Protocol support for HTTP headers in Azure Front Door
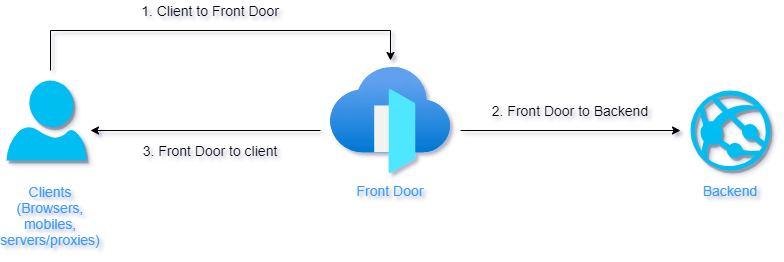
This article outlines the protocol that Front Door supports with parts of the call path (see image). In the following sections, you find information about HTTP headers supported by Front Door.
Important
Azure Front Door doesn't certify any HTTP headers that aren't documented here.
From client to Azure Front Door
Azure Front Door accepts most headers for the incoming request without modifying them. Some reserved headers are removed from the incoming request if sent, including headers with the X-FD-* prefix.
The debug request header, X-Azure-DebugInfo, provides extra debugging information about the Front Door. You need to send X-Azure-DebugInfo: 1 request header from the client to the Azure Front Door to receive optional response headers when Azure Front Door response to the client.
From the Front Door to the backend
Azure Front Door includes headers for an incoming request unless they're removed because of restrictions. Azure Front Door also appends the following headers:
| Header | Example and description |
|---|---|
| Via | Via: 1.1 Azure Front Door adds the client's HTTP version followed by Azure as the value for the Via header. This header indicates the client's HTTP version and that Front Door was an intermediate recipient for the request between the client and the backend. |
| X-Azure-ClientIP | X-Azure-ClientIP: 127.0.0.1 Represents the client IP address associated with the request being processed. For example, a request coming from a proxy might add the X-Forwarded-For header to indicate the IP address of the original caller. |
| X-Azure-SocketIP | X-Azure-SocketIP: 127.0.0.1 Represents the socket IP address associated with the TCP connection that the current request originated from. A request's client IP address might not be equal to its socket IP address because the client IP can be arbitrarily overwritten by a user. |
| X-Azure-Ref | X-Azure-Ref: 0zxV+XAAAAABKMMOjBv2NT4TY6SQVjC0zV1NURURHRTA2MTkANDM3YzgyY2QtMzYwYS00YTU0LTk0YzMtNWZmNzA3NjQ3Nzgz A unique reference string that identifies a request served by Azure Front Door. This string is used to search access logs and critical for troubleshooting. |
| X-Azure-RequestChain | X-Azure-RequestChain: hops=1 A header that Front Door uses to detect request loops, and users shouldn't take a dependency on it. |
| X-Azure-FDID | X-Azure-FDID: 55ce4ed1-4b06-4bf1-b40e-4638452104da A reference string that identifies the request came from a specific Front Door resource. The value can be seen in the Azure portal or retrieved using the management API. You can use this header in combination with IP ACLs to lock down your endpoint to only accept requests from a specific Front Door resource. See the FAQ for more detail |
| X-Forwarded-For | X-Forwarded-For: 127.0.0.1 The X-Forwarded-For (XFF) HTTP header field often identifies the originating IP address of a client connecting to a web server through an HTTP proxy or load balancer. If there's an existing XFF header, then Front Door appends the client socket IP to it or adds the XFF header with the client socket IP. |
| X-Forwarded-Host | X-Forwarded-Host: contoso.azurefd.net The X-Forwarded-Host HTTP header field is a common method used to identify the original host requested by the client in the Host HTTP request header. This is because the host name from Azure Front Door might differ for the backend server handling the request. Any previous value is overridden by Azure Front Door. |
| X-Forwarded-Proto | X-Forwarded-Proto: http The X-Forwarded-Proto HTTP header field is often used to identify the originating protocol of an HTTP request. Front Door based on configuration might communicate with the backend by using HTTPS. This is true even if the request to the reverse proxy is HTTP. Any previous value will be overridden by Front Door. |
| X-FD-HealthProbe | X-FD-HealthProbe HTTP header field is used to identify the health probe from Front Door. If this header is set to 1, the request is from the health probe. It can be used to restrict access from Front Door with a particular value for the X-Forwarded-Host header field. |
From the Front Door to the client
Any headers sent to Azure Front Door from the backend are also passed through to the client. Front Door also attaches the following headers to all responses to the client:
| Header | Example and description |
|---|---|
| X-Azure-Ref | X-Azure-Ref: 0zxV+XAAAAABKMMOjBv2NT4TY6SQVjC0zV1NURURHRTA2MTkANDM3YzgyY2QtMzYwYS00YTU0LTk0YzMtNWZmNzA3NjQ3Nzgz This is a unique reference string that identifies a request served by Front Door, which is critical for troubleshooting as it's used to search access logs. |
| X-Cache | X-Cache: This header describes the caching status of the request. For more information, see Caching with Azure Front Door. |
Optional debug response headers
You need to send X-Azure-DebugInfo: 1 request header to enable the following optional response headers.
| Header | Example and description |
|---|---|
| X-Azure-OriginStatusCode | X-Azure-OriginStatusCode: 503 This header contains the HTTP status code returned by the backend. Using this header you can identify the HTTP status code returned by the application running in your backend without going through backend logs. This status code might be different from the HTTP status code in the response sent to the client by Front Door. This header allows you to determine if the backend is misbehaving or if the issue is with the Front Door service. |
| X-Azure-InternalError | This header contains the error code that Azure Front Door comes across when processing the request. This error indicates the issue is internal to the Azure Front Door service/infrastructure. Report issue to support. |
| X-Azure-ExternalError | X-Azure-ExternalError: 0x830c1011, The certificate authority is unfamiliar This header shows the error code that Front Door servers come across while establishing connectivity to the backend server to process a request. This header helps identify issues in the connection between Front Door and the backend application. This header includes a detailed error message to help you identify connectivity issues to your backend (for example, DNS resolution, invalid cert, and so on.). |
Next steps
- Learn how to create an Azure Front Door profile.
- Learn about how Azure Front Door works.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for