Create a workspace with data exfiltration protection enabled
This article describes how to create a workspace with data exfiltration protection enabled and how to manage the approved Microsoft Entra tenants for this workspace.
Note
You cannot change the workspace configuration for managed virtual network and data exfiltration protection after the workspace is created.
Prerequisites
- Permissions to create a workspace resource in Azure.
- Synapse workspace permissions to create managed private endpoints.
- Subscriptions registered for the Networking resource provider. Learn more.
Follow the steps listed in Quickstart: Create a Synapse workspace to get started with creating your workspace. Before creating your workspace, use the information below to add data exfiltration protection to your workspace.
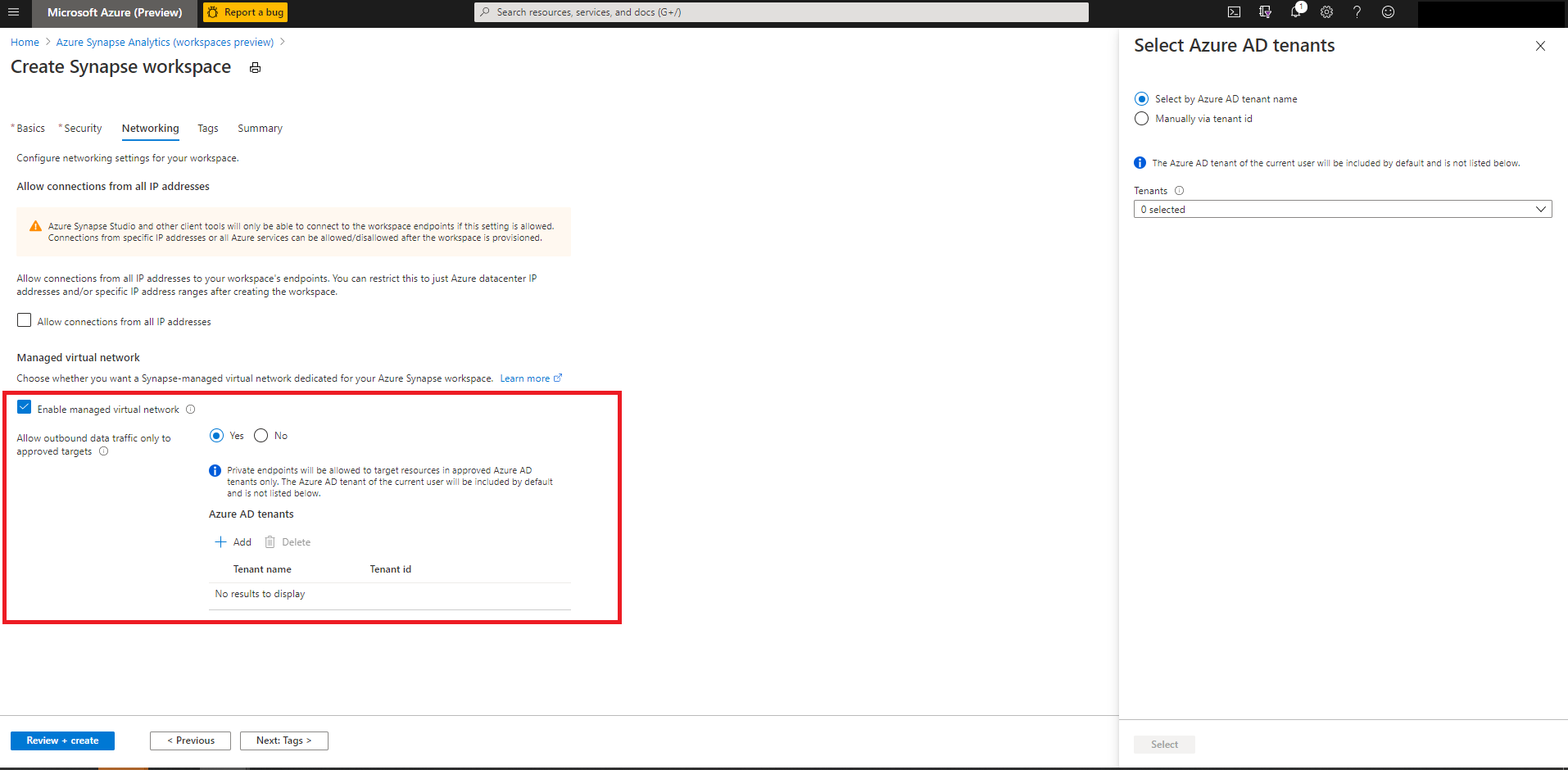
Add data exfiltration protection when creating your workspace
- On the Networking tab, select the “Enable managed virtual network” checkbox.
- Select “Yes” for the “Allow outbound data traffic only to approved targets” option.
- Choose the approved Microsoft Entra tenants for this workspace.
- Review the configuration and create the workspace.
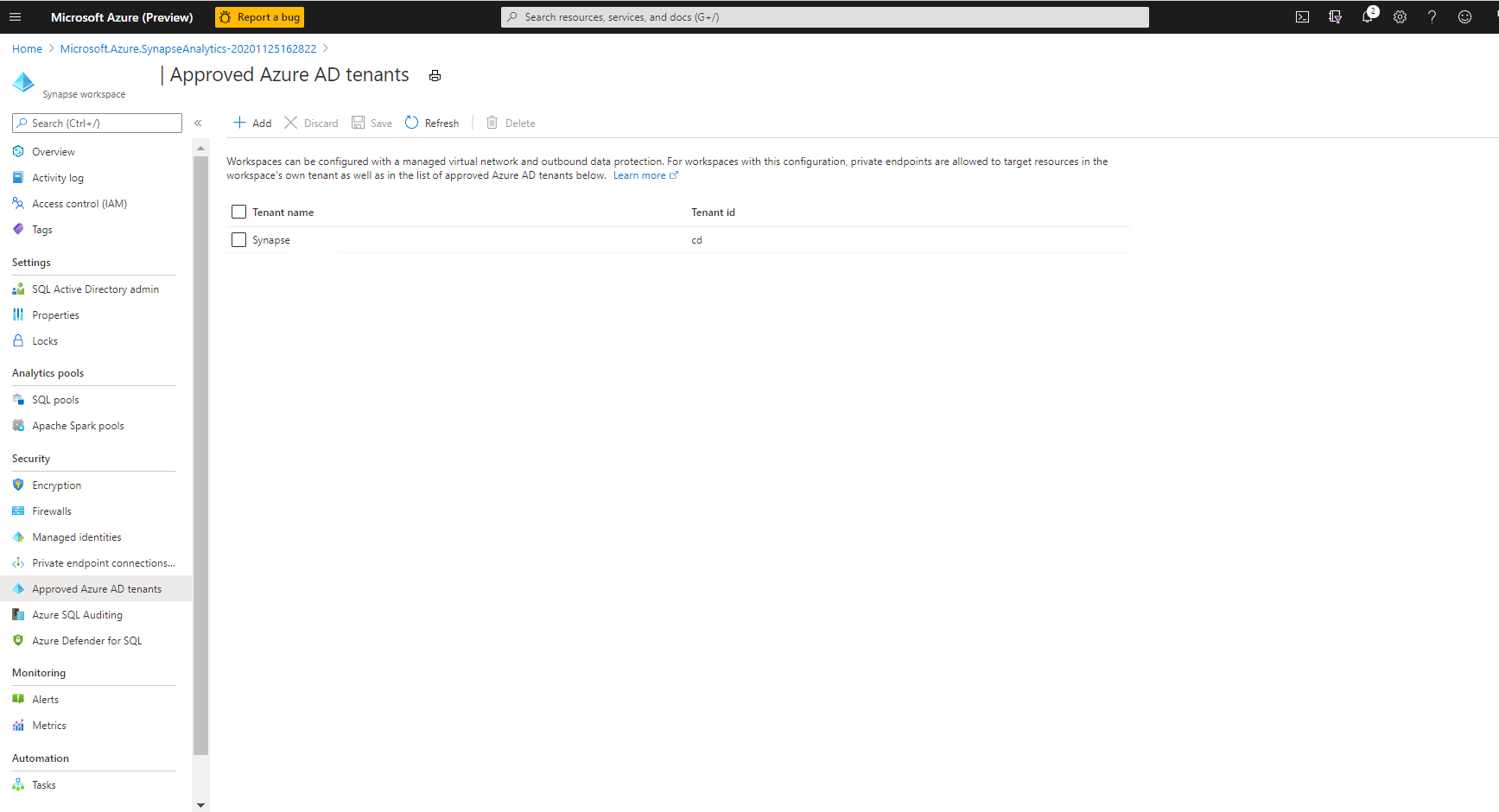
Manage approved Microsoft Entra tenants for the workspace
- From the workspace’s Azure portal, navigate to “Approved Microsoft Entra tenants”. The list of approved Microsoft Entra tenants for the workspace will be listed here. The workspace’s tenant is included by default and is not listed.
- Use “+Add” to include new tenants to the approved list.
- To remove a Microsoft Entra tenant from the approved list, select the tenant and select on “Delete” and then “Save”.
Connecting to Azure resources in approved Microsoft Entra tenants
You can create managed private endpoints to connect to Azure resources that reside in Microsoft Entra tenants, which are approved for a workspace. Follow the steps listed in the guide for creating managed private endpoints.
Important
Resources in tenants other than the workspace's tenant must not have blocking firewall rules in place for the SQL pools to connect to them. Resources within the workspace’s managed virtual network, such as Spark clusters, can connect over managed private links to firewall-protected resources.
Known limitations
Users can provide an environment configuration file to install Python packages from public repositories like PyPI. In data exfiltration protected workspaces, connections to outbound repositories are blocked. As a result, Python libraries installed from public repositories like PyPI are not supported.
As an alternative, users can upload workspace packages or create a private channel within their primary Azure Data Lake Storage account. For more information, visit Package management in Azure Synapse Analytics
Ingesting data from an Event Hub into Data Explorer pools will not work if your Synapse workspace uses a managed virtual network with data exfiltration protection enabled.
Next steps
- Learn more about data exfiltration protection in Synapse workspaces
- Learn more about Managed workspace Virtual Network
- Learn more about Managed private endpoints
- Create Managed private endpoints to your data sources
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for