Examine Microsoft's strategy for Zero Trust networking
Big data presents new opportunities to derive new insights and gain a competitive edge. Industries are moving away from an era where networks were clearly defined and specific to a certain location. The cloud, mobile devices, and other endpoints expand the boundaries and change the paradigm. Now there isn't necessarily a contained/defined network to secure. Instead, there's a vast portfolio of devices and networks, all linked by the cloud.
Instead of believing everything behind the corporate firewall is safe, an end-to-end Zero Trust strategy assumes breaches are inevitable. That means you must verify each request as if it originates from an uncontrolled network. As such, identity management plays a crucial role in this new paradigm.
In the Zero Trust model, there are three key objectives when it comes to securing your networks:
- Be ready to handle attacks before they happen.
- Minimize the extent of the damage and how fast it spreads.
- Increase the difficulty of compromising your cloud footprint.
To achieve these objectives, organizations must follow these Zero Trust principles:
- Verify explicitly. Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least-privileged access. Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection to protect both data and productivity.
- Assume breach. Minimize blast radius for breaches and prevent lateral movement by segmenting access by network, user, devices, and application awareness. Verify all sessions are encrypted end to end. Use analytics to get visibility, drive threat detection, and improve defenses.
Building Zero Trust networks with Microsoft 365
The traditional perimeter-based network defense is obsolete. Perimeter-based networks operate on the assumption that all systems within a network can be trusted. However, today’s increasingly mobile workforce, the migration towards public cloud services, and the adoption of Bring Your Own Device (BYOD) model make perimeter security controls irrelevant. Networks that fail to evolve from traditional defenses are vulnerable to breaches: an attacker can compromise a single endpoint within the trusted boundary and then quickly expand foothold across the entire network.
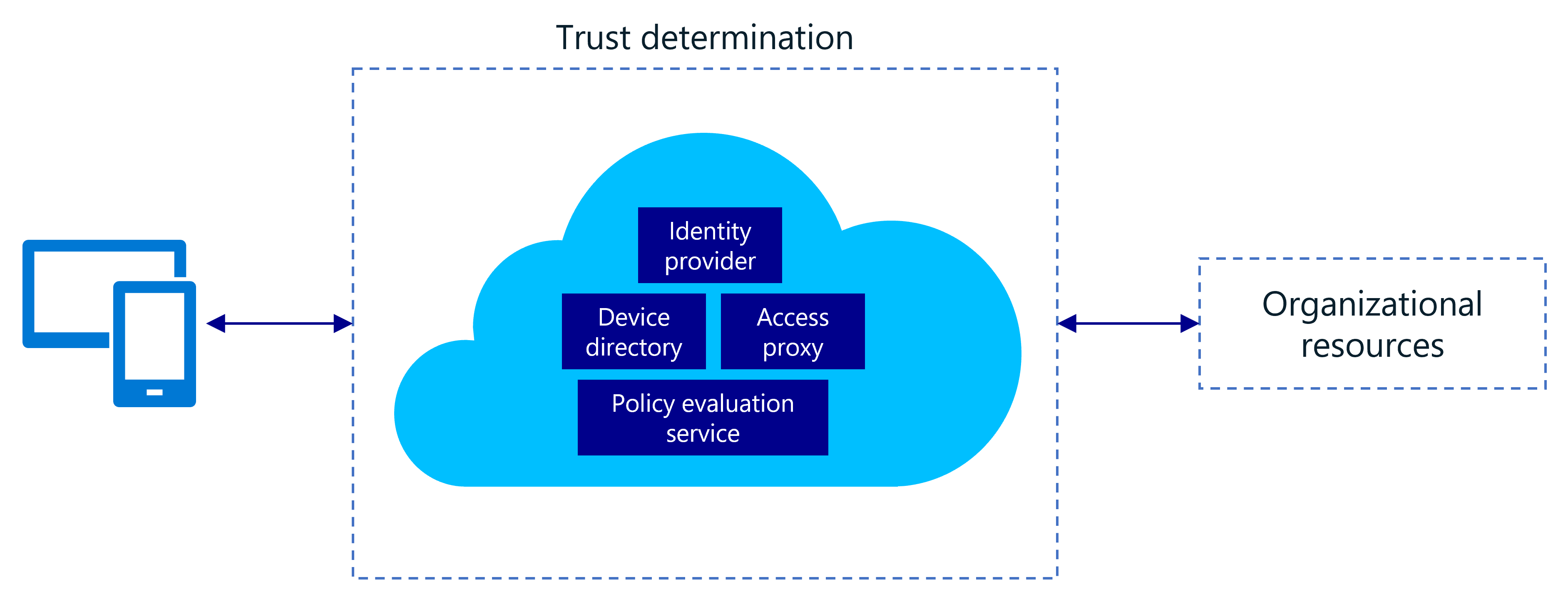
Zero Trust networks eliminate the concept of trust based on network location within a perimeter. Instead, Zero Trust architectures use device and user trust claims to gate access to organizational data and resources. A general Zero Trust network model typically comprises the following signals:
- Identity provider. Keeps track of users and user-related information.
- Device directory. Maintains a list of devices that have access to corporate resources, along with their corresponding device information (for example, type of device, integrity, and so on).
- Policy evaluation service. Determines if a user or device conforms to the policy set forth by security admins.
- Access proxy. Utilizes the prior signals to grant or deny access to an organizational resource.
Gating access to resources using dynamic trust decisions allows an enterprise to enable access to certain assets from any device while restricting access to high-value assets on enterprise-managed and compliant devices. In targeted and data breach attacks, attackers can compromise a single device within an organization, and then use the “hopping” method to move laterally across the network using stolen credentials. A solution based on Zero Trust network, configured with the right policies around user and device trust, can help prevent stolen network credentials from being used to gain access to a network.
Zero Trust is the next evolution in network security. The state of cyberattacks drives organizations to take the “assume breach” mindset, but this approach shouldn't be limiting. Zero Trust networks protect corporate data and resources while ensuring that organizations can build a modern workplace using technologies that empower employees to be productive anytime, anywhere, any which way.
Network Zero Trust deployment objectives
Before most organizations start their Zero Trust journey, they have network security that is characterized by the following features:
- Few network security perimeters and open, flat networks.
- Minimal threat protection and static traffic filtering.
- Unencrypted internal traffic.
When implementing an end-to-end Zero Trust framework for securing networks, it's recommended that organizations focus first on these initial deployment objectives:
- Network segmentation: Many ingress/egress cloud micro-perimeters with some micro-segmentation.
- Threat protection: Cloud native filtering and protection for known threats.
- Encryption: User-to-app internal traffic is encrypted.
After these initial objectives are achieved, organizations should then focus on the following deployment objectives:
- Network segmentation: Fully distributed ingress/egress cloud micro-perimeters and deeper micro-segmentation.
- Threat protection: Machine learning-based threat protection and filtering with context-based signals.
- Encryption: All traffic is encrypted.
Zero Trust networking based on Microsoft Entra Conditional Access
Today, employees access their organization’s resources from anywhere using various devices and apps. Access control policies that focus only on who can access a resource isn't sufficient. To achieve balance between security and productivity, security admins also need to factor in how a resource is being accessed.
Microsoft Entra Conditional Access is the foundational building block of how customers can implement a Zero Trust network approach. Conditional access and Microsoft Entra ID Protection make dynamic access control decisions based on user, device, location, and session risk for every resource request. They combine:
- Attested runtime signals about the security state of a Windows device.
- The trustworthiness of the user session and identity to arrive at the strongest possible security posture.
Conditional access provides a set of policies that can be configured to control the circumstances in which users can access corporate resources. Considerations for access include user role, group membership, device health and compliance, mobile applications, location, and sign-in risk. These considerations are used to decide whether to allow access, deny access, or control access with other authentication challenges (for example, multifactor authentication), Terms of Use, or access restrictions. Conditional access works robustly with any application configured for access with Microsoft Entra ID.
Knowledge check
Choose the best response for the following question. Then select “Check your answers.”