Completed with warning |
| Failed | Failed | Failed |
Now with this capability, for the same VM, two backups can run in parallel, but in either phase (snapshot, transfer data to vault) only one sub task can be running. So in scenarios where a backup job in progress resulted in the next day’s backup to fail, it will be avoided with this decoupling functionality. Subsequent days' backups can have the snapshot completed, while Transfer data to vault is skipped if an earlier day’s backup job is in progress state. The incremental recovery point created in the vault will capture all the churn from the most recent recovery point created in the vault. There's no cost impact on the user.
Optional steps
Install the VM agent
Azure Backup backs up Azure VMs by installing an extension to the Azure VM agent running on the machine. If your VM was created from an Azure Marketplace image, the agent is installed and running. If you create a custom VM, or you migrate an on-premises machine, you might need to install the agent manually, as summarized in the table.
| VM | Details |
|---|---|
| Windows | 1. Download and install the agent MSI file. 2. Install with admin permissions on the machine. 3. Verify the installation. In C:\WindowsAzure\Packages on the VM, right-click WaAppAgent.exe > Properties. On the Details tab, Product Version should be 2.6.1198.718 or higher. If you're updating the agent, make sure that no backup operations are running, and reinstall the agent. |
| Linux | Install by using an RPM or a DEB package from your distribution's package repository. This is the preferred method for installing and upgrading the Azure Linux agent. All the endorsed distribution providers integrate the Azure Linux agent package into their images and repositories. The agent is available on GitHub, but we don't recommend installing from there. If you're updating the agent, make sure no backup operations are running, and update the binaries. |
Next steps
- Troubleshoot any issues with Azure VM agents or Azure VM backup.
- Restore Azure VMs.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for